Securityaffairs
1M
263
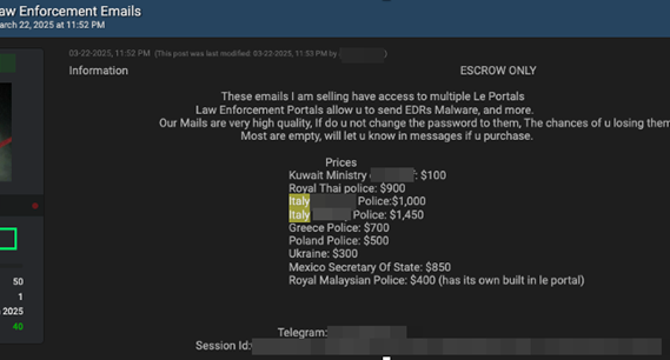
Image Credit: Securityaffairs
EDR-as-a-Service makes the headlines in the cybercrime landscape
- Cybercriminals are utilizing compromised accounts for EDR-as-a-Service (Emergency Data Requests), targeting major platforms.
- A detailed analysis by Meridian Group reveals the rise of 'EDR-as-a-Service' in the cybersecurity landscape.
- Criminal groups exploit stolen credentials to forward false Emergency Data Requests, obtaining sensitive information.
- The model has evolved to cover every aspect of the process, making it easier for non-technical individuals to access confidential data for a fee in cryptocurrencies.
- Payment dynamics involve transactions in Bitcoin or Monero on underground forums with escrow services for secure exchanges.
- Operational manuals and deception strategies guide the use of EDR services, facilitating social engineering and doxxing campaigns.
- The illicit sector's professionalization poses risks to cybersecurity and privacy, potentially affecting governmental infrastructures and citizens' privacy.
- Ransomware groups are showing interest in EDR techniques, hinting at a future blend of ransomware attacks with specific data obtained through fraudulent EDRs.
- Recommendations include strengthening validation procedures and authentication systems to mitigate risks and safeguard digital security and privacy.
- Urgent collaboration and process enhancement are crucial to prevent the proliferation of this threat and protect institutional channels and citizens' privacy.
Read Full Article
15 Likes
For uninterrupted reading, download the app