Securityaffairs
1M
9
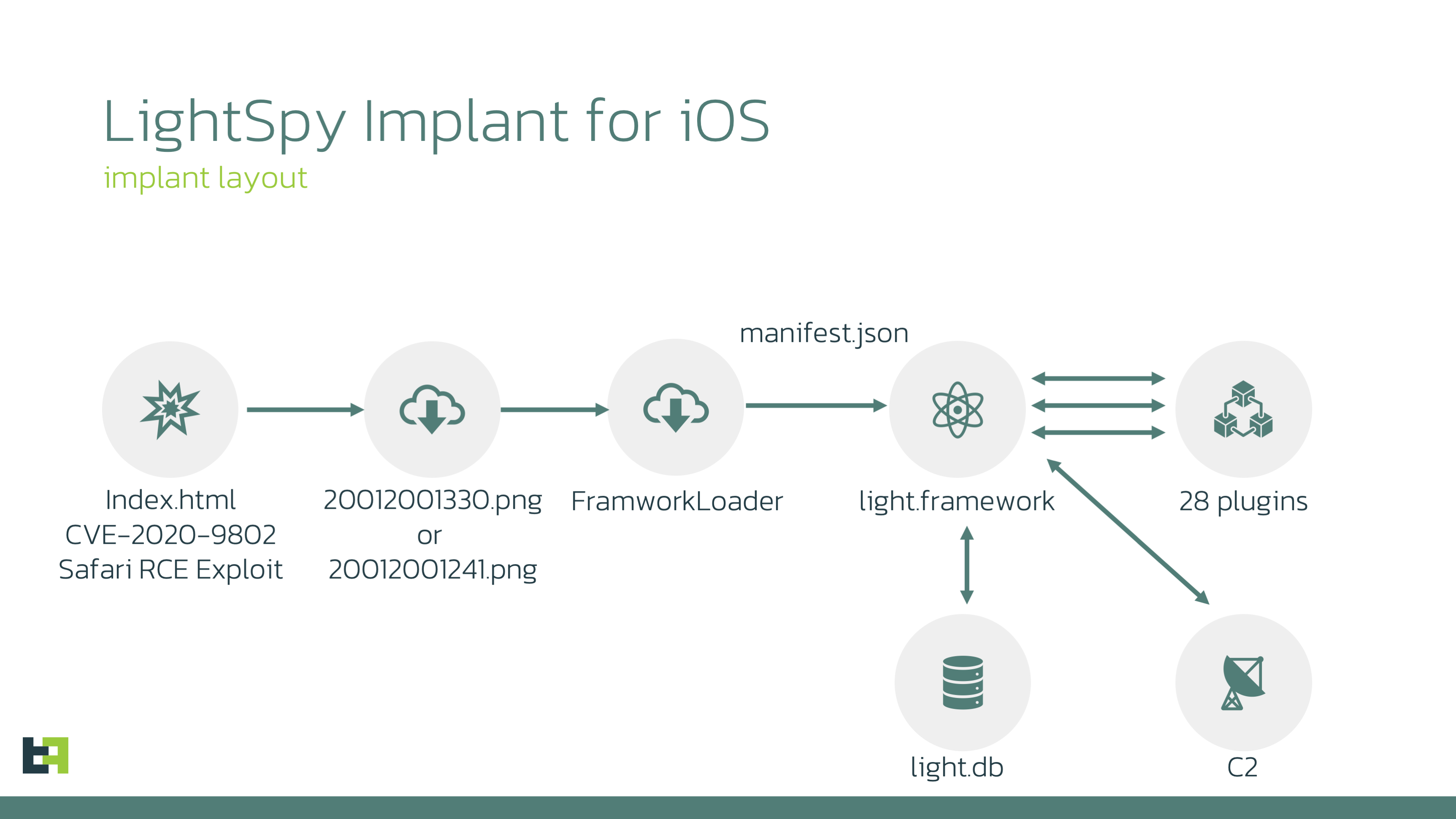
Image Credit: Securityaffairs
New LightSpy spyware version targets iPhones with destructive capabilities
- The new LightSpy spyware version, which targets iOS devices, has destructive abilities that allow it to block compromised devices from booting up.
- This modular spyware can steal files from popular applications, record audio, harvest browser history, and more.
- The updated iOS version of LightSpy has expanded plugins to 28, from 12 before, including 7 that disrupt device booting.
- The iOS version of this spyware targets platforms up to version 13.3, and it gains initial access with the Safari exploit CVE-2020-9802 and for privilege escalation with CVE-2020-3837.
- This spyware is capable of deleting media files, SMS messages, and contacts, freezing devices, and preventing restarts. Some of the above plugins can simulate fake push notifications with specific URLs.
- The authors of this spyware used five active C2 servers, and some samples labeled 'DEMO' suggest that the infrastructure might be used for demonstration rather than active deployment.
- The delivery method for the iOS implant is similar to that of the macOS version, but the two versions rely on different post-exploitation and privilege escalation stages.
- The researchers suggest that watering hole attacks may be the method of distribution, and they believe the operators have a Chinese origin.
- Since the threat actors use a 'Rootless Jailbreak' — which doesn't survive a device reboot — a regular reboot may provide some protection for Apple device users.
- Evidence collected by the researchers suggests that this spyware was developed by the same team that designed the macOS version.
Read Full Article
Like
For uninterrupted reading, download the app