Securityaffairs
1M
410
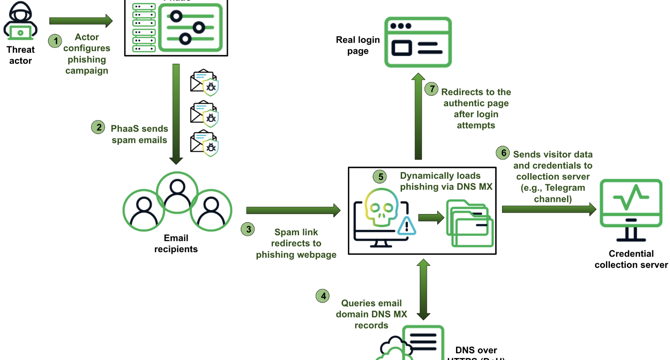
Image Credit: Securityaffairs
Morphing Meerkat phishing kits exploit DNS MX records
- Morphing Meerkat phishing kits exploit DNS MX records to deliver spoofed login pages, targeting over 100 brands.
- A new phishing-as-a-service (PhaaS) platform called Morphing Meerkat has been discovered, which generates multiple phishing kits using DNS mail exchange (MX) records.
- Threat actors use MX records to serve dynamically tailored fake login pages, abusing open redirects and compromised domains.
- Morphing Meerkat enables large-scale phishing campaigns, using obfuscated code and dynamic translations, and distributing stolen credentials via email and chat.
Read Full Article
24 Likes
For uninterrupted reading, download the app