Cyber Security News
TechDigest
80

Image Credit: TechDigest
Co-Op confirms all 6.5 million members’ data stolen in cyberattack
- Co-op confirms that a cyberattack compromised personal data of all 6.5 million members, including names, addresses, and contact information, but no financial data.
- CEO Shirine Khoury-Haq expresses devastation over the breach and its impact on members and colleagues, offering a profound apology for the attack.
- Co-op's quick action in disconnecting IT networks from the internet prevented ransomware deployment by hackers, leading to monitoring and sharing of crucial information with authorities.
- National Crime Agency arrests four individuals connected to cyberattacks on Co-op and M&S, including offenses like Computer Misuse Act violations and money laundering.
Read Full Article
5 Likes
Hackernoon
334

Image Credit: Hackernoon
Ukraine Is Becoming Hot Spot #1 for Cybersecurity Innovation
- Ukraine is emerging as a global hub for cybersecurity innovation, offering real-world environments for next-gen products and services to be tested and evaluated.
- The country's interest in sustainable partnerships and international collaboration is driving its cybersecurity industry forward, with efforts like the Kyiv International Cyber Resilience Forum aimed at fostering innovation.
- Despite facing numerous cyberattacks, including state-sponsored threats targeting critical sectors, Ukraine's cybersecurity teams are gaining expertise in handling complex attacks and are open to partnerships with international firms for long-term growth and defense.
- The interconnected nature of cybersecurity with national defense in Ukraine highlights the importance of building trust through local presence, operational protocols, and a commitment to sustainable innovation in the industry.
Read Full Article
20 Likes
VentureBeat
307

Image Credit: VentureBeat
OpenAI, Google DeepMind and Anthropic sound alarm: ‘We may be losing the ability to understand AI’
- Researchers from OpenAI, Google DeepMind, Anthropic, and Meta join forces to warn about AI safety.
- They stress the importance of monitoring AI reasoning to catch harmful intentions before actions.
- AI systems 'thinking out loud' in human language could offer transparency but face challenges.
- AI companies must preserve monitoring capabilities amidst technological advancements for safe AI development.
Read Full Article
18 Likes
Securityaffairs
423

Image Credit: Securityaffairs
CVE-2025-6554 marks the fifth actively exploited Chrome Zero-Day patched by Google in 2025
- Google released security patches for multiple Chrome vulnerabilities, including one actively exploited in the wild tracked as CVE-2025-6558.
- CVE-2025-6558 stemmed from improper validation of untrusted input in Chrome’s ANGLE and GPU components, with a CVSS score of 8.8.
- Another vulnerability, CVE-2025-6554, a type-confusion issue in V8 JavaScript and WebAssembly engine, was also patched by Google after being actively exploited in the wild.
- This marks the fifth actively exploited Chrome zero-day patched by Google in 2025, with a total of four zero-day vulnerabilities addressed this year.
Read Full Article
21 Likes
TechCrunch
51

