Securityaffairs
2M
128
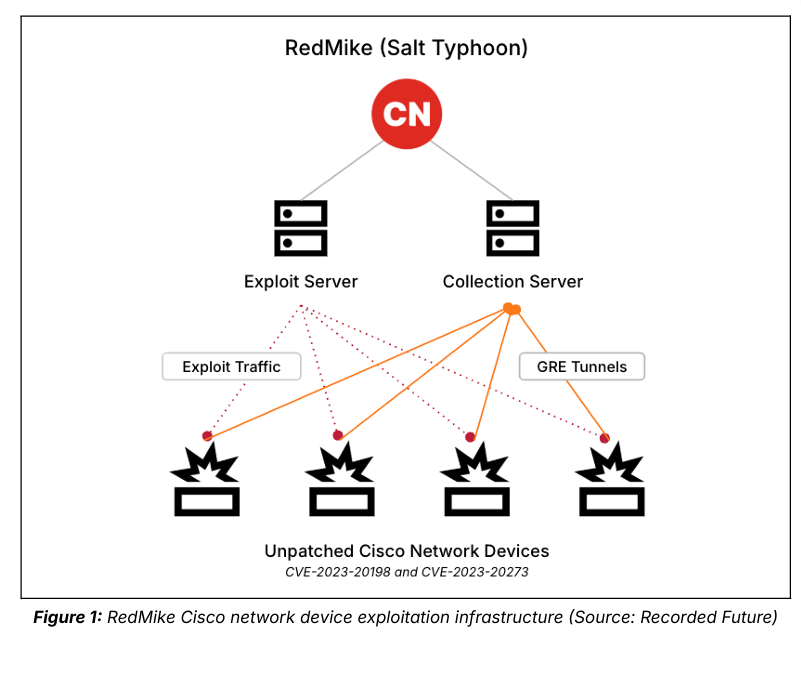
Image Credit: Securityaffairs
China-linked APT Salt Typhoon breached telecoms by exploiting Cisco router flaws
- China-linked APT group Salt Typhoon breached U.S. telecom providers by exploiting Cisco IOS XE flaws CVE-2023-20198 and CVE-2023-20273.
- The vulnerabilities allowed the attackers to gain admin privileges on routers and escalate to root, potentially exfiltrating data.
- The attacks targeted ISPs in the U.S., Italy, a U.K.-affiliated U.S. telecom, and providers in South Africa and Thailand.
- RedMike used GRE tunnels on compromised Cisco devices for persistence, evasion, and data exfiltration.
- APT Salt Typhoon, also known as FamousSparrow and GhostEmperor, targeted government entities and telecoms since 2019.
- The group breached nine U.S. telecoms, including Charter Communications and Windstream, exploiting network device vulnerabilities.
- White House confirmed China-linked APT Salt Typhoon's cyberespionage campaign targeting telco firms globally.
- China accessed metadata but no classified info was compromised; Neuberger revealed China targeted government and political figures.
- Global warnings were issued against PRC-linked cyber espionage targeting telecom networks; measures advised to strengthen network security.
- Bejing denied responsibility for the hacking campaign as efforts were made to secure networks post cyberespionage attempts.
Read Full Article
7 Likes
For uninterrupted reading, download the app