Dev
1M
202
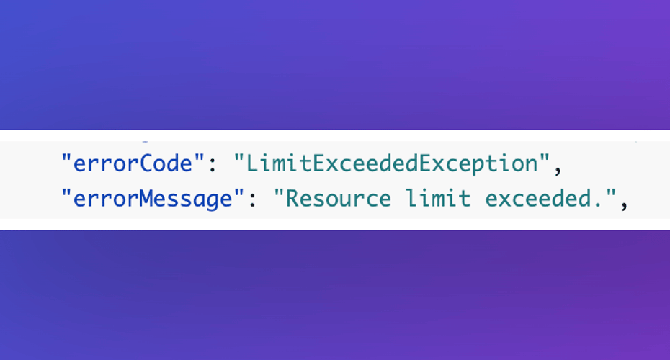
Image Credit: Dev
[Solved] Resource limit exceeded
- While deploying an OpenSearch domain with logging via CDK, I hit a “Resource limit exceeded” error due to more than 10 resource access policies for CloudWatch log groups.
- To fix this, I created CloudWatch log groups in CDK and passed their ARNs to a Lambda function.
- In the Lambda, I used the AWS SDK’s putResourcePolicy to update the existing policy with OpenSearch as the principal and attached the log group ARNs.
- I also set suppressLogsResourcePolicy: true in OpenSearch to stop CDK from creating resource policies automatically.
- This bypassed the limit and gave me full control over the policies.
- Initially, I created both the log groups and the Lambda function within the same construct, while OpenSearch was placed in a different construct that received the log groups as props.
- This setup caused issues because the log groups were being referenced by the correct log group name in the same construct and a different one outside of the construct in the opensearch construct, which led to the Lambda failing to update the policy correctly.
- While this solution worked for me, I’m still relatively new to CDK, so there might be better approaches out there.
- If you have a more elegant solution or if I’ve made any mistakes in my understanding, I’d truly appreciate hearing your thoughts!
- The GitHub issues I referenced were incredibly helpful in providing context and guiding me toward a solution.
Read Full Article
12 Likes
For uninterrupted reading, download the app