Hacking News
Idownloadblog
0

Image Credit: Idownloadblog
EverPwnage v1.2 released to support 32-bit devices running iOS 9.1-9.3.4
- EverPwnage v1.2 has been released, supporting 32-bit devices running iOS 9.1-9.3.4.
- The update includes support for new firmware and device combinations, improvements in exploit success rates, and the disabling of stashing by default on untethered jailbreaks.
- The update also introduces a new fork of JailbreakMe 4.0, a web-based jailbreak utility for 32-bit iOS 9.1-9.3.4 devices, using EverUntether.
- While the devices targeted by EverPwnage may be considered outdated, dedicated users who value continued development on jailbreaks and untethers will find these updates valuable.
Read Full Article
Like
Medium
84

Image Credit: Medium
Apple Built the Perfect Spy: Part 1
- Apple's transition to custom silicon represents significant shift in computing architecture with security implications.
- Complete vertical integration gives Apple control over tech stack, potentially creating surveillance infrastructure.
- Apple's M-Series transition eliminates trust boundaries, hinders conventional security auditing and enables surveillance capabilities.
- Multiple unpatchable hardware flaws in Apple Silicon reveal vulnerabilities to sophisticated hardware-level attacks.
- Integration with biometric systems and baseband processors raises concerns about privacy and potential surveillance.
Read Full Article
5 Likes
TechCrunch
377

Image Credit: TechCrunch
AI chatbot’s simple ‘123456’ password risked exposing personal data of millions of McDonald’s job applicants
- Security researchers discovered a security flaw that allowed access to personal data of 64 million McDonald's job applicants.
- The flaw involved logging into McDonald's AI job hiring chatbot with the weak password '123456.'
- The exposed data included applicants' names, email addresses, home addresses, and phone numbers.
- Paradox.ai, the provider of the chatbot, fixed the issues promptly after they were reported, ensuring candidate information was not leaked.
Read Full Article
22 Likes
Securelist
137

Image Credit: Securelist
Forensic journey: Breaking down the UserAssist artifact structure
- In-depth analysis of the UserAssist artifact structure reveals valuable execution information for investigations.
- UserAssist stores program details like run count, focus count, focus time, and execution time.
- Data inconsistencies were observed in UserAssist, stemming from interactions triggering FireEvent function.
- CUASession and UEME_CTLSESSION values play vital roles in maintaining UserAssist statistics.
- New insights gained on UserAssist data structure and its significance in forensic investigations.
Read Full Article
8 Likes
Securityaffairs
6

Image Credit: Securityaffairs
Spain awarded €12.3 million in contracts to Huawei
- Spain awarded €12.3 million in contracts to Huawei to manage and store judicially authorized wiretaps, sparking concerns over potential Chinese government access due to Huawei's ties to Beijing.
- The contracts were awarded between 2021 and 2025 for digital storage of wiretaps using Huawei's OceanStor 6800 V5 servers, adhering to national security standards.
- Internal sources from Spain's National Police and Civil Guard expressed security concerns over Huawei's involvement in sensitive systems, despite Prime Minister Pedro Sánchez's support of the company.
- While Huawei denies engaging in espionage, concerns persist over its ties to the Chinese state, contrasting with EU and US caution regarding the company's involvement in sensitive infrastructure projects.
Read Full Article
Like
Securityaffairs
334

Image Credit: Securityaffairs
Patch immediately: CVE-2025-25257 PoC enables remote code execution on Fortinet FortiWeb
- PoC exploits for CVE-2025-25257 in Fortinet FortiWeb enable pre-auth RCE, urging users to patch.
- The flaw is a SQL injection vulnerability (CWE-89) allowing unauthorized SQL commands via HTTP/HTTPS requests.
- Fortinet released security patches in versions 7.6.4, 7.4.8, 7.2.11, and 7.0.11 to address the issue.
- Administrators are advised to patch immediately due to the availability of public exploits, with potential future active exploitation.
Read Full Article
20 Likes
Medium
288
Image Credit: Medium
Apple Built the Perfect Spy: Part 2
- Exploring Apple's surveillance capabilities and defenses in its tightly controlled ecosystem.
- Detecting Apple's surveillance methods requires unconventional security approaches due to its full stack ownership.
- Power analysis and other advanced techniques may reveal potential covert surveillance activities by Apple.
Read Full Article
17 Likes
Securityaffairs
137

