Securityaffairs
2M
78
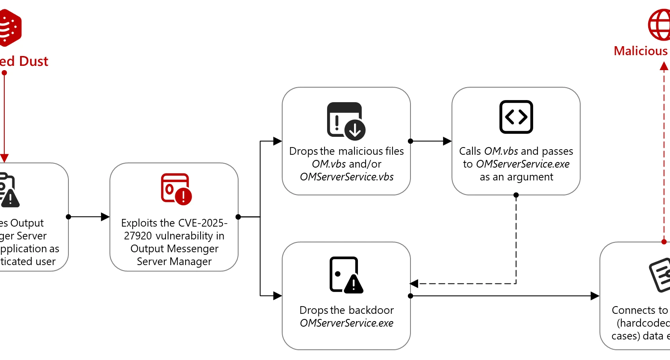
Image Credit: Securityaffairs
APT group exploited Output Messenger Zero-Day to target Kurdish military operating in Iraq
- A Türkiye-linked group, Marbled Dust, exploited a zero-day vulnerability in Output Messenger (CVE-2025-27920) to spy on Kurdish military targets in Iraq since April 2024.
- Marbled Dust, active since 2017, primarily targets organizations in Europe and the Middle East, with a history of using DNS hijacking in campaigns.
- The group targeted various entities, including government entities, Kurdish political groups, telecommunication, ISPs, NGO, and Media & Entertainment sectors.
- The exploit allowed the group to upload malicious files, gain access to user communications, steal data, compromise credentials, and deploy backdoors for exfiltration.
Read Full Article
4 Likes
For uninterrupted reading, download the app