Securityaffairs
1w
321
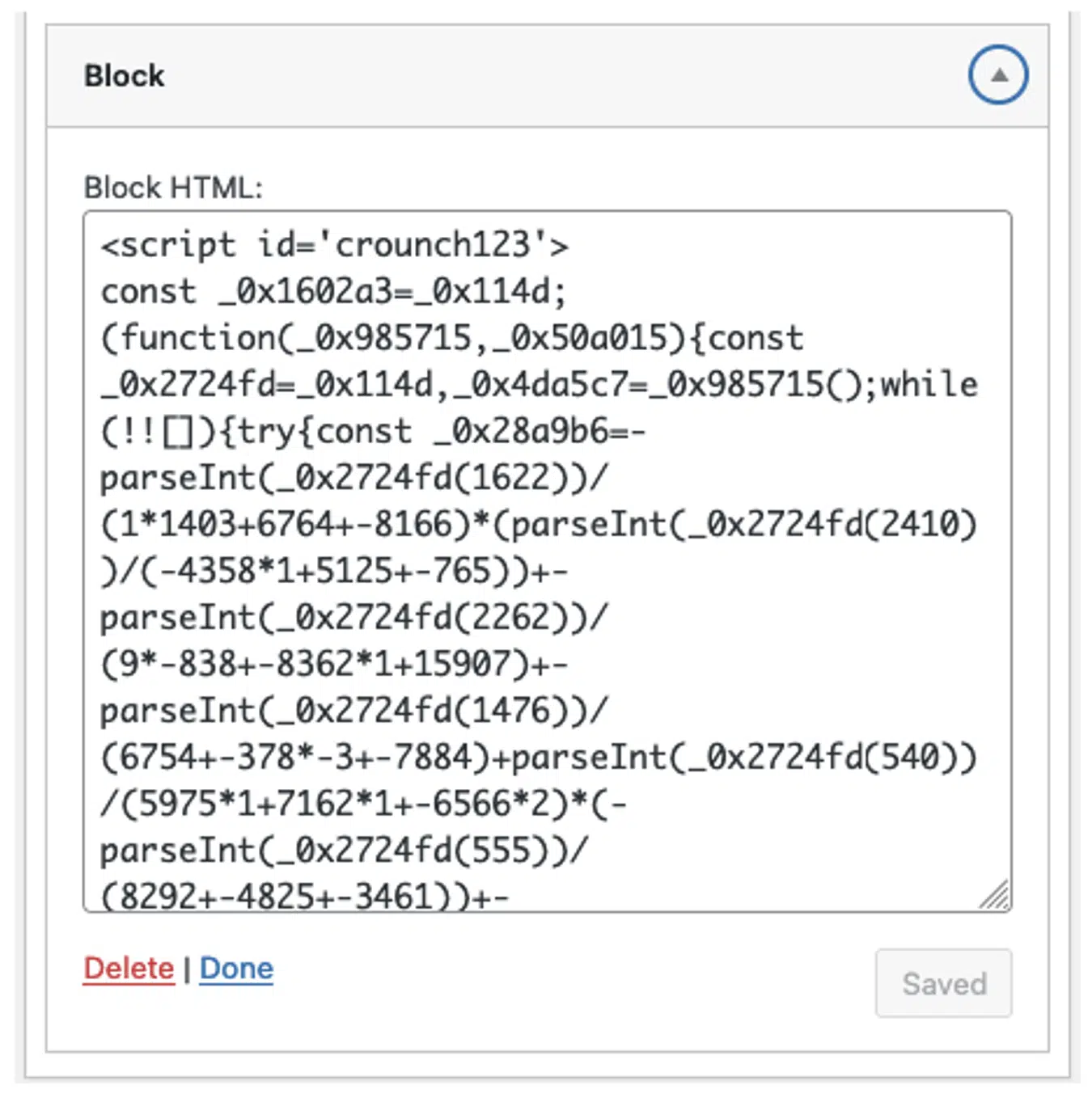
Image Credit: Securityaffairs
Credit Card Skimmer campaign targets WordPress via database injection
- Stealthy credit card skimmer targets WordPress e-commerce sites, injecting malicious JavaScript into CMS database tables to evade detection.
- Attackers hide the malicious code in the WordPress wp_options table, injecting obfuscated JavaScript into widget_block for persistence and to avoid file scans.
- The JavaScript code targets checkout pages, creating fake payment screens to capture credit card details and billing information.
- The stolen data is encoded and encrypted, then transmitted to an attacker-controlled server.
Read Full Article
19 Likes
For uninterrupted reading, download the app