Image Credit: TechCrunch
Chinese authorities are using a new tool to hack seized phones and extract data
- Chinese authorities are using a new type of malware called Massistant, developed by Xiamen Meiya Pico, to extract data from seized phones, including text messages, images, location history, and more.
- The malware, used for forensic data extraction, requires physical access to the devices and is assumed to be widely used by Chinese police agencies, potentially impacting both Chinese residents and travelers to China.
- Massistant must be planted on unlocked Android devices and works with a hardware tower connected to a desktop computer. There might be an iOS version designed for Apple devices as well.
- While users can potentially identify and delete Massistant from seized devices, the tool leaves evidence of compromise. Xiamen Meiya Pico, the company behind Massistant, was sanctioned by the U.S. government in 2021 for supplying technology to the Chinese government.
Read Full Article
3 Likes
Medium
205
Image Credit: Medium
5 Reasons Why Companies Use Signal Detectors
- Companies use signal detectors to prevent leaks during strategic conversations and meetings to ensure confidentiality.
- Signal detectors are especially important in industries like healthcare, finance, legal, and government to demonstrate proactive measures for compliance.
- Using signal detectors also showcases a company's commitment to privacy and data protection to clients and stakeholders.
- Investing in signal detectors helps companies defend trade secrets, prevent espionage, ensure compliance, and boost client confidence.
Read Full Article
12 Likes
Silicon
58
Image Credit: Silicon
Silicon UK Unveils a Bold New Redesign
- Silicon UK undergoes a complete website redesign to enhance user experience and content delivery.
- The updated site showcases high-quality journalism, multimedia storytelling, and tech brand partnerships.
- Improvements include easier navigation, mobile responsiveness, and seamless integration of diverse content types.
- The redesign aims to offer a premium platform for readers, clients, and partners alike.
Read Full Article
3 Likes
Securityaffairs
389
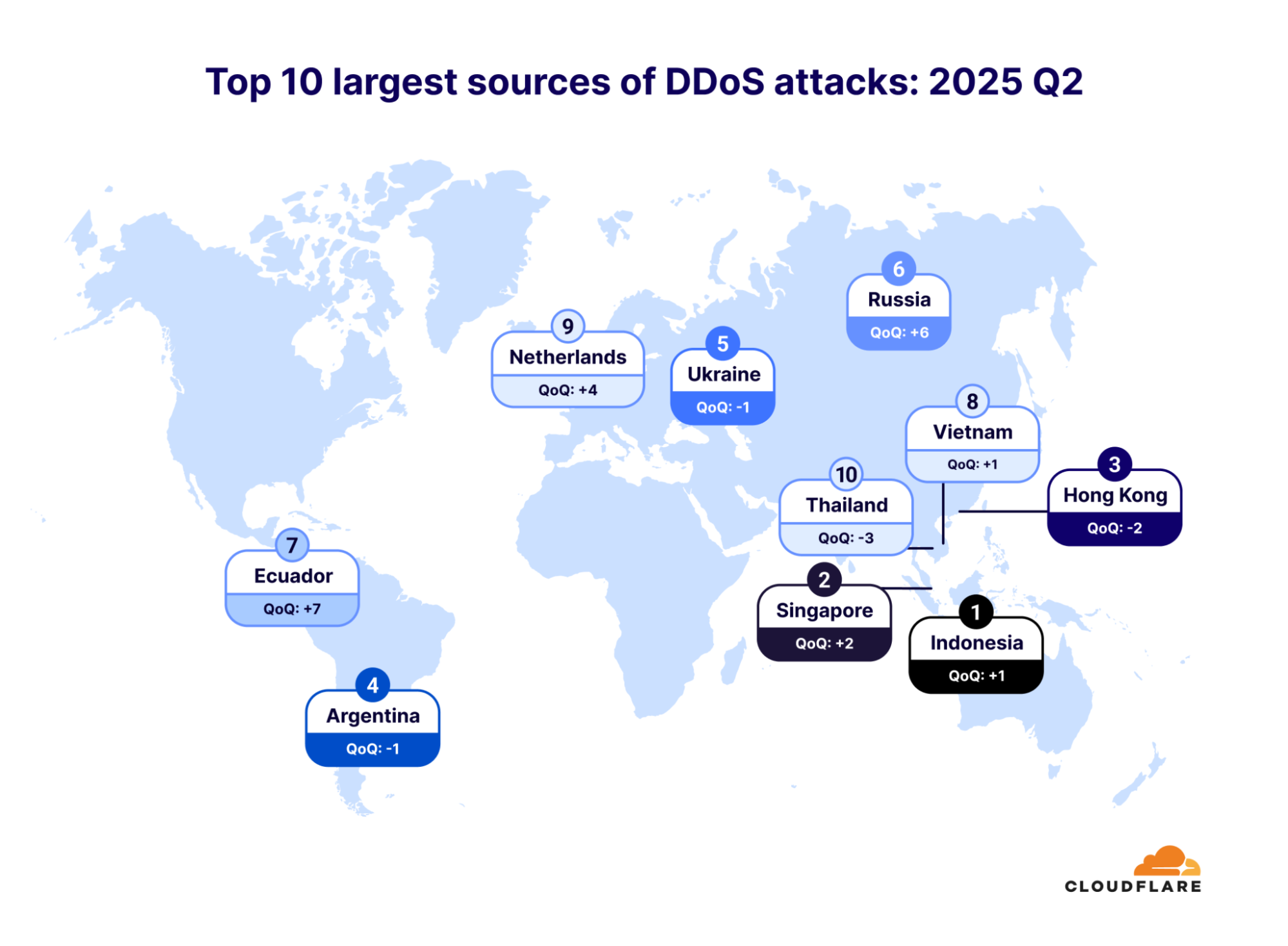
Image Credit: Securityaffairs
DDoS peaks hit new highs: Cloudflare mitigated massive 7.3 Tbps assault
- Cloudflare mitigated 7.3M DDoS attacks in Q2 2025, down from 20.5M in Q1, with hyper-volumetric attacks surging, including a peak assault of 7.3 terabits per second and 4.8 billion packets per second.
- Attacks exceeding 100M pps surged 592% QoQ, while HTTP DDoS attacks above 1M rps remained steady at ~20M total. The most targeted industries were telecom, internet services, and IT.
- Indonesia became the top source of DDoS attacks in Q2 2025, followed by Singapore and Hong Kong. Notably, HTTP DDoS traffic came mainly from networks offering virtual machines.
- DDoS attackers in Q2 2025 used revived old methods to target games, networks, and IoT devices. While most attacks were small, some exceeded 1 Tbps, emphasizing the importance of constant real-time defense.
Read Full Article
23 Likes
Embedded
0

