Amazon
1M
297
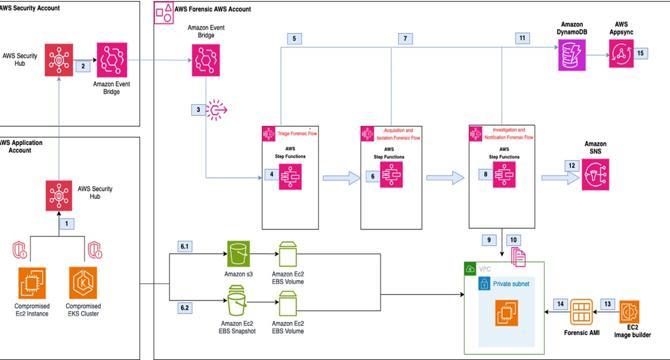
Image Credit: Amazon
How to automate incident response for Amazon EKS on Amazon EC2
- Automated incident response in AWS environments is crucial for minimizing impact, especially with standardized processes for capturing forensic evidence and quarantining resources.
- Implementing automation allows for quick and repeatable responses to security events, emphasizing the need for a defined process and understanding of actions for AWS resources.
- Differences between Amazon EC2 and EKS clusters on EC2 impact incident response automation, considering Amazon GuardDuty for security event detection.
- Understanding the relationship between EKS and EC2 is important for responding to security events such as anomalous behavior within EKS clusters.
- Accessing Amazon EKS clusters using kubectl for forensic evidence collection and managing pods on EKS clusters is essential in automated incident response.
- Capturing volatile memory is critical for determining the root cause of security events in EKS clusters, with differences in obtaining information from EC2 instances.
- Network segmentation on EKS involves isolating compromised resources using security groups, network policies, and node cordoning to protect the cluster.
- Identity and access management plays a vital role in EKS incident response, using IAM roles, service-linked roles, and Kubernetes RBAC configurations for authorization.
- Automated EKS incident response involves incorporating workflows for acquisition, isolation, and investigation using solutions like the Automated Forensics Orchestrator for Amazon EC2.
- Implementing the automated solution requires specific prerequisites and steps for deployment using AWS services like AWS CLI, CDK, and Security Hub.
Read Full Article
17 Likes
For uninterrupted reading, download the app