Securityaffairs
1M
109
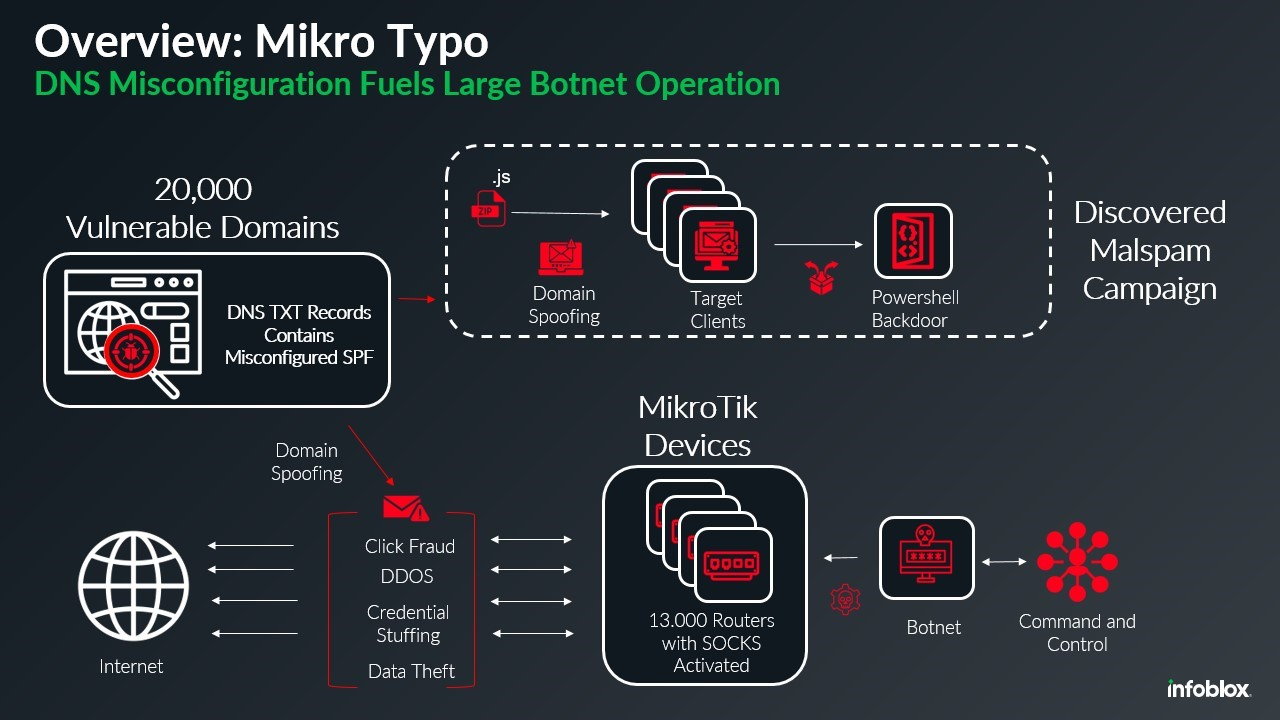
Image Credit: Securityaffairs
MikroTik botnet relies on DNS misconfiguration to spread malware
- Researchers discovered a 13,000-device MikroTik botnet exploiting DNS flaws to spoof 20,000 domains and deliver malware.
- The botnet comprises MikroTik routers with various firmware versions, including recent ones.
- The botnet uses compromised MikroTik devices as SOCKS proxies, masking malicious traffic origins.
- The botnet operators exploit an improperly configured DNS record for the sender policy framework (SPF) to enable spoofing.
Read Full Article
6 Likes
For uninterrupted reading, download the app