Image Credit: Securityaffairs
Wing FTP Server flaw actively exploited shortly after technical details were made public
- Hackers are actively exploiting a critical flaw (CVE-2025-47812) in Wing FTP Server, allowing remote code execution with root/system privileges.
- The vulnerability stems from improper handling of null bytes, enabling injection of malicious Lua code into session files.
- Even anonymous FTP accounts can be used to trigger code execution with administrative rights on both Linux and Windows systems.
- Researchers confirmed active exploitation of the flaw shortly after technical details were made public on June 30, urging users to update to server version 7.4.4 or later.
Read Full Article
8 Likes
Medium
302

How I Cracked the Mr. Robot VulnHub Machine: A Step-by-Step Walkthrough
- The article provides a step-by-step walkthrough of how the author cracked the Mr. Robot VulnHub machine.
- The process involved scanning the network and target machine using tools like nmap, nikto, and gobuster to discover vulnerabilities.
- The author utilized Burp Suite for intercepting and analyzing WordPress login requests, followed by brute-forcing credentials and achieving a reverse shell access.
- The walkthrough concludes with lessons learned and key takeaways related to web hacking, privilege escalation, tool usage, and understanding system exploitation.
Read Full Article
16 Likes
Securityaffairs
312

Image Credit: Securityaffairs
Security Affairs newsletter Round 532 by Pierluigi Paganini – INTERNATIONAL EDITION
- McDonald’s job app exposes data of 64 million applicants
- Russian basketball player accused in U.S. ransomware case
- UK NCA arrests four people over M&S, Co-op cyberattacks
- PerfektBlue Bluetooth attack allows hacking infotainment systems of Mercedes, Volkswagen, and Skoda
Read Full Article
17 Likes
Securityaffairs
113
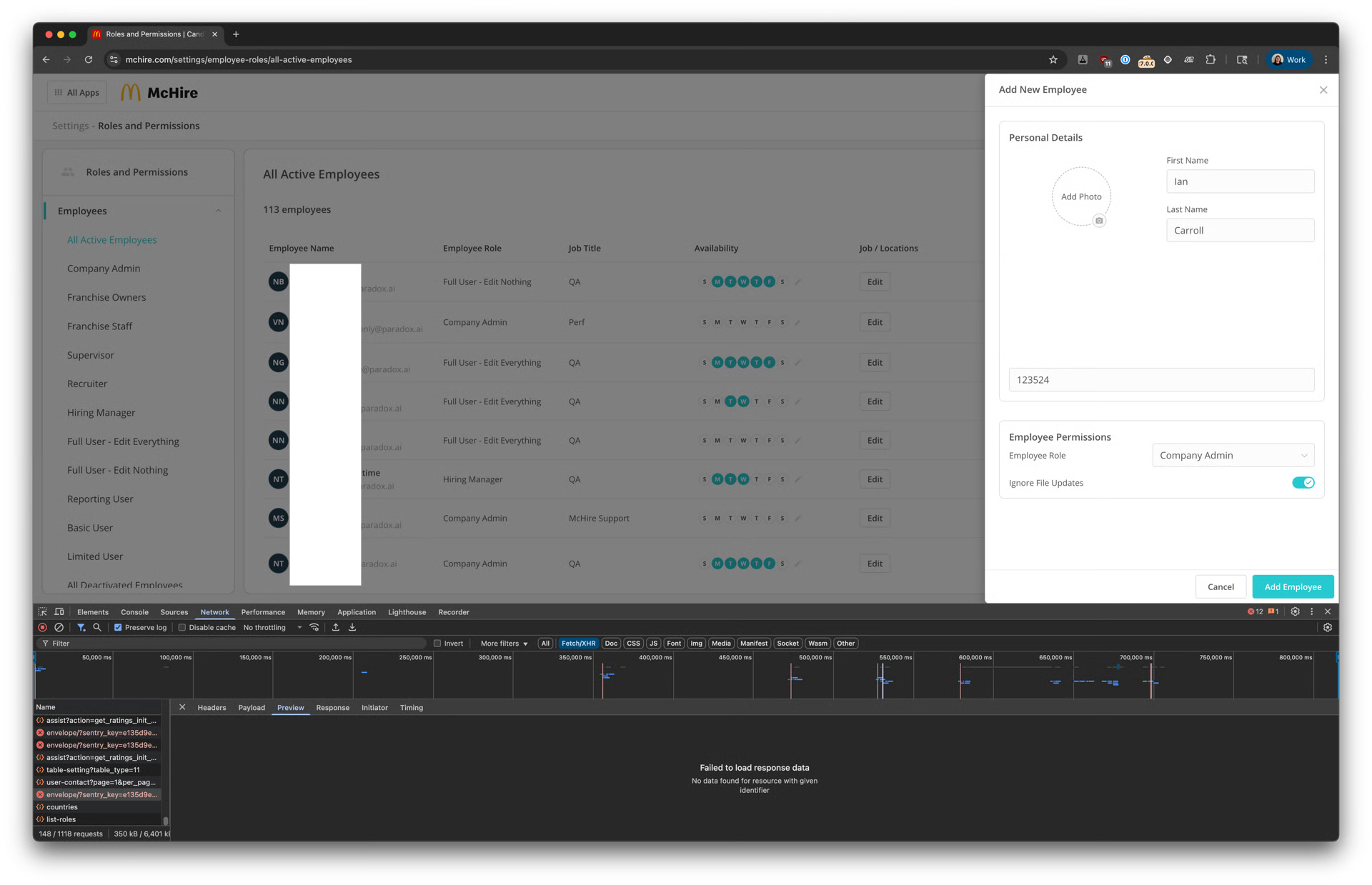
Image Credit: Securityaffairs
McDonald’s job app exposes data of 64 Million applicants
- Security researchers discovered vulnerabilities in McDonald’s McHire chatbot exposing data of over 64 million job applicants.
- Major flaws like default credentials '123456' and insecure APIs allowed access to private chats, admin privileges, and sensitive info.
- Researchers gained unauthorized access to internal data but promptly alerted Paradox.ai, who resolved the issues and enhanced security.
- McDonald's and Paradox.ai were informed of the vulnerabilities, leading to a quick response and resolution of the security concerns.
Read Full Article
6 Likes
Hackers-Arise
15

Image Credit: Hackers-Arise
Sock Puppets: Creating Fake Accounts for OSINT Operations
- Maintaining anonymity is crucial for cyberwarriors during investigations for security reasons.
- Creating and managing 'sock puppets' - fake online identities - ensures operational security.
- Using sock puppets helps in concealing intentions, social engineering, and ensuring safety.
- Essential steps include obtaining sock puppets, registration, profile creation, and building credibility.
- Develop convincing profiles with realistic details and take precautions to maintain authenticity.
Read Full Article
Like
Securityaffairs
326

Image Credit: Securityaffairs
Athlete or Hacker? Russian basketball player accused in U.S. ransomware case
- Russian basketball player Daniil Kasatkin, 26, was arrested in France at the request of the U.S. over alleged ties to a ransomware group targeting U.S. companies and federal entities.
- Kasatkin is suspected of aiding a ransomware group that targeted over 900 entities from 2020 to 2022, allegedly helping negotiate ransoms.
- Despite the accusations, Kasatkin denies all charges, with his lawyer claiming he lacks the technical skills for such involvement, having minimal computer knowledge.
- The athlete's lawyer unsuccessfully requested his release, citing health and career concerns, with Kasatkin experiencing weight loss in detention and feeling unsafe amidst the Russia-Ukraine conflict.
Read Full Article
19 Likes
Hackers-Arise
35

Image Credit: Hackers-Arise
CyberWar! Taking Over a Russian Corporate Mail
- Learn about a cyberattack on a Russian company's corporate mail system.
- Details on bypassing security measures like 2FA using tools like LaZagne.
- Exploration of network traffic analysis to uncover vulnerabilities and gain access.
- The post emphasizes the importance of monitoring internal traffic for potential compromises.
Read Full Article
2 Likes
Securityaffairs
147

Image Credit: Securityaffairs
U.S. CISA adds Citrix NetScaler ADC and Gateway flaw to its Known Exploited Vulnerabilities catalog
- The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added Citrix NetScaler ADC and Gateway flaw, known as CVE-2025-5777, to its Known Exploited Vulnerabilities catalog.
- The 'CitrixBleed 2' vulnerability with a CVSS v4.0 Base Score of 9.3 allows attackers to steal session cookies, similar to a past critical exploit.
- The flaw impacts NetScaler ADC and Gateway versions before specific fixed versions, exposing memory and potentially sensitive information.
- Citrix recommends updating to mitigate the risk as attacks exploiting CVE-2025-5777 have been observed since mid-June, with federal agencies required to address vulnerabilities by July 11, 2025.
Read Full Article
8 Likes
For uninterrupted reading, download the app