Python
Dev
419

Image Credit: Dev
Advanced Array Manipulation Techniques in Python
- Advanced Array Manipulation Techniques in Python without using built-in functions or shortcuts like reversed() or slicing.
- Problem One: Reversing an array in-place using two pointers and swapping values until fully reversed.
- Code snippet provided for reversing an array in-place.
- Problem Two: Rotating an array anti-clockwise by k steps with detailed breakdown and code snippet for in-place rotation.
Read Full Article
25 Likes
PlanetPython
184

Zato Blog: Using Oracle Database from Python and Zato Services
- Oracle Database is a vital component of enterprise IT, and integrating it with Python offers automation, reporting, and API capabilities.
- Connecting to Oracle Database from Python enables tasks such as automating business processes and running analytics.
- Zato services allow for easy integration with Oracle Database, with SQL connections configured in the Dashboard.
- Service logic in Zato is organized into dedicated services, enhancing clarity, reusability, and maintainability.
- SQL objects like tables and stored procedures are fundamental in leveraging Oracle Database within Python and Zato services.
- Examples provided in the article demonstrate querying users, calling stored procedures with input/output parameters, and handling multiple rows.
- Parameterized queries are highlighted as a best practice to prevent SQL injection and maintain code clarity.
- Key concepts such as connection management, calling procedures, and service separation are explained for effective Oracle Database usage.
- Security and best practices emphasize using parameterized queries, secure credential management, error handling, and connection pooling.
- Overall, integrating Oracle Database with Python and Zato services empowers users to build APIs, automate processes, and connect enterprise data sources securely and efficiently.
Read Full Article
11 Likes
Dev
1.2k

Image Credit: Dev
How to Scrape Amazon Influencer Links Using Python?
- Web scraping Amazon influencer links can be complicated due to dynamic content like SiteStripe banners on product pages.
- Challenges include missing elements due to JavaScript rendering and discrepancies in scraped HTML based on session and cookies.
- To effectively scrape Amazon influencer links, ensure proper authentication and session handling.
- Consider using tools like Selenium to handle dynamically loaded content for accurate data extraction.
Read Full Article
24 Likes
Dev
99

Image Credit: Dev
How to Fix PydanticSchemaGenerationError with Nested DefaultDict in Python?
- The PydanticSchemaGenerationError can occur due to nested defaultdict types in Pydantic models.
- Pydantic struggles with inferring default factories for complex types like nested defaultdict with dictionary keys not among the supported types.
- To resolve this, you need to set explicit default factories for each level of the nested defaultdict in your Pydantic model.
- By following the step-by-step solution provided, you can update your Pydantic model with proper default factories and test the implementation to avoid the schema generation error in Python.
Read Full Article
5 Likes
Discover more
Dev
63

Image Credit: Dev
What Are Today’s Top Movie Plots? I Wrote a Python Scraper to Find Out
- A Python scraper was built to analyze the plots of today's top movies by pulling data from IMDb.
- The script gathers plot summaries of the top 25 movies, creates word clouds to visualize common themes, and offers insights into popular genres.
- Skills acquired include data cleaning with NLTK, web scraping using requests and BeautifulSoup, and data visualization with WordCloud and matplotlib.
- The project also focused on handling website quirks, avoiding anti-bot measures, and being considerate by using time.sleep() to avoid overloading IMDb's servers.
Read Full Article
3 Likes
Dev
216

Image Credit: Dev
Learning Python by Teaching Your Computer to Be Petty and Petty Good at It
- Learn Python by creating a program that tracks and shames you for overusing certain apps like Slack, YouTube, Steam, etc.
- The program involves file handling, scheduling tasks, conditional logic, and notifications, providing practical Python script-building experience.
- Using the psutil library, the script monitors the activity of specific programs and updates a count in a JSON file.
- It includes a feature to issue humorous notifications when app usage crosses a certain threshold.
- The script can be scheduled to run automatically using the 'schedule' module in Python.
- The project highlights tracking app usage, creating persistent counters, and using humor to aid learning.
- The article suggests exploring more Python projects, setting usage limits, building dashboards, and integrating with APIs like Twitter.
- Learning through practical, humorous projects can help solidify Python skills and solve real-world problems in creative ways.
- The article also mentions resources for Python developers and encourages building projects that align with personal interests.
- The final message is to keep learning, coding, and exploring unique Python projects that combine humor and productivity.
- The author shares insights on using Python to build tools that encourage productivity in a playful manner.
Read Full Article
13 Likes
Medium
157

