Msandbu
3w
229
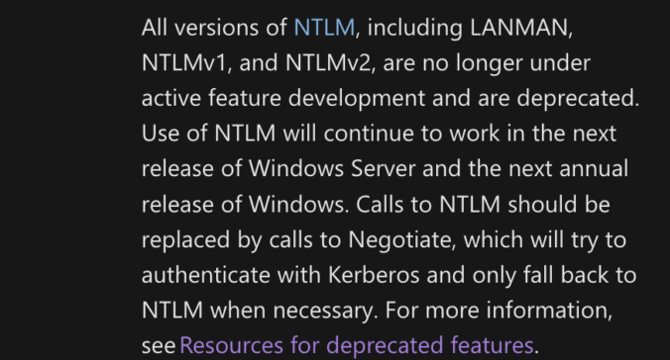
Image Credit: Msandbu
NTLM Deprecation – What does it actually mean?
- Microsoft has announced its decision to deprecate the authentication protocol NTLM (NT Lan Manager) which has been misused numerous times in various cyberattacks.
- NTLM is used in many different places and Microsoft is planning to disable it by default and move towards the use of Kerberos instead.
- Reducing the use of NTLM will ultimately culminate in it being disabled in Windows 11.
- Customers will also be able to use the enhanced controls we are providing to re-enable NTLM for compatibility reasons.
- Auditing NTLM events in your environment is required, which can be done by configuring some group policy settings and as long as you have the Azure Monitoring Agent installed.
- SMB and print services are some that are happy using NTLM but the logs for event ID 8002 are pretty useless in most cases.
- Members of the Protected Users group can only authenticate using Kerberos with Advanced Encryption Standards (AES).
- However, blocking NTLM is no joke and requires extra caution and implementation expertise within an organization.
- In conclusion, NTLM usage will be deprecated with the objective of moving towards increased use of Kerberos authentication on several Windows-based hosts.
- It is important for organizations to audit the use of NTLM in their environment and make relevant changes to move to using Kerberos instead.
Read Full Article
13 Likes
For uninterrupted reading, download the app