Dev
2w
326
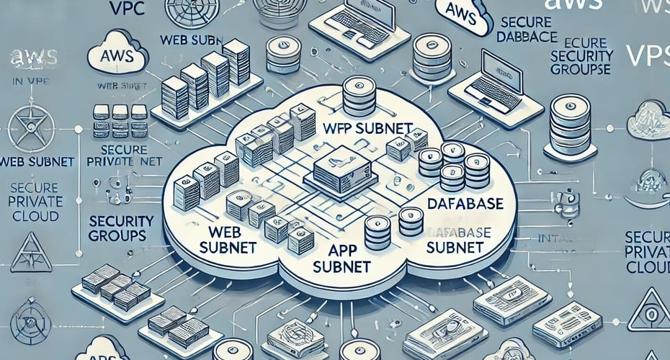
Image Credit: Dev
Secure Multi-Tier Web Application in a Custom VPC
- Create a custom VPC with public and private subnets.
- Deploy a web application with secure application and database layers.
- Utilize security groups and NACLs for traffic control between the tiers.
- Enable logging for network traffic monitoring and troubleshooting.
Read Full Article
19 Likes
For uninterrupted reading, download the app