Securityaffairs
1M
433
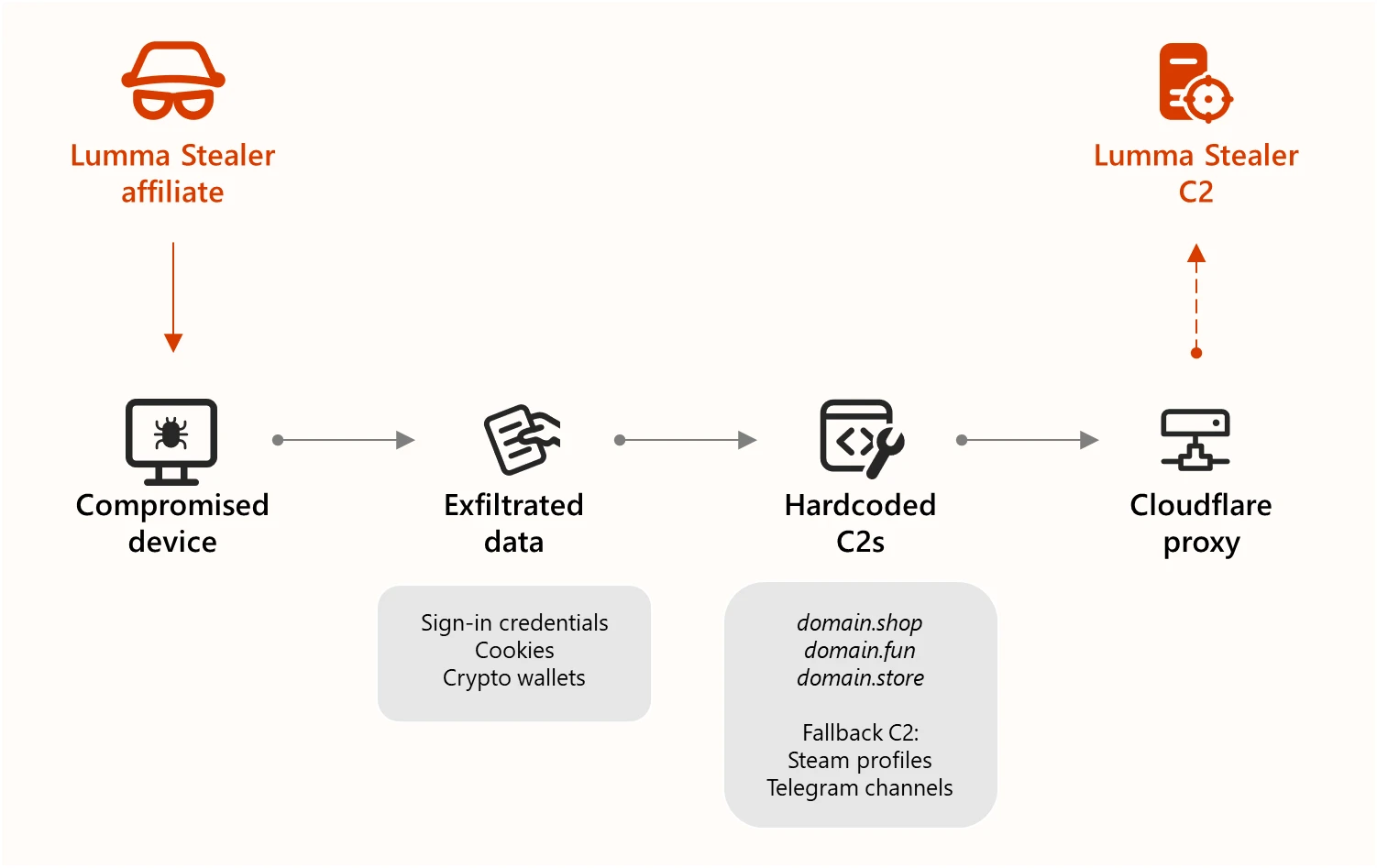
Image Credit: Securityaffairs
Law enforcement dismantled the infrastructure behind Lumma Stealer MaaS
- Law enforcement, with the help of Microsoft, Europol, and Japan’s JC3, dismantled the infrastructure behind Lumma Stealer Malware-as-a-Service (MaaS) operation, seizing 2,300 domains used for command-and-control.
- The malware, known as Lumma Stealer, targeted over 394,000 Windows systems, including those of global manufacturers, to steal sensitive data like passwords, credit card information, and crypto wallet keys.
- Microsoft's Digital Crimes Unit sinkholed over 1,300 domains used by Lumma Stealer to reroute victims to safe servers for analysis and cleanup, showcasing the collaboration between law enforcement and tech companies against cyber threats.
- The FBI and US CISA released a joint advisory containing tactics, techniques, and procedures associated with Lumma Stealer, along with indicators of compromise (IOCs), emphasizing the importance of public-private partnerships in combating cybercrime.
Read Full Article
26 Likes
For uninterrupted reading, download the app