Medium
2w
224
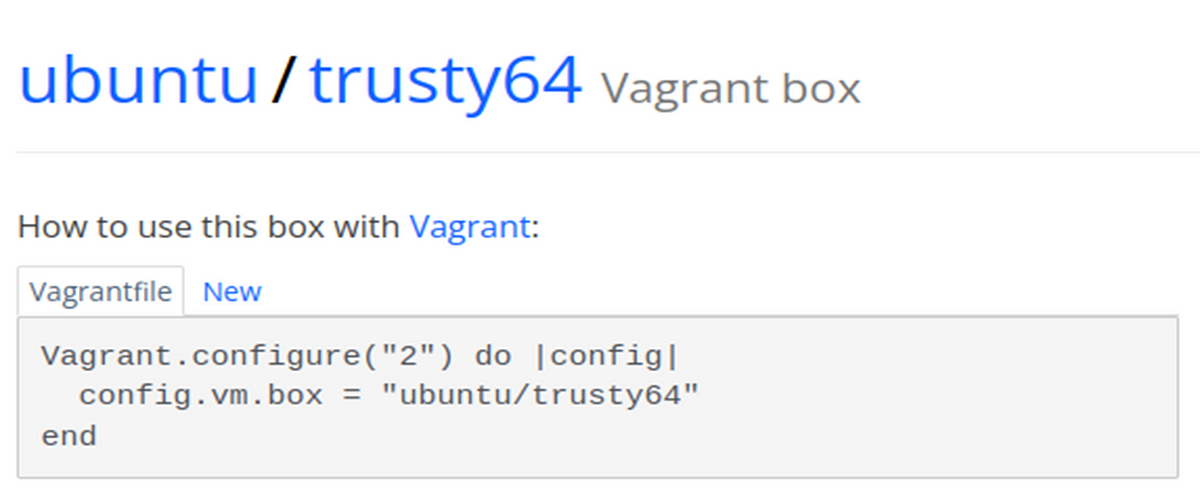
Image Credit: Medium
How To Create Your Own Vulnerable CTF Machines
- To create your own vulnerable Capture The Flag (CTF) machines, you can follow these steps:
- 1. Set up VirtualBox and Vagrant by downloading the necessary files and configuring the Vagrantfile.
- 2. Boot up the virtual machine.
- 3. Connect to the virtual machine and start configuring it manually or write an automated script.
- 4. Induce misconfigurations, gain initial access, escalate privileges, and perform cleanup and finalization.
- 5. Export the machine for others to use.
- To add specific Common Vulnerabilities and Exposures (CVEs) with publicly available exploits, you can download and install applications from exploit.db.
Read Full Article
13 Likes
For uninterrupted reading, download the app