Securityaffairs
20h
92
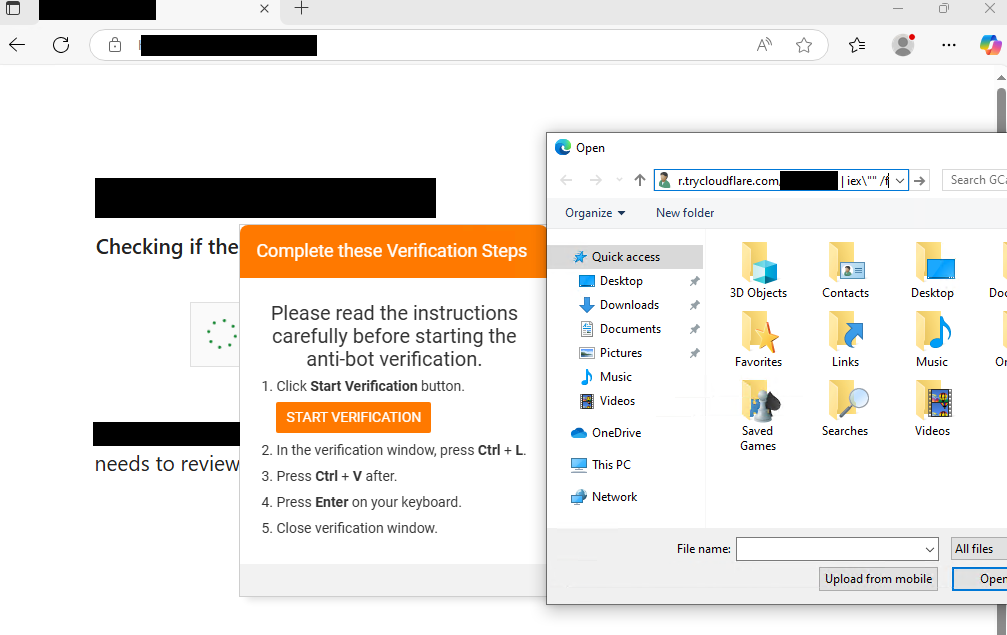
Image Credit: Securityaffairs
Interlock ransomware group deploys new PHP-based RAT via FileFix
- The Interlock ransomware group has deployed a new PHP-based variant of the Interlock RAT through a campaign using a delivery method known as FileFix, targeting various industries as reported by researchers.
- The PHP variant, which emerged in June and is distinct from the previous JavaScript-based version, spreads through compromised websites using hidden scripts to deceive victims into running a PowerShell script to install the malware.
- The Interlock RAT, once deployed, conducts system reconnaissance, checks privilege levels, exfiltrates system info, establishes a command and control channel through trycloudflare.com URLs, and supports various commands for malicious activities such as lateral movement via RDP.
- The campaign showcases the Interlock group's evolving tactics and operational sophistication, moving from Node.js to PHP for access to victim networks. Researchers have provided Sigma and YARA rules along with IOCs for identification.
Read Full Article
5 Likes
For uninterrupted reading, download the app