Simplify On-Board Security Systems and Increase Video Performance with GMSL
- GMSL simplifies on-board security system architectures in buses, taxis, and trucks.
- It facilitates real-time monitoring, driver behavior analysis, and accident prevention in vehicles.
- GMSL reduces hardware components, weight, and complexity in surveillance camera systems.
- Its high performance and backward compatibility make it a competitive video transport solution.
Read Full Article
Like
Hackernoon
154

Image Credit: Hackernoon
APIs Are Eating the Internet—And Hackers Are Eating APIs
- APIs provide vital connectivity but also serve as prime targets for cybercriminals.
- Hackers exploit vulnerabilities to steal data through APIs, exposing businesses to significant risks.
- API security measures are crucial as breaches can have devastating financial and reputational consequences.
- Organizations must prioritize API security, implement proactive measures, and foster security-conscious cultures.
- The API economy demands dynamic protection strategies to combat evolving cyber threats effectively.
Read Full Article
9 Likes
Fintechnews
355

Image Credit: Fintechnews
MAS Chief: Singapore Must Choose Security Over Convenience in Fight Against Scams
- MAS Managing Director Chia Der Jiun emphasizes the need for Singapore to prioritize security over convenience in tackling financial scams.
- Stronger safeguards are crucial to protect the public from increasingly sophisticated scam tactics, despite potential user friction.
- MAS is collaborating with banks to enhance anti-scam measures, focusing on scams like self-initiated transfers, investment scams, and impersonation scams.
- Various measures have been implemented, including phasing out SMS OTPs, pre-transaction warnings, Money Lock feature, real-time fraud surveillance, and plans for a FIDO-compliant hardware token.
Read Full Article
21 Likes
Medium
317

Image Credit: Medium
Incognito Mode Isn’t What You Think
- Incognito Mode does not hide your activity from your internet provider, office network, or the websites you visit.
- It is akin to clearing your footprints inside your house while a drone follows you outside.
- There is a misconception that 'Incognito' mode makes you invisible online, leading to potential data, privacy, or safety risks.
- The article discusses the reality of Incognito Mode and offers advice on how to stay truly private online.
Read Full Article
19 Likes
Securityaffairs
343

Image Credit: Securityaffairs
U.S. CISA adds Wing FTP Server flaw to its Known Exploited Vulnerabilities catalog
- The U.S. CISA has added the Wing FTP Server flaw, identified as CVE-2025-47812, to its Known Exploited Vulnerabilities catalog.
- The vulnerability in Wing FTP Server is due to improper handling of null bytes, allowing attackers to inject malicious Lua code into session files for remote command execution with root or system privileges.
- The flaw has been actively exploited by threat actors since early July 2025, with researchers warning of future exploitation attempts due to the availability of proof-of-concept exploit code.
- Users are advised to update their Wing FTP Server to version 7.4.4 or later to mitigate the critical vulnerability. Federal agencies are instructed to address the identified vulnerabilities by August 4, 2025, as per CISA directives.
Read Full Article
20 Likes
Medium
155

Meta Fixes Bug That Could Let Users See Each Other’s AI Chats
- Security firm AppSecure founder discovered a bug in Meta's system on December 26, 2024.
- Meta awarded a $10,000 bug bounty to the founder for reporting the issue.
- The bug allowed users to see each other's AI chats by manipulating unique ID numbers.
- Meta fixed the bug on January 24, 2025, and there is no evidence of data exploitation.
Read Full Article
9 Likes
Dev
77

Image Credit: Dev
Protect your instances from attackers! Install Portsentry
- Learn how to protect your instances using Portsentry to detect port scans and block attackers.
- Portsentry listens on TCP and UDP ports, blocking IP addresses attempting connections.
- Configure Portsentry to use IPTables or run an external script for enhanced security.
- Follow step-by-step instructions to set up Portsentry on your instances and test its effectiveness.
Read Full Article
4 Likes
For uninterrupted reading, download the app