Medium
1M
238
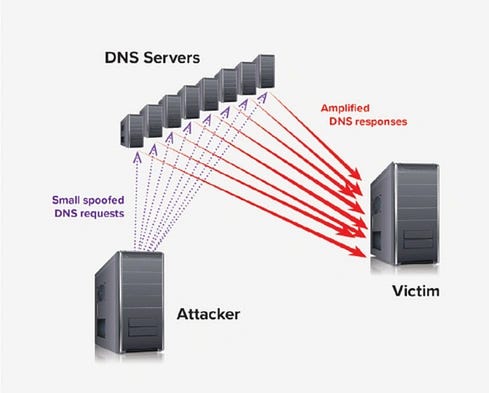
Image Credit: Medium
DNS Cache Poisoning: The Invisible Hacker in the Network
- DNS Cache Poisoning, also known as DNS Spoofing, poses a threat by manipulating trust and redirecting users to malicious servers.
- DNS serves as the internet's phonebook, translating domain names to IP addresses and caching responses for efficiency.
- DNS Cache Poisoning involves injecting false DNS records to reroute users to fake sites.
- Attackers exploit vulnerabilities in the DNS caching mechanism to execute poisoning attacks.
- Key concepts involved include guessing transaction IDs, predictable source ports, and race conditions.
- Attack tools like dsniff, Ettercap, and dnsspoof are commonly used for DNS poisoning.
- Real-world incidents in Iran and China have showcased the impact of DNS spoofing on redirecting users and censoring content.
- Defense mechanisms against DNS Cache Poisoning include DNSSEC, randomizing source ports, encrypted DNS protocols, and hardened recursive resolvers.
- The future of DNS security faces challenges despite advancements like DNSSEC and encrypted protocols, highlighting the need for vigilance and defense strategies.
- DNS Cache Poisoning underscores the importance of understanding and combating this threat to safeguard online identities and data.
Read Full Article
14 Likes
For uninterrupted reading, download the app