Securityaffairs
2w
395
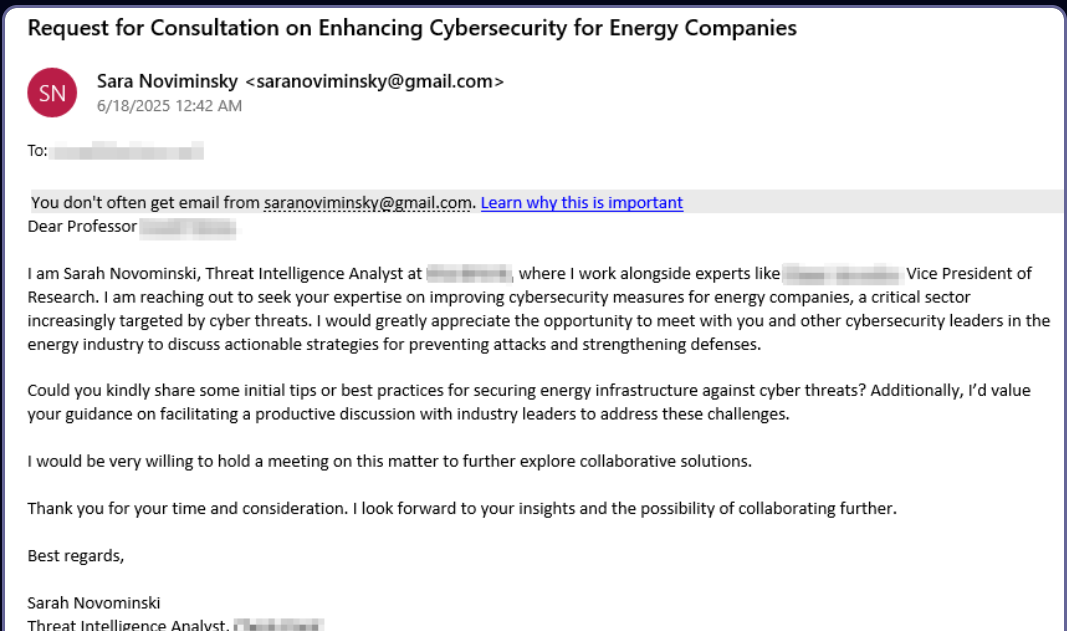
Image Credit: Securityaffairs
APT42 impersonates cyber professionals to phish Israeli academics and journalists
- Iran-linked APT42, known as Educated Manticore, targets Israeli journalists, cybersecurity experts, and academics with phishing attacks by impersonating security professionals.
- APT42 focuses on highly targeted spear-phishing using techniques such as credential harvesting, surveillance operations, and malware deployment.
- The threat actors created fake Gmail login pages and Google Meet invitations to steal email credentials and 2FA codes from victims, gaining unauthorized access to their accounts.
- The group used custom phishing kits mimicking Gmail, Outlook, and Yahoo, employing live keyloggers and WebSocket connections to control the stolen data.
Read Full Article
23 Likes
For uninterrupted reading, download the app