Medium
2M
280
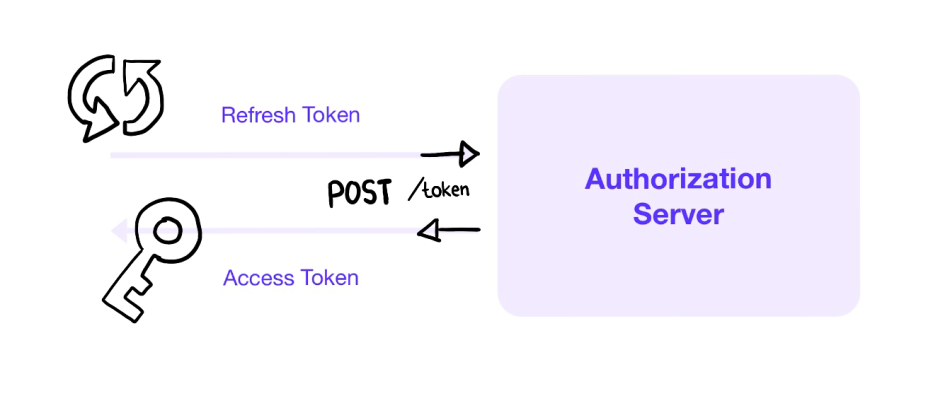
Image Credit: Medium
Using Access Tokens and Refresh Tokens Effectively: A Guide to Securing API-Driven Applications
- Access tokens and refresh tokens are crucial components in developing secure authentication systems for API-driven applications.
- Access tokens function as digital keys that grant users access to restricted resources, containing user information and permission details with short expiration periods to minimize security risks.
- Refresh tokens complement access tokens by enabling the application to obtain new access tokens without requiring the user to log in again, maintaining sessions and enhancing user experience.
- Secure implementation practices such as token storage, transmission over HTTPS, token expiry management, role-based permissions, and token revocation are essential for effectively using access and refresh tokens in applications.
Read Full Article
16 Likes
For uninterrupted reading, download the app