Hackers-Arise
4w
279
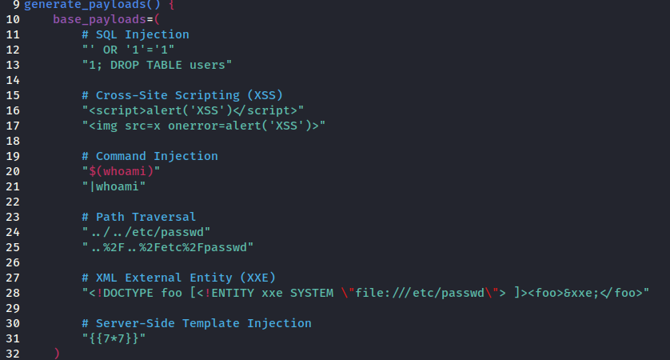
Image Credit: Hackers-Arise
Exploit Development: Building Your Own Fuzzer with BASH
- Web application fuzzing stands as a critical technique for uncovering vulnerabilities and developing exploits.
- This practical guide equips aspiring cyber warriors with the knowledge to wield BASH scripting as a powerful weapon in creating custom fuzzing tools.
- Fuzzing is a dynamic analysis technique used in software testing and security assessments.
- Fuzzing explores the vast input space of a program; generating inputs with a high likelihood of triggering bugs or vulnerabilities.
- Fuzzing can be categorized into several types based on the knowledge and approach used - black-box, white-box, grey-box, generation-based, mutation-based, and evolutionary.
- BASH scripting for web fuzzing offers simplicity and seamless system integration.
- Limitations of using BASH for web fuzzing are that it can be slow on large-scale projects and implementing advanced fuzzing techniques can be challenging.
- The tutorial covers creating payloads and request handling, including writing a function for sending requests and response analysis.
- By fuzzing the application, we can identify the application's breaking point, which can often be a place to exploit.
- Overall, web application fuzzing using Bash is a perfect starting point for aspiring cyber warriors.
Read Full Article
16 Likes
For uninterrupted reading, download the app