Securityaffairs
4w
199
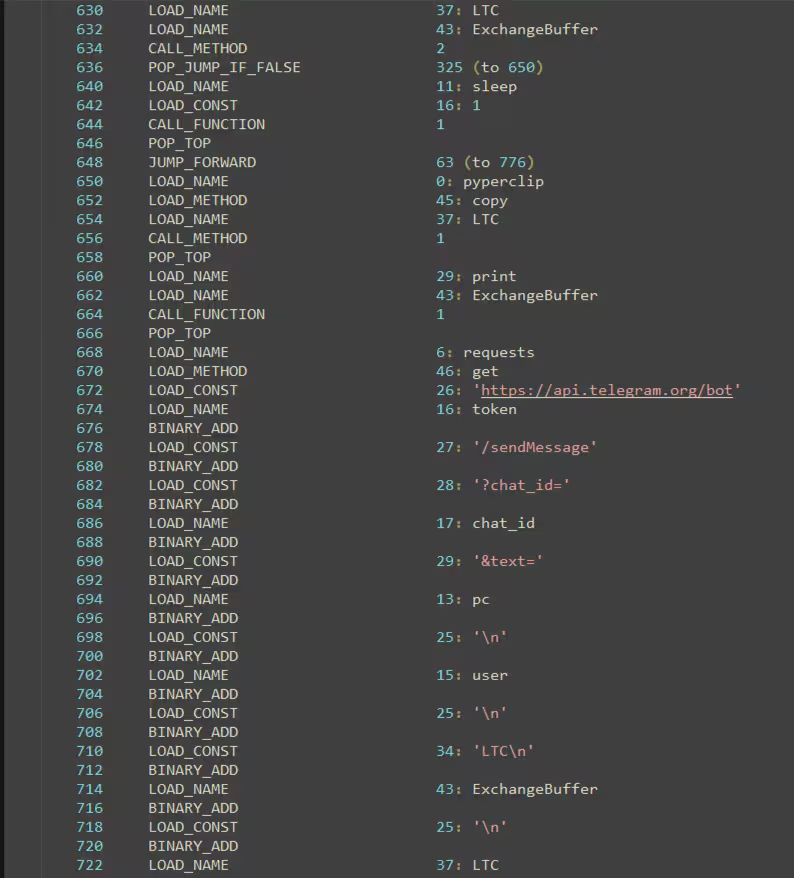
Image Credit: Securityaffairs
Mass exploitation campaign hit 4,000+ ISP networks to deploy info stealers and crypto miners
- A mass exploitation campaign originating from Eastern Europe has targeted ISPs in China and the U.S. West Coast.
- The threat actors gain access through weak credential brute-force and deploy info stealers and crypto miners.
- The malware disables remote access and uses PowerShell to drop binaries and disable security features.
- The campaign focuses on ISPs in China and the U.S. West Coast, and the malware sends data to its C2 server via a Telegram bot.
Read Full Article
12 Likes
For uninterrupted reading, download the app