Securityaffairs
2w
86
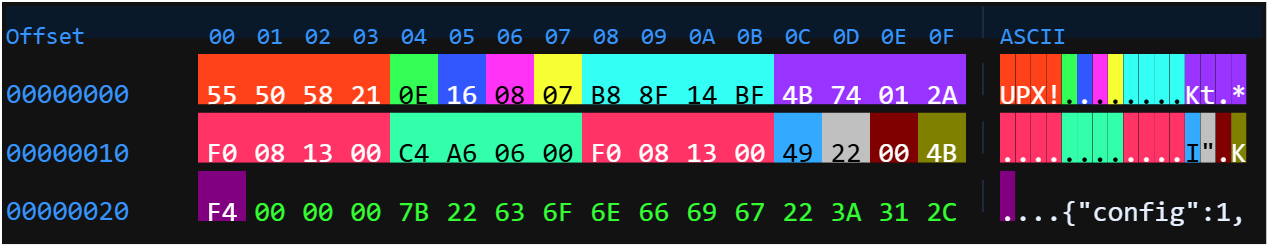
Image Credit: Securityaffairs
Prometei botnet activity has surged since March 2025
- Prometei botnet activity has surged since March 2025, with a new malware variant rapidly spreading, according to Palo Alto Networks.
- The botnet targets Linux systems for Monero mining and credential theft, using modular architecture and evasion tactics to avoid detection.
- Prometei allows attackers to control compromised systems for cryptocurrency mining and credential theft, with a focus on the Linux variant.
- First discovered in 2020, Prometei exploits vulnerabilities like EternalBlue and spreads through brute-force attacks.
- The malware primarily focuses on Monero mining and credential theft, displaying financial motivations without state ties.
- The latest Prometei variant is distributed via an HTTP GET request, utilizing UPX-packed Linux ELF files disguised as .php scripts.
- Prometei malware uses Ultimate Packer for eXecutables (UPX) for obfuscation, requiring analysts to strip a JSON config trailer for static analysis.
- Analyzing the configuration JSON reveals system information collected by the malware, including processor, motherboard, OS, uptime, and kernel details.
- Detection of the evolving Prometei botnet can be done with YARA rules targeting UPX and its configuration JSON trailer, but defenders must remain alert.
- The report provides Indicators of Compromise (IoCs) related to the Prometei botnet activity.
Read Full Article
5 Likes
For uninterrupted reading, download the app