Securityaffairs
1M
303
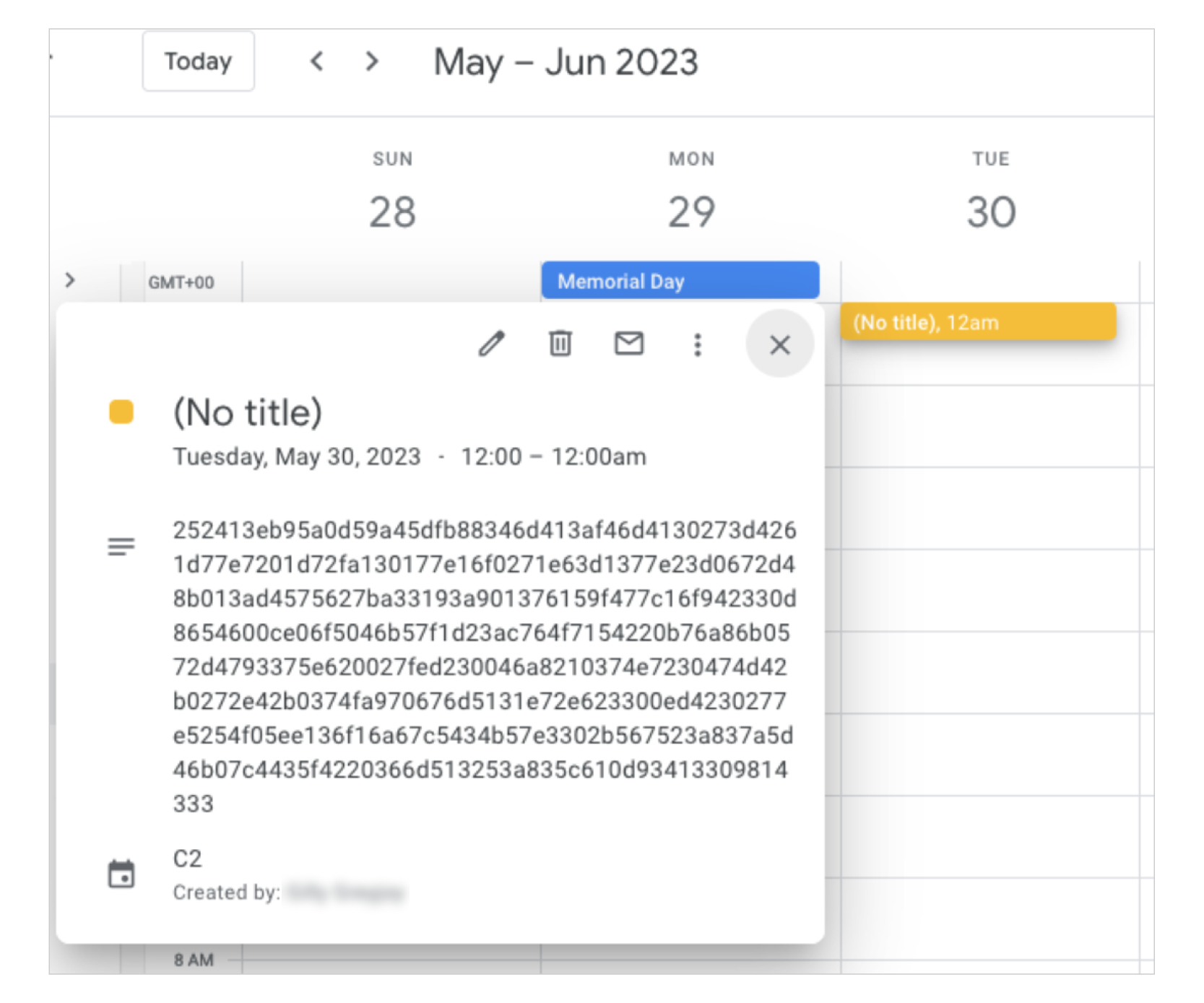
Image Credit: Securityaffairs
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware
- China-linked group APT41 used Google Calendar as a command-and-control (C2) channel to control its TOUGHPROGRESS malware, targeting government entities through a compromised website.
- APT41 used spear phishing emails with a ZIP file hosted on a hacked government site to distribute the TOUGHPROGRESS malware, which operates in three stealthy stages with advanced evasion tactics.
- TOUGHPROGRESS decrypts and runs stages in memory, uses process hollowing for injection, and communicates with operators through Google Calendar to exfiltrate data and receive commands.
- Google has developed custom fingerprints to disrupt APT41 and TOUGHPROGRESS malware, terminated attacker-controlled projects, updated file detections, and shared threat intel with affected organizations.
Read Full Article
18 Likes
For uninterrupted reading, download the app