Securityaffairs
1M
284
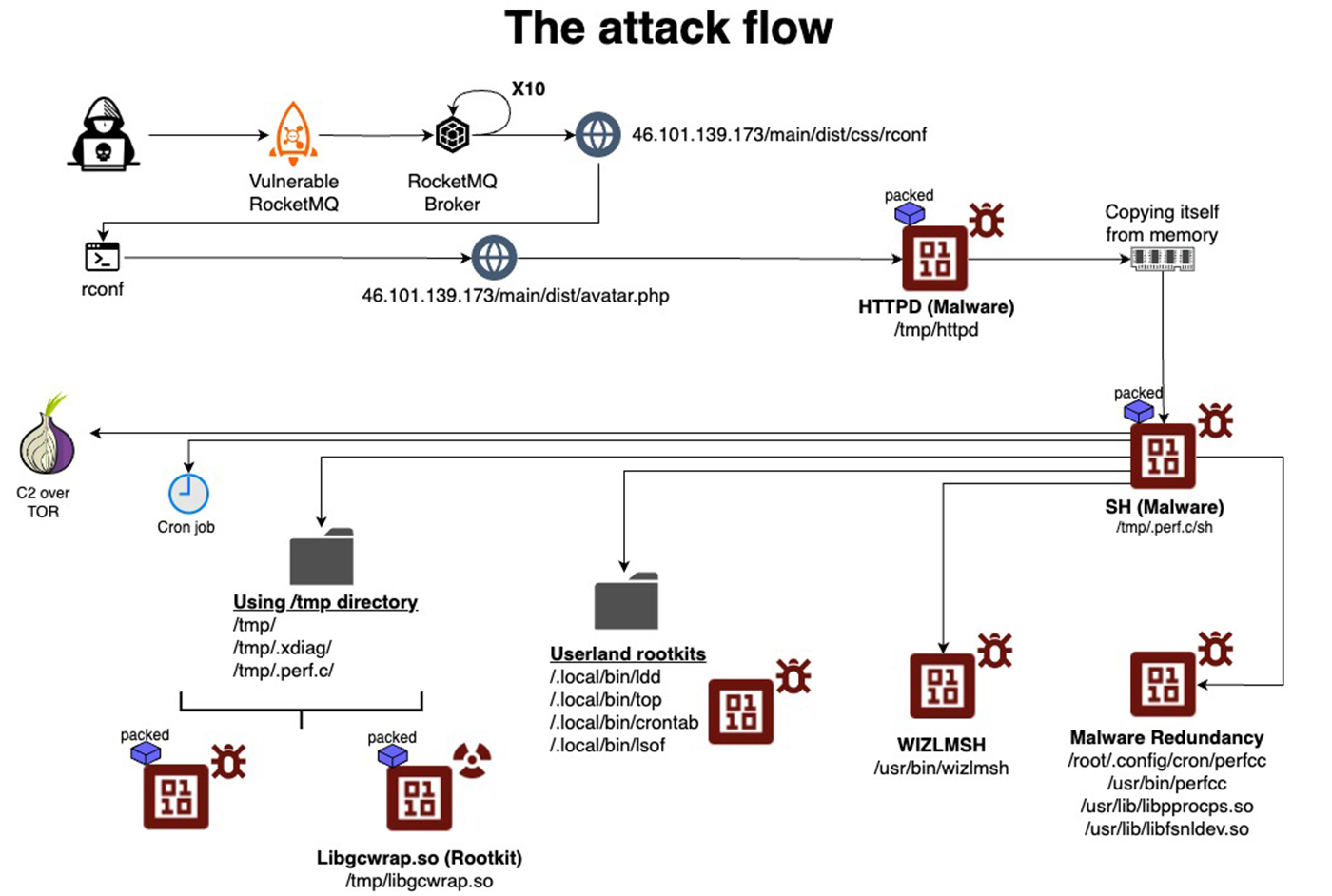
Image Credit: Securityaffairs
New Perfctl Malware targets Linux servers in cryptomining campaign
- Perfctl malware targets misconfigured Linux servers to deploy cryptocurrency miners and proxyjacking software.
- The malware employs rootkits to conceal its presence and operates as a service in the background.
- It downloads the main payload from an attacker-controlled server and utilizes advanced evasion techniques to bypass detection.
- The main impact is resource hijacking, with the malware running a monero cryptominer to exhaust CPU resources.
Read Full Article
17 Likes
For uninterrupted reading, download the app