Amazon
1M
168
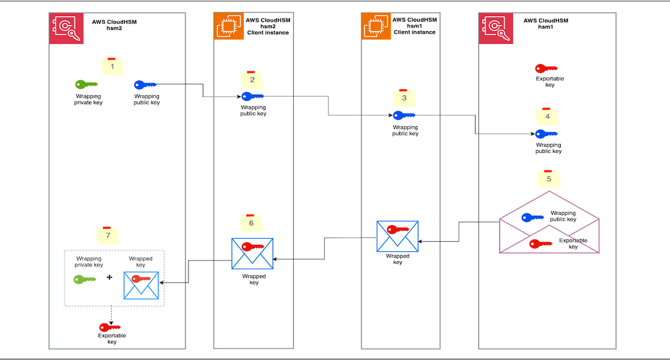
Image Credit: Amazon
How to migrate 3DES keys from a FIPS to a non-FIPS AWS CloudHSM cluster
- AWS has introduced a new CloudHSM hardware security module (HSM) instance type called hsm2 that supports Federal Information Processing Standard (FIPS) 140-3 Level 3.
- AWS CloudHSM hsm2 offers increased storage capacity of 16,666 total keys, the ability to run CloudHSM clusters in non-FIPS mode, and support for Mutual Transport Layer Security (mTLS) between CloudHSM client SDKs and the CloudHSM cluster.
- To securely and efficiently migrate Triple DES (3DES) keys from a hsm1 CloudHSM cluster to a new hsm2 cluster, the RSA-AES wrapping mechanism is suggested.
- Customers that don’t use 3DES can migrate keys to an hsm2 cluster by creating an hsm2 cluster running in FIPS mode from an hsm1 backup.
- AWS recommends migrating 3DES workloads to Advanced Encryption Standard (AES), but if this isn't feasible and you intend to continue to use 3DES, an hsm2 cluster running in non-FIPS mode can manage your 3DES keys and take advantage of the new hsm2 benefits.
- To migrate keys between CloudHSM clusters without using backups, CloudHSM CLI is used with the RSA-AES wrap mechanism.
- There are important considerations when migrating cryptographic keys, including the fact that the solution only works for exportable keys, and when a key is migrated, the crypto user who unwraps the key becomes the key owner.
- To test whether your 3DES key was migrated successfully, you can encrypt and decrypt a simple message using your migrated key to obtain plaintext that should match the original message.
- The same methodology can be used to migrate keys between many AWS CloudHSM cluster pairs and can be extended to other CloudHSM SDKs, like JCE and PKCS #11, to automate the migration process.
- To migrate keys from on-premises or other non AWS HSMs to AWS CloudHSM, the same principle of wrap and unwrap can be applied.
Read Full Article
10 Likes
For uninterrupted reading, download the app