Medium
2d
241
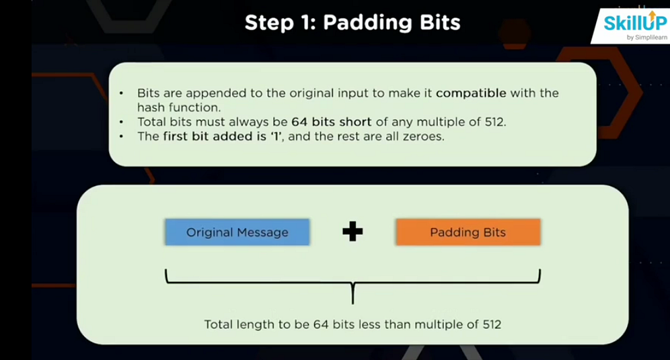
Image Credit: Medium
Steps involved in Secure Hash Algorithm : How to get a secure digital fingerprint
- Secure Hash Algorithm (SHA-1) involves appending bits to the original input to ensure compatibility with the hash function.
- Padding ensures the total bits are always 64 bits or a multiple of 512, with the first added bit as '1' followed by zeros.
- The padding length involves expressing the length of the original message in a 64-bit format to create a multiple of 512 bits and increase complexity.
- Chaining variables A, B, C, D, and E are initialized with fixed values, breaking down the message into 512-bit blocks.
- Each 512-bit block is processed into 16 sub-blocks using different logical and constant operations over 80 rounds, creating a unique hash.
- Non-linear processes in each round involving different operations like AND, OR, and XOR further enhance the uniqueness and security of the hash.
- SHA-1 transforms any information into a fixed-size digital fingerprint, ensuring irreversibility, similar to baking a cake with unbreakable ingredients.
- The process includes padding bits, padding length, initializing chaining variables, processing each block, and applying non-linear transformations.
- At the end, SHA-1 delivers a 160-bit hash representing the original message in a way that cannot be decrypted back, ensuring security.
- SHA-1 safeguards passwords, messages, and data by generating unique digital fingerprints that cannot be reversed, ensuring data security.
Read Full Article
14 Likes
For uninterrupted reading, download the app