Hackingblogs
1M
328
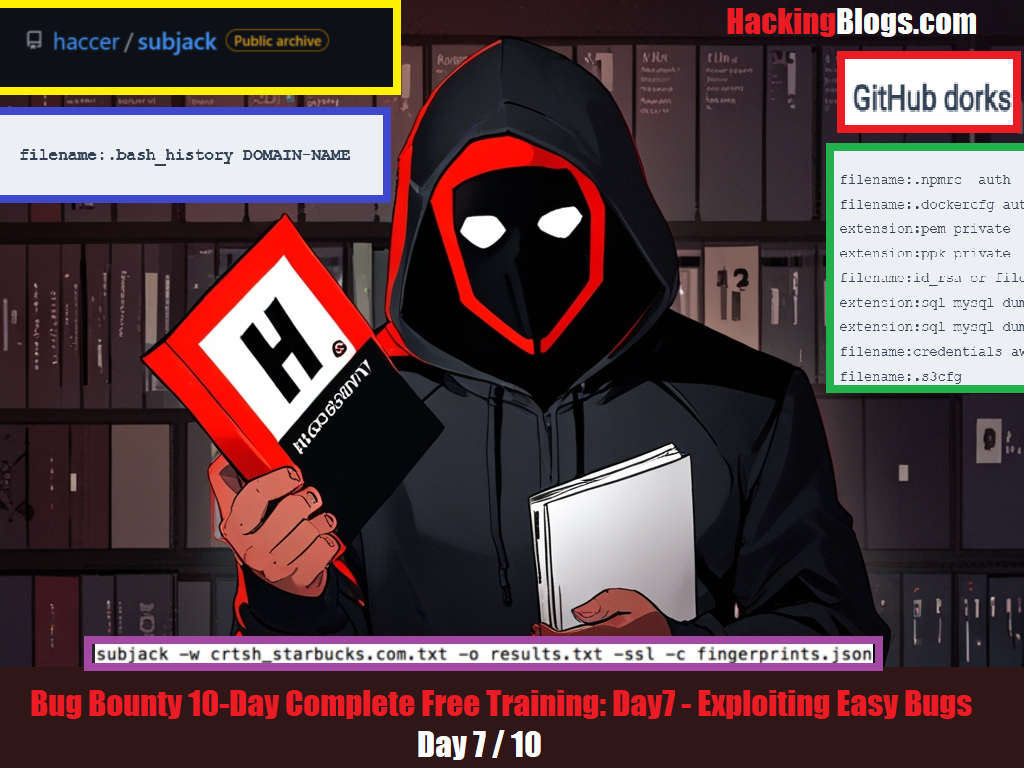
Image Credit: Hackingblogs
Bug Bounty 10-Day Complete Free Training: Day7 – Exploiting Easy Bugs
- Dipanshu Kumar hosts a free 10-day Bug Bounty course focusing on improving bug-hunting skills and exploiting vulnerabilities efficiently.
- Day 7 introduces exploitation techniques such as subdomain takeover, GitHub Dorks, and information leaks via GitHub.
- The focus is on finding low-hanging bugs quickly to maximize rewards, targeting areas like subdomain takeover, GitHub, and cloud services.
- Subdomain takeover occurs when a subdomain points to an unused resource, allowing hackers to gain control of it.
- Steps for exploiting subdomain takeover flaws include checking subdomains, identifying vulnerable applications, and taking control of subdomains.
- GitHub Dorks can be used to find sensitive information like passwords, API keys, and more in GitHub repositories.
- The example of finding a secret key in the source code demonstrates the potential risks of sensitive data exposure.
- Various GitHub Dorks are provided for hunting purposes, targeting file extensions, configuration files, and other sensitive information.
- Readers are encouraged to regularly search for subdomain takeovers and exposed information to maximize bug bounty hunting success.
- The article concludes with a preview of upcoming topics on information disclosure strategies and more complex vulnerabilities.
Read Full Article
19 Likes
For uninterrupted reading, download the app