Hackingblogs
2M
110
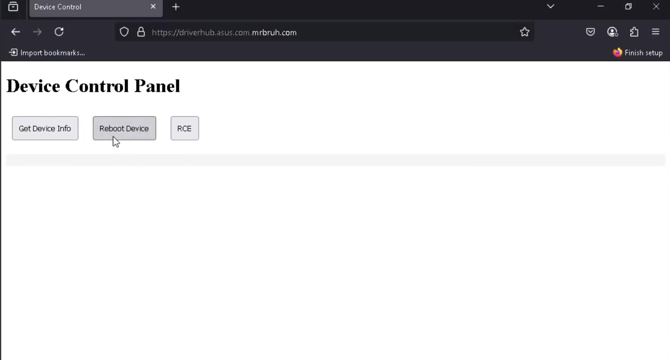
Image Credit: Hackingblogs
One-Click Exploit: ASUS DriverHub RCE Vulnerability Exposes Admin Access
- Security researcher Paul discovered a critical ASUS DriverHub RCE vulnerability that allows attackers to execute code with admin privileges by tricking users into visiting a malicious website.
- DriverHub, a background process by ASUS, interacts with the website driverhub.asus.com using Remote Procedure Calls (RPC) instead of a graphical user interface.
- Key findings of the vulnerability include DriverHub hosting a local HTTP service, vulnerability in Origin header validation, and exploitable endpoints like InstallApp and UpdateApp which is the basis of the exploit.
- The exploit chain involves making an UpdateApp request to download a harmless-looking executable, injecting INI files, and executing a signed executable with admin rights, demonstrating the severity of the ASUS DriverHub RCE vulnerability.
Read Full Article
6 Likes
For uninterrupted reading, download the app