Hackernoon
1M
163
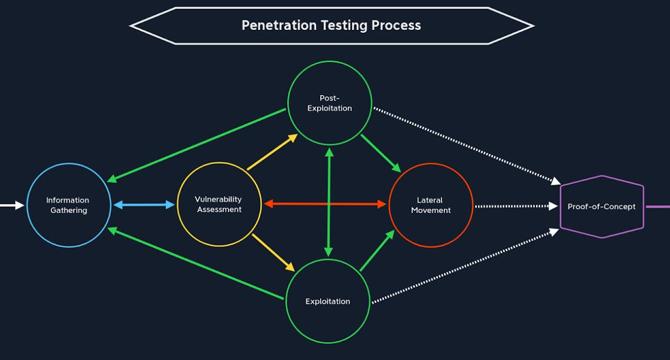
Image Credit: Hackernoon
Breaking Into a Server Using a Hello World Page and a Fake JPEG
- The article discusses the stages of the Penetration Testing Process and their application in practical labs.
- It covers Pre-Engagement, Information Gathering, Vulnerability Assessment, Exploitation, Post-Exploitation, and Lateral Movement stages.
- Post-Engagement includes system cleanup after exploitation to ensure systems are not left vulnerable.
- The article delves into applying the Penetration Testing stages on a real vulnerable machine, showcasing the practical implementation.
- Using tools like Nmap, the Information Gathering stage reveals details about open ports and services like SSH.
- Exploitation techniques like IP Rotation Spoofing are discussed to bypass security measures like IP-dependent anti-brute-force protection.
- The article describes methods to upload malicious PHP code via a vulnerable plugin, bypassing file type restrictions on the web server.
- It explores different shell types like Web Shell, Reverse Shell, and Bind Shell, highlighting their advantages and limitations.
- Steps for escalating privileges to gain Root access are outlined, including leveraging sudo privileges without a password.
- The article concludes by emphasizing the importance of addressing minor misconfigurations to prevent complete system compromise, exemplified in the HTB Nibbles scenario.
Read Full Article
9 Likes
For uninterrupted reading, download the app