Securityaffairs
3w
185
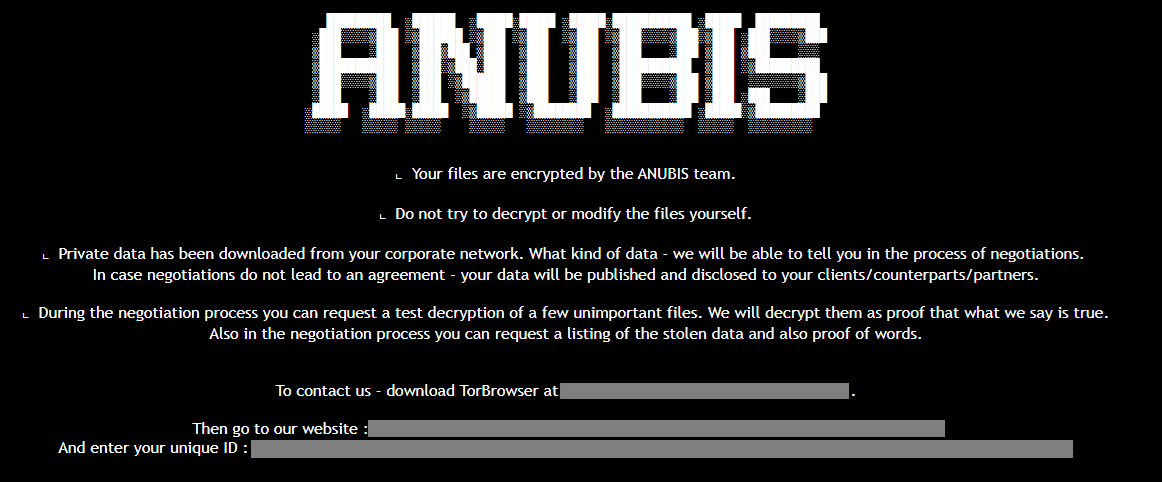
Image Credit: Securityaffairs
New Anubis RaaS includes a wiper module
- Anubis RaaS now includes a wiper module, permanently deleting files and preventing recovery even after ransom payment.
- Active since December 2024, Anubis launched an affiliate program in February 2025, breaching organizations in various sectors like healthcare and construction.
- It combines file encryption with a rare 'wipe mode,' erasing data effectively, as per a report by Trend Micro.
- Anubis evolved from an earlier variant called Sphinx, offering multiple monetization paths, including data theft and access resale.
- The ransomware operates with the ECIES encryption scheme and uses double extortion tactics, threatening to leak data if ransom demands are not met.
- Upon activation of the wiper mode, files are left with a 0 KB size, indicating complete erasure.
- Anubis supports various commands for privilege escalation, directory exclusion, and targeted encryption, ensuring successful data encryption.
- The ransomware's use of dual-threat capabilities and flexible affiliate programs represents a significant evolution in cyberthreat landscape, maximizing revenue potential and victim pressure.
- Trend Micro released a list of indicators of compromise (IoCs) related to the Anubis threat.
Read Full Article
11 Likes
For uninterrupted reading, download the app