Securityaffairs
2M
302
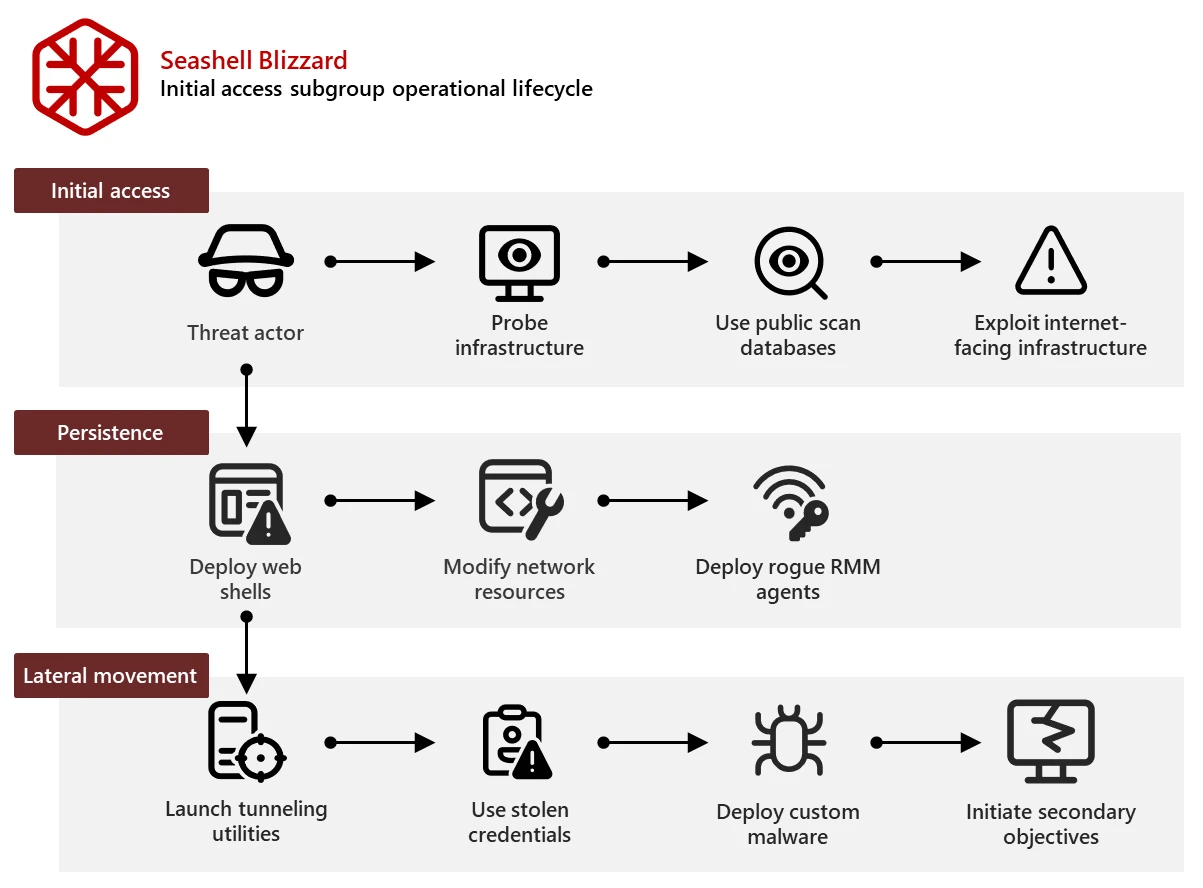
Image Credit: Securityaffairs
Russia-