Dev
2w
255
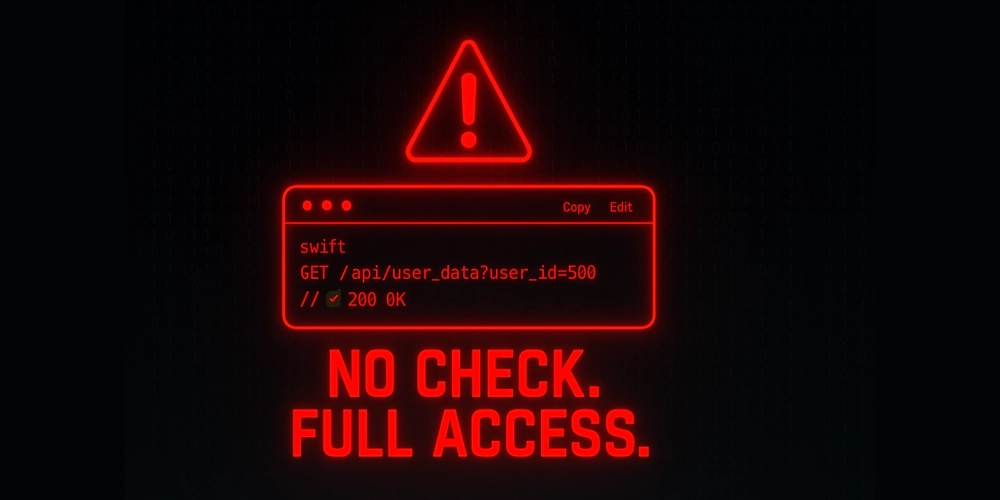
Image Credit: Dev
EXPOSED! The Authorization Blind Spot!
- In the digital world, Insecure Direct Object Reference (IDOR) poses a major security threat due to the oversight of checking user authorization.
- IDOR occurs when an application fetches sensitive data without verifying if the user has permission, making it a simple yet dangerous vulnerability.
- It is categorized under 'Broken Access Control' by OWASP and is increasingly exploited, especially with the rise of APIs and microservices.
- The vulnerability of IDOR is demonstrated through examples in Python (Flask) and Node.js (Express), showcasing how unauthorized access can occur.
- Common places where IDOR hides include URL parameters, POST bodies, hidden form fields, cookies, headers, and download routes.
- Real-world case studies like MTN Business Nigeria and Primary Arms highlight the repercussions of IDOR attacks, leading to data breaches.
- Hackers exploit IDOR through actions like URL tampering, form field manipulation, file download exploitation, API body injection, and path traversal.
- Preventing IDOR involves enforcing access control, not trusting user IDs, using indirect references, employing unpredictable identifiers, and sanitizing input.
- IDOR, a preventable mistake, emphasizes the importance of authorization checks to mitigate the risk of unauthorized data access.
- Developers are urged to audit resource access, replace direct ID usage with session mappings, and thoroughly test applications for vulnerabilities.
Read Full Article
15 Likes
For uninterrupted reading, download the app