Image Credit: Medium
Building a Real-Time API Token Leak Detection and Response System Using Python
- API tokens are at risk of exposure through application logs, browser consoles, source code repositories, and error monitoring tools.
- Building a real-time API token leak detection and response system involves scanning log streams, detecting tokens using regex and ML scoring, sending alerts, auto-revoking leaked tokens, maintaining a dashboard, and sending events to various platforms.
- The system can be integrated with Slack, Microsoft Teams, SIEM platforms, and other tools for monitoring and responding to token leaks promptly.
- Implementing this system using Python can enhance security practices and help in safeguarding organizations against financial and reputational damage from data leaks.
Read Full Article
9 Likes
Medium
37

Image Credit: Medium
7 Confusing Python Code Snippets (And Why They Make Sense)
- Python code snippets that may seem confusing at first glance are actually features.
- Exploring 7 mind-bending Python snippets that challenge the understanding of developers.
- One example involves tuple unpacking where a seemingly strange line of code actually works as intended.
- The article delves into how Python interprets code snippets that appear buggy but have logical explanations.
Read Full Article
2 Likes
Dev
288

Image Credit: Dev
How Does GenerateCode.dev Work? A Python Example
- GenerateCode.dev is a platform that assists developers in effortlessly generating code snippets.
- It utilizes advanced algorithms and artificial intelligence to streamline the code generation process.
- Developers can make API requests to GenerateCode.dev to receive Python code samples by following a simple process.
- Using GenerateCode.dev saves time, enhances learning, and encourages experimentation in coding.
Read Full Article
17 Likes
Medium
148

Image Credit: Medium
5 Free Resources to Learn Python
- Python is a beginner-friendly language with various applications in software engineering like web development and AI.
- Learning Python can be empowering and life-changing, offering the ability to create a desired lifestyle.
- Several free resources exist for learning Python without expensive courses or bootcamps.
- Harvard’s CS50 Intro to Python course contains modules with lecture transcripts, notes, and problem sets.
- Google’s Python class includes guides, video lectures, and coding exercises for mastering Python basics.
- Automate the Boring Stuff with Python, an online book, teaches coding basics and automation projects in Python.
- Al Sweigart's resources and the official Python documentation tutorial are recommended for learning.
- YouTube offers tutorials and courses for learning Python, such as Corey Schafer's videos.
- Practicing coding exercises independently is crucial for solidifying Python programming skills.
- Continuous practice and project-building are key to mastering Python and becoming a proficient programmer.
Read Full Article
8 Likes
Dev
365

Image Credit: Dev
Most Overpowered Python Scripts You’ve Never Heard Of
- The article unveils hidden Python scripts that deviate from conventional usage, including black-hat scraping, AI thought scaffolding, and game-playing bots trained through reinforcement learning.
- Scripts automate tasks like scraping data with stealth and using GPT classifiers for analysis, often earning freelancers substantial income by selling market trend data.
- Some developers leverage Python not just for AI implementation but as a 'thought engine' for idea breakdown and strategic planning, enhancing creativity and problem-solving.
- Certain Python scripts enable gameplay automation, with bots learning to excel in various systems beyond gaming, such as e-commerce, social media, and trading platforms.
- Python bots automate lucrative tasks like domain flipping, NFT reselling, and crypto arbitrage, emphasizing the potential for passive income generation but also the risks involved.
- Python developers craft compact yet powerful applications mimicking full SaaS platforms, demonstrating the language's transformative potential in simplifying complex functionalities.
- The article emphasizes Python's evolution into a versatile tool capable of simulating conversations, extracting profits, self-improving, and even replacing entire startups with minimal code.
- It encourages readers to explore and experiment with these innovative script ideas to solve problems creatively, with Python acting as a catalyst for impactful change.
- Additionally, the article recommends intriguing courses on computing, tech history, and programming esoterica for those eager to delve deeper into the tech realm.
- Lastly, a featured GitHub database offers over 7,000 projects for AI tools, startup launch ideas, and product inspiration, providing a wealth of opportunities for tech enthusiasts.
- The content spans underground Python script revelations, unconventional AI utilization, and novel approaches to automation for diverse applications, showcasing Python's robust versatility.
Read Full Article
22 Likes
Hackingblogs
13
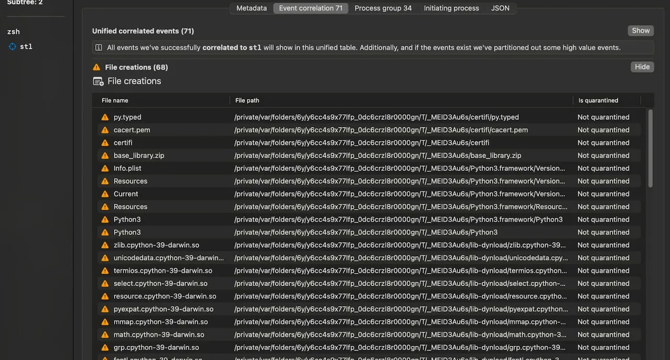
Image Credit: Hackingblogs
MacOS Malware Alert: Python-Based Infostealer Bundled via PyInstaller
- Researchers at Jamf Threat Labs discovered a MacOS malware using PyInstaller to distribute infostealer malicious software meant to steal confidential data.
- The malware prompts users for their password through an AppleScript dialog and communicates with suspicious domains like 'connect' patterned sites.
- PyInstaller is a tool for converting Python scripts into standalone executables that include all necessary components without requiring Python installation.
- Static analysis revealed the ad-hoc signing, architecture support for Intel and Apple Silicon Macs, and the use of PyInstaller in the malware file.
- Dynamic analysis using Mac Monitor exposed malicious activities like password prompts, volume reduction, Python script unpacking, and private information gathering.
- The malware's capabilities include password theft, AppleScript execution, Keychain credential extraction, and cryptocurrency wallet information theft.
- Attackers are increasingly using PyInstaller to cloak malware, as evidenced by the growing prevalence of infostealers on MacOS.
- Indicators of Compromise (IOCs) for the MacOS malware include filenames like stl, stl-deobf.py, installer, and sosorry, along with contacted domains.
Read Full Article
Like
Dev
293

Image Credit: Dev
DIY Python Web Scraping Tool: Proxy IP Management and Optimization Tips
- Web scraping is a powerful technique for gathering data from websites, with challenges in managing proxy IPs.
- Using proxies is essential to avoid IP bans, access geolocation-restricted content, and provide anonymity.
- Setting up a DIY Python web scraping tool involves installing necessary libraries and defining proxies in requests.
- Best practices include rotating proxies, testing proxy health, using proxy services like IP2World, rate limiting, and error handling.
Read Full Article
17 Likes
Medium
370

Image Credit: Medium
Using Python to Extract Text from Audio
- Python provides various libraries for audio processing, including pydub, librosa, wave, and soundfile.
- The SpeechRecognition library is commonly used for converting speech to text in Python, supporting multiple backends.
- Vosk is a lightweight speech recognition engine that works offline and supports WAV, MP3, and FLAC audio formats.
- Vosk can run on different platforms without requiring GPU acceleration, making it suitable for devices like laptops, Raspberry Pi, and mobile devices.
Read Full Article
22 Likes
Dev
420

Image Credit: Dev
How to Write Python Code Compatible with Both Python 2 and 3?
- When working on a project that requires compatibility with both Python 2 and Python 3, understanding key differences is crucial.
- Common compatibility issues include differences in print statements, integer division, string handling, module imports, and dictionary iteration.
- Best practices for compatibility include using future imports, utilizing the six library, leveraging compatibility libraries, and regular testing.
- Tools like futurize, modernize, and continuous integration services can assist in identifying and resolving compatibility issues.
Read Full Article
25 Likes
For uninterrupted reading, download the app