Hackingarticles
4w
336
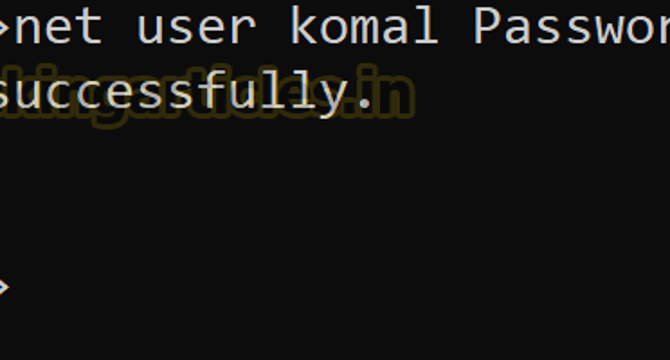
Image Credit: Hackingarticles
Abusing AD-DACL : Generic ALL Permissions
- In this post, we explore the exploitation of Discretionary Access Control Lists (DACL) using the Generic ALL permission in Active Directory environments.
- The “Generic ALL” privilege is one of the most powerful in AD because it grants complete control over the target object.
- Here’s how an attacker can leverage the “Generic ALL” privilege to compromise Active Directory:
- Weak DACLs can lead to unauthorized access or privilege escalation if not properly configured.
- Abusing DACL using the Generic ALL permission can enable various attacks like Kerberoasting, password resets, and account manipulation.
- Bloodhound or PowerView tools are used for identifying objects where attackers have Generic ALL privileges.
- Detection mechanisms such as Active Directory DACL can be used to identify and mitigate these vulnerabilities.
- A prerequisite to execute these attacks is to have a lab environment set up using Windows Server as Active Directory, Kali Linux, and Windows 10/11 clients.
- In Active Directory (AD), a DACL is a component of an object’s security descriptor that specifies which users or groups are allowed (or denied) access to the object and what actions they are permitted to perform.
- Kerberoasting is an attack technique that targets service accounts in Active Directory environments, where an attacker with Generic ALL permissions on a user can exploit the ability to request service tickets (TGS).
Read Full Article
20 Likes
For uninterrupted reading, download the app