Securityaffairs
1M
8
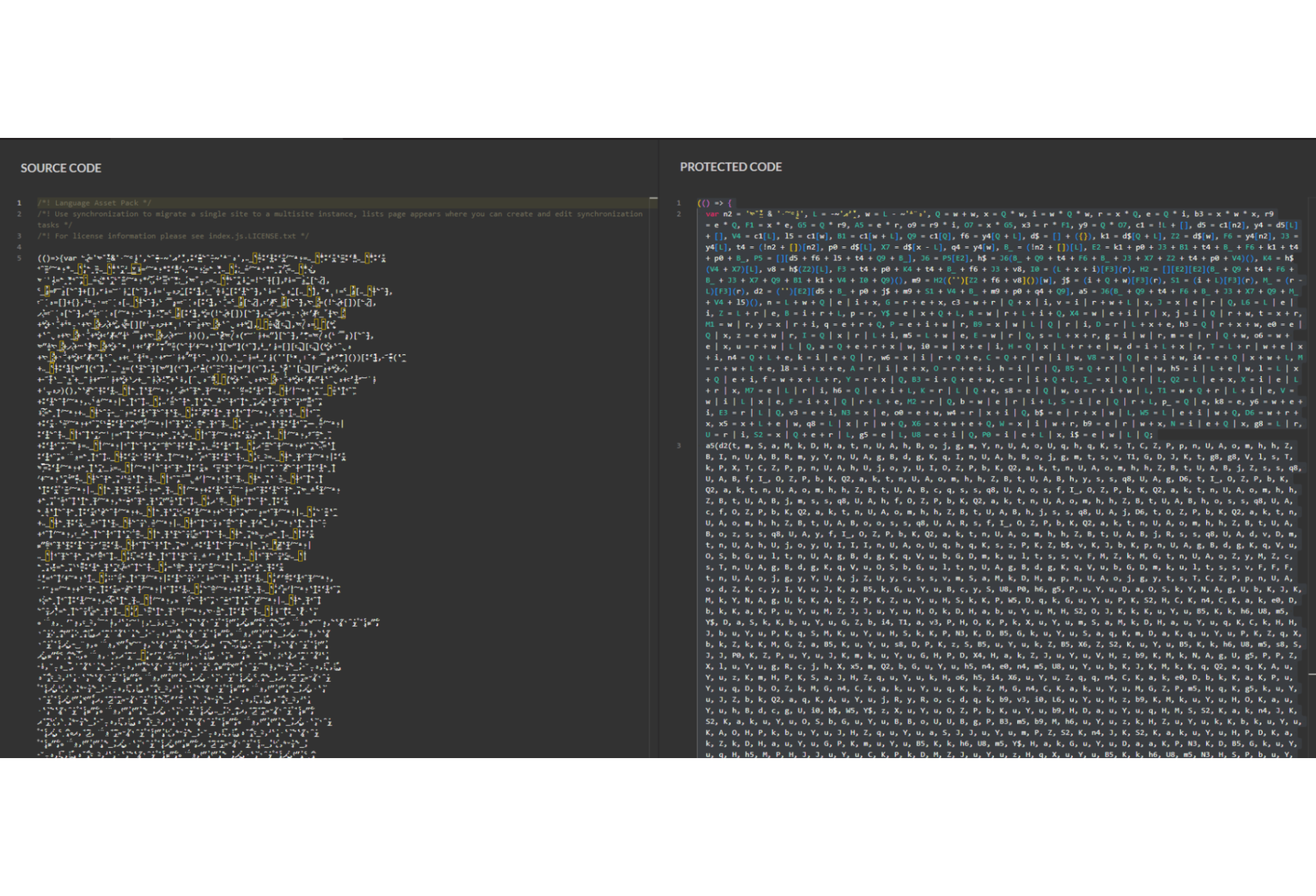
Image Credit: Securityaffairs
E-skimming campaign uses Unicode obfuscation to hide the Mongolian Skimmer
- Jscrambler researchers uncovered a skimming campaign using unique JavaScript obfuscation with accented characters to hide a skimmer named Mongolian Skimmer.
- The attackers used unusual Unicode characters for variables and function names.
- The skimmer was named “Mongolian Skimmer” after researchers found it used the Unicode character “Mongolian Letter OE” as an identifier in the code.
- The Mongolian Skimmer employs common techniques such as DOM monitoring, data exfiltration, DevTools detection, and anti-debugging measures to evade detection and tampering.
Read Full Article
Like
For uninterrupted reading, download the app