VentureBeat
1M
233
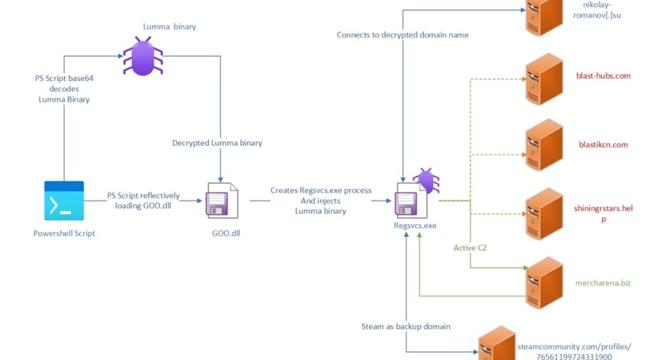
Image Credit: VentureBeat
Demystifying Myth Stealer: An ‘InfoStealer’ that targeted video games | Trellix
- Trellix's Advanced Research Center discovered a fully undetected infostealer malware called Myth Stealer targeting games, written in Rust code and marketed on Telegram.
- Infostealers infiltrate systems to collect passwords, cookies, credit card info, and more from browsers, setting apart Myth Stealer with its Rust code written in a less common language.
- Using Rust gives Myth Stealer wider platform support for the malware's execution, potentially increasing the exposure for victim organizations.
- Myth Stealer was promoted on Telegram with advanced features appealing to cybercriminals, initially offered for free trial and later shifted to a subscription model.
- The malware is distributed through fraudulent gaming websites, targeting browsers like Gecko and Chromium, extracting sensitive data and utilizing anti-analysis techniques.
- Myth Stealer's authors update the code frequently to avoid antivirus detection, adding features like screen capture and clipboard hijacking.
- The malware is now offered on a subscription basis through cryptocurrency and Razer Gold, with a separate channel for testimonials and compromised account sales being shut down by Telegram.
- Myth Stealer was distributed disguised as game-related software on fraudulent gaming websites, and as a crack for game cheating software in online forums.
- The malware evolved from stealing data in free versions to subscription-based with additional functionalities like fake windows, screenshots, and clipboard hijacking.
- Myth Stealer's consistent updates and enhancements, like string obfuscation and fake windows, challenge endpoint security solutions to detect it, posing a persistent risk to users.
Read Full Article
14 Likes
For uninterrupted reading, download the app