Hackingblogs
1M
13
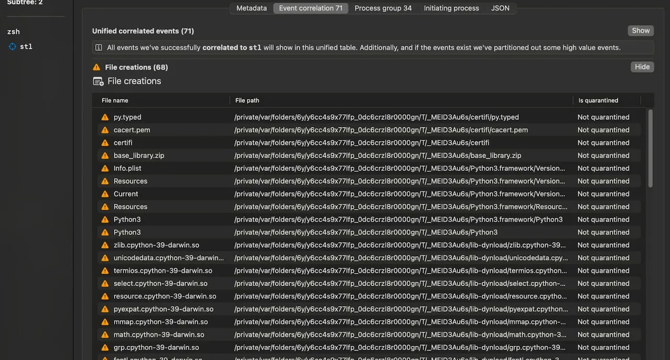
Image Credit: Hackingblogs
MacOS Malware Alert: Python-Based Infostealer Bundled via PyInstaller
- Researchers at Jamf Threat Labs discovered a MacOS malware using PyInstaller to distribute infostealer malicious software meant to steal confidential data.
- The malware prompts users for their password through an AppleScript dialog and communicates with suspicious domains like 'connect' patterned sites.
- PyInstaller is a tool for converting Python scripts into standalone executables that include all necessary components without requiring Python installation.
- Static analysis revealed the ad-hoc signing, architecture support for Intel and Apple Silicon Macs, and the use of PyInstaller in the malware file.
- Dynamic analysis using Mac Monitor exposed malicious activities like password prompts, volume reduction, Python script unpacking, and private information gathering.
- The malware's capabilities include password theft, AppleScript execution, Keychain credential extraction, and cryptocurrency wallet information theft.
- Attackers are increasingly using PyInstaller to cloak malware, as evidenced by the growing prevalence of infostealers on MacOS.
- Indicators of Compromise (IOCs) for the MacOS malware include filenames like stl, stl-deobf.py, installer, and sosorry, along with contacted domains.
Read Full Article
Like
For uninterrupted reading, download the app