Securityaffairs
1M
113
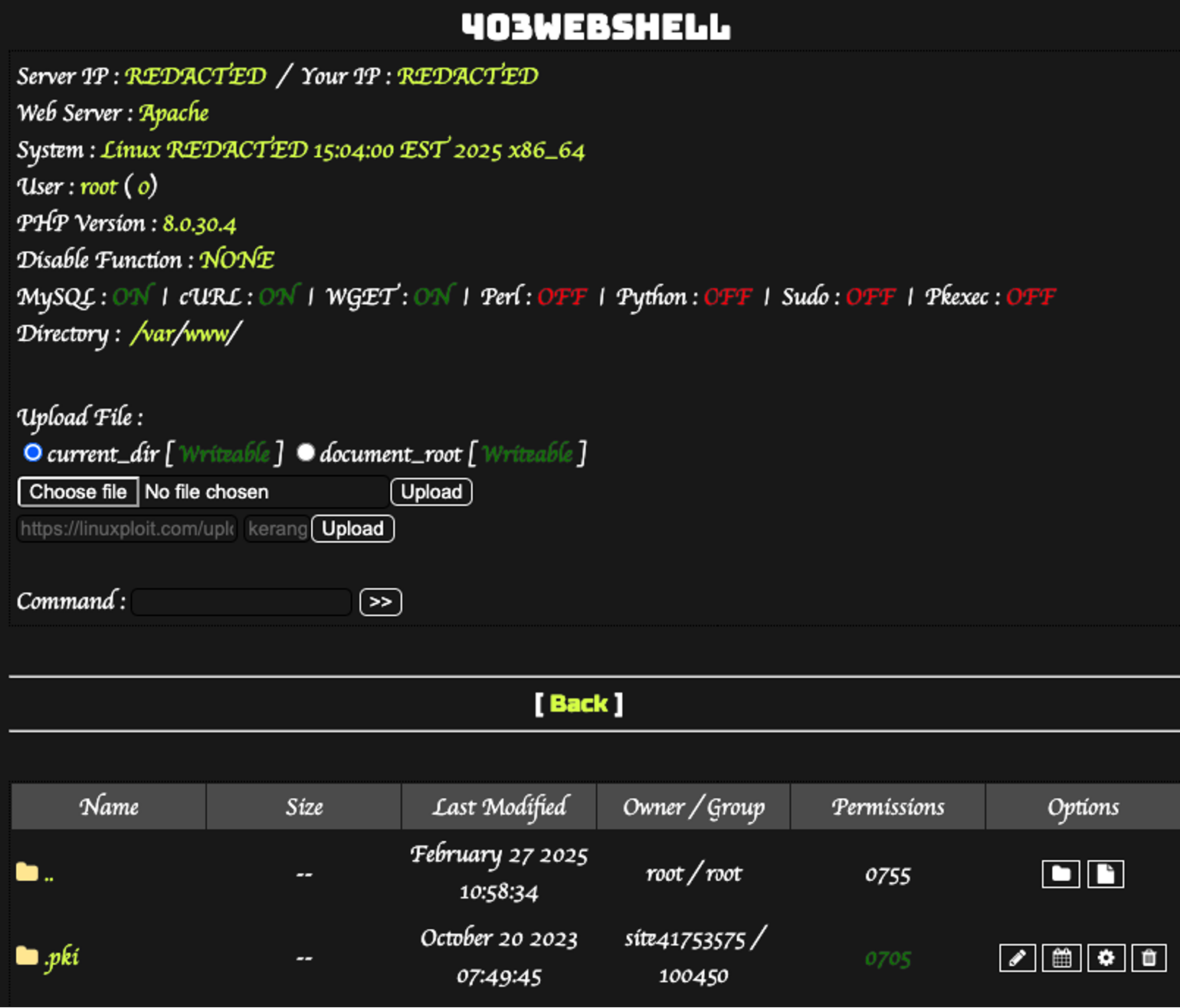
Image Credit: Securityaffairs
Hiding WordPress malware in the mu-plugins directory to avoid detection
- Threat actors are hiding WordPress malware in the mu-plugins directory to evade detection and maintain persistence.
- Unlike regular plugins, mu-plugins automatically load on every page load, making them an ideal location for backdoors.
- Attackers are using obfuscated PHP to execute hidden payloads from the mu-plugins directory, enabling them to manipulate website behavior.
- The malware found in the mu-plugins directory includes fake update redirects, webshells, and JavaScript injectors for various malicious purposes.
Read Full Article
6 Likes
For uninterrupted reading, download the app