Info. Security News News
Kaspersky
21

Image Credit: Kaspersky
How extensions from Open VSX were used to steal cryptocurrency
- Malicious Open VSX extensions targeted Solidity developers, leading to cryptocurrency theft.
- Extensions lacked useful functionality, acting as fake software, enabling attackers to steal.
- Fake extension outranked real ones due to loopholes in Open VSX ranking algorithm.
- Developers urged to be cautious while installing extensions and monitor for suspicious activity.
- Recommendations include checking developer details and using XDR solutions for monitoring.
Read Full Article
1 Like
Socprime
219

Image Credit: Socprime
CVE-2025-25257 Vulnerability: Critical SQL Injection in Fortinet FortiWeb Enables Unauthenticated Remote Code Execution
- A critical SQL injection vulnerability, CVE-2025-25257, in Fortinet's FortiWeb enables unauthenticated remote code execution, assigned a CVSS score of 9.6.
- Exploitation of vulnerabilities like CVE-2025-25257 is a common method for attackers, with a 34% increase in such activities noted in 2025, leading to an uptick in security breaches.
- Fortinet advises users to apply patches promptly to address CVE-2025-25257 affecting multiple versions of FortiWeb and suggests temporarily disabling the HTTP/HTTPS administrative interface as a workaround.
- Organizations can utilize the SOC Prime Platform for real-time cyber threat intelligence, curated detection algorithms, and tools like Uncoder AI to enhance detection engineering and threat hunting capabilities.
Read Full Article
13 Likes
Medium
141

Image Credit: Medium
SOCFortres5: Louis Vuitton Data Breach Exposes Customer Information in Sophisticated Cyberattack
- Louis Vuitton experienced a data breach due to cyberattack exploiting vulnerabilities in their digital infrastructure.
- Attackers targeted e-commerce backend or third-party services, leading to significant data leakage despite the company's rapid response.
- Digital forensics experts are assessing the breach, suspecting phishing or malware injection for obtaining admin-level privileges.
- Louis Vuitton is notifying affected customers, cooperating with authorities, and enhancing security measures to prevent future intrusions.
Read Full Article
8 Likes
Securityaffairs
74

Image Credit: Securityaffairs
An attacker using a $500 radio setup could potentially trigger train brake failures or derailments from a distance
- US CISA warns about a critical flaw in End-of-Train and Head-of-Train systems, allowing hackers to trigger emergency braking and issue unauthorized brake commands.
- The vulnerability, tracked as CVE-2025-1727, affects the radio-based linking protocol between End-of-Train (EoT) and Head-of-Train systems used in freight trains.
- Exploiting the lack of encryption and authentication, attackers could send crafted radio packets to manipulate brake commands, potentially causing disruptions, brake failures, or derailments.
- Despite efforts to address the flaw and replace the outdated protocol by 2027, the risk remains severe, with the potential for an attacker using a $500 radio setup to remotely trigger train brake failures or derailments, posing national safety risks.
Read Full Article
4 Likes
Securityaffairs
91
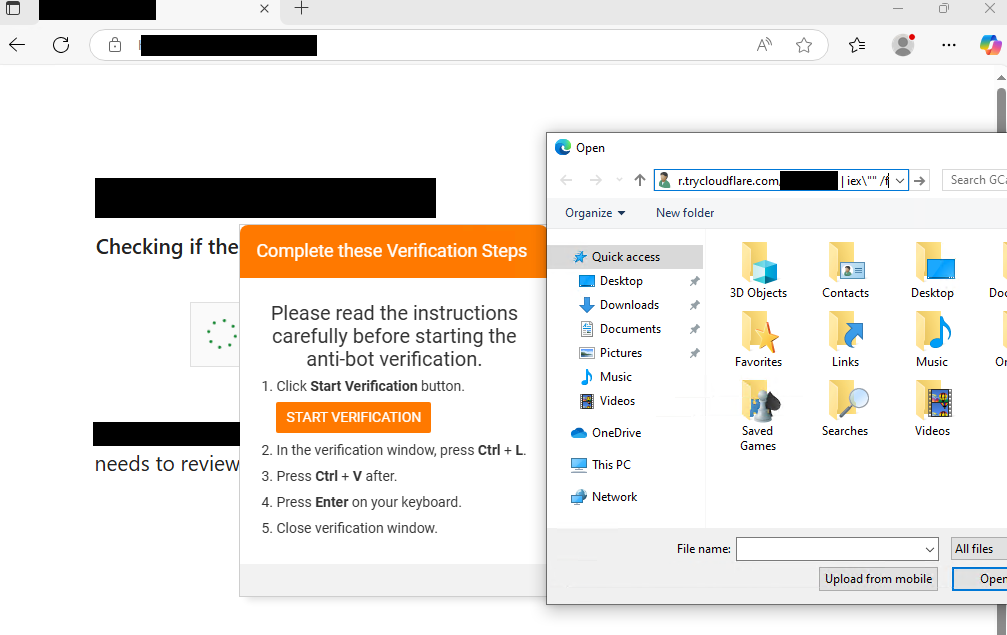
Image Credit: Securityaffairs
Interlock ransomware group deploys new PHP-based RAT via FileFix
- The Interlock ransomware group has deployed a new PHP-based variant of the Interlock RAT through a campaign using a delivery method known as FileFix, targeting various industries as reported by researchers.
- The PHP variant, which emerged in June and is distinct from the previous JavaScript-based version, spreads through compromised websites using hidden scripts to deceive victims into running a PowerShell script to install the malware.
- The Interlock RAT, once deployed, conducts system reconnaissance, checks privilege levels, exfiltrates system info, establishes a command and control channel through trycloudflare.com URLs, and supports various commands for malicious activities such as lateral movement via RDP.
- The campaign showcases the Interlock group's evolving tactics and operational sophistication, moving from Node.js to PHP for access to victim networks. Researchers have provided Sigma and YARA rules along with IOCs for identification.
Read Full Article
5 Likes
Qualys
140

Image Credit: Qualys
The State of Cyber Risk 2025: Business Context Needed
- Despite increasing investments in cyber risk programs, organizations remain immature in risk management.
- New data reveals cyber risk rising as digital transformation accelerates and AI threats emerge.
- Most organizations lack business context in cyber risk management, affecting effectiveness and ROI.
- Formal cyber risk programs are expanding, but many still lack alignment with business objectives.
- Prioritizing risks based on business context and evolving towards a Risk Operations Center model.
Read Full Article
8 Likes
Securityaffairs
29

Image Credit: Securityaffairs
Global Louis Vuitton data breach impacts UK, South Korea, and Turkey
- A global data breach at Louis Vuitton has impacted customers in the UK, South Korea, Turkey, and possibly more countries.
- The breach, discovered on July 2nd, exposed customer personal information like names and contact details but did not compromise passwords or payment card data.
- Notifications are ongoing, with concerns about potential misuse of stolen data for phishing or fraud attempts.
- Louis Vuitton's parent company, LVMH, reported this as the third breach in three months, with attackers accessing systems nearly a month before detection.
Read Full Article
1 Like
Securityaffairs
126

Image Credit: Securityaffairs
Experts uncover critical flaws in Kigen eSIM technology affecting billions
- Experts discovered critical flaws in Kigen eSIM technology, impacting billions of devices.
- The hack targeted Kigen's eSIM technology, affecting over 2 billion IoT devices and smartphones.
- The vulnerabilities in the Kigen eUICC card raise serious security concerns, as neither eSIM profiles nor Java Card apps on the chip are adequately protected.
- The breach underscores significant risks in eSIM technology and questions industry security assumptions, with researchers elucidating the need for heightened MNO, vendor, and security community awareness.
Read Full Article
7 Likes
Securityaffairs
7

Image Credit: Securityaffairs
Spain awarded €12.3 million in contracts to Huawei
- Spain awarded €12.3 million in contracts to Huawei to manage and store judicially authorized wiretaps, sparking concerns over potential Chinese government access due to Huawei's ties to Beijing.
- The contracts were awarded between 2021 and 2025 for digital storage of wiretaps using Huawei's OceanStor 6800 V5 servers, adhering to national security standards.
- Internal sources from Spain's National Police and Civil Guard expressed security concerns over Huawei's involvement in sensitive systems, despite Prime Minister Pedro Sánchez's support of the company.
- While Huawei denies engaging in espionage, concerns persist over its ties to the Chinese state, contrasting with EU and US caution regarding the company's involvement in sensitive infrastructure projects.
Read Full Article
Like
Securityaffairs
349

Image Credit: Securityaffairs
Patch immediately: CVE-2025-25257 PoC enables remote code execution on Fortinet FortiWeb
- PoC exploits for CVE-2025-25257 in Fortinet FortiWeb enable pre-auth RCE, urging users to patch.
- The flaw is a SQL injection vulnerability (CWE-89) allowing unauthorized SQL commands via HTTP/HTTPS requests.
- Fortinet released security patches in versions 7.6.4, 7.4.8, 7.2.11, and 7.0.11 to address the issue.
- Administrators are advised to patch immediately due to the availability of public exploits, with potential future active exploitation.
Read Full Article
21 Likes
Securityaffairs
142

Image Credit: Securityaffairs
Wing FTP Server flaw actively exploited shortly after technical details were made public
- Hackers are actively exploiting a critical flaw (CVE-2025-47812) in Wing FTP Server, allowing remote code execution with root/system privileges.
- The vulnerability stems from improper handling of null bytes, enabling injection of malicious Lua code into session files.
- Even anonymous FTP accounts can be used to trigger code execution with administrative rights on both Linux and Windows systems.
- Researchers confirmed active exploitation of the flaw shortly after technical details were made public on June 30, urging users to update to server version 7.4.4 or later.
Read Full Article
8 Likes
Securityaffairs
321

Image Credit: Securityaffairs
Security Affairs newsletter Round 532 by Pierluigi Paganini – INTERNATIONAL EDITION
- McDonald’s job app exposes data of 64 million applicants
- Russian basketball player accused in U.S. ransomware case
- UK NCA arrests four people over M&S, Co-op cyberattacks
- PerfektBlue Bluetooth attack allows hacking infotainment systems of Mercedes, Volkswagen, and Skoda
Read Full Article
18 Likes
Securityaffairs
223
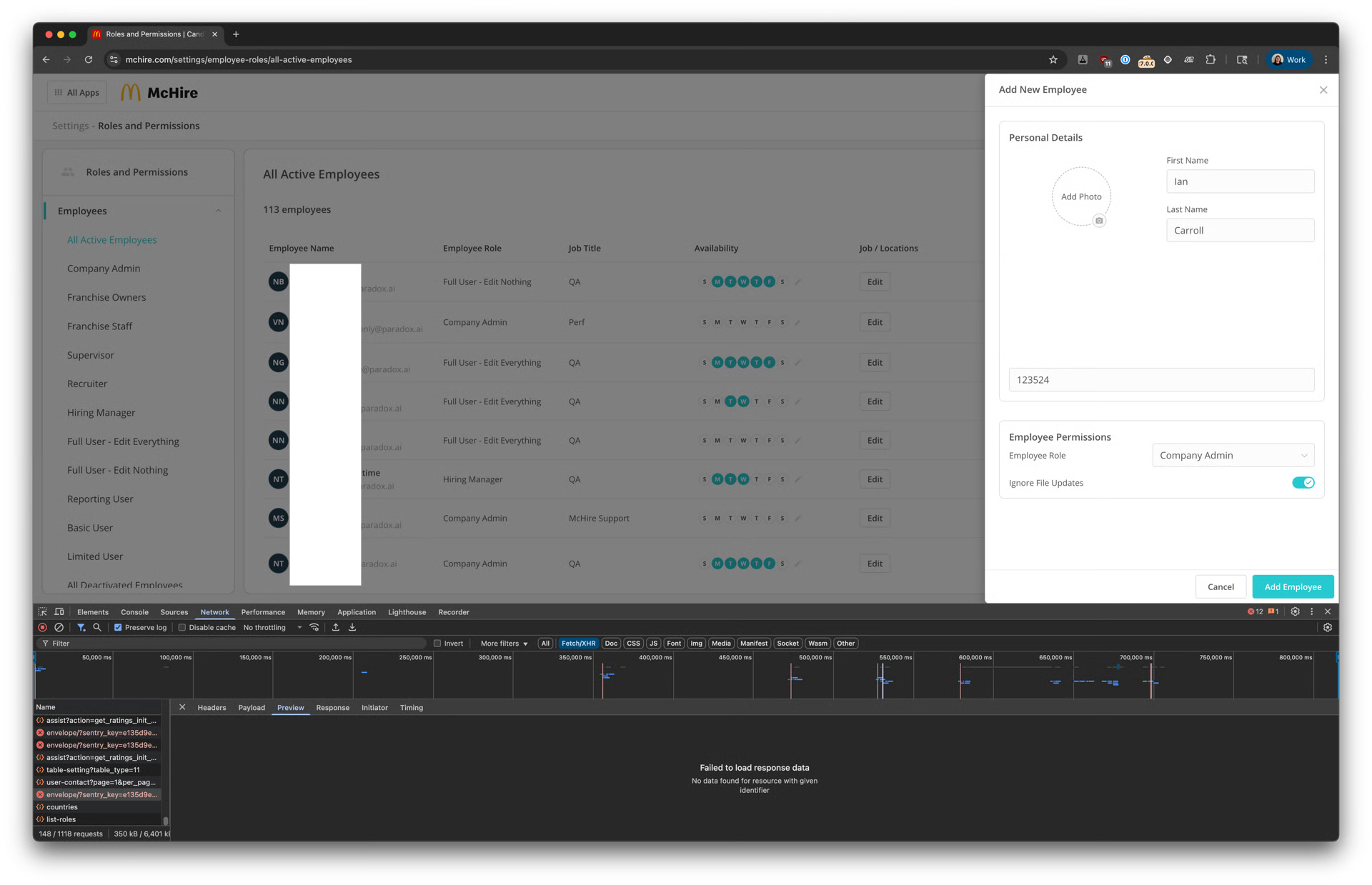
Image Credit: Securityaffairs
McDonald’s job app exposes data of 64 Million applicants
- Security researchers discovered vulnerabilities in McDonald’s McHire chatbot exposing data of over 64 million job applicants.
- Major flaws like default credentials '123456' and insecure APIs allowed access to private chats, admin privileges, and sensitive info.
- Researchers gained unauthorized access to internal data but promptly alerted Paradox.ai, who resolved the issues and enhanced security.
- McDonald's and Paradox.ai were informed of the vulnerabilities, leading to a quick response and resolution of the security concerns.
Read Full Article
6 Likes
Securityaffairs
331

Image Credit: Securityaffairs
Athlete or Hacker? Russian basketball player accused in U.S. ransomware case
- Russian basketball player Daniil Kasatkin, 26, was arrested in France at the request of the U.S. over alleged ties to a ransomware group targeting U.S. companies and federal entities.
- Kasatkin is suspected of aiding a ransomware group that targeted over 900 entities from 2020 to 2022, allegedly helping negotiate ransoms.
- Despite the accusations, Kasatkin denies all charges, with his lawyer claiming he lacks the technical skills for such involvement, having minimal computer knowledge.
- The athlete's lawyer unsuccessfully requested his release, citing health and career concerns, with Kasatkin experiencing weight loss in detention and feeling unsafe amidst the Russia-Ukraine conflict.
Read Full Article
19 Likes
Schneier
68

Squid Dominated the Oceans in the Late Cretaceous
- New research focused on finding ancient squid beaks to understand squid evolution due to the lack of squid fossils with hard shells.
- An advanced fossil discovery technique digitized Late Cretaceous rocks from Japan, leading to the identification of 1,000 fossilized cephalopod beaks, including 263 squid specimens and 40 previously unknown squid species.
- The number of squid fossils found surpassed bony fishes and ammonites in the rocks, indicating a dominance of squid specimens in the Late Cretaceous oceans.
Read Full Article
4 Likes
For uninterrupted reading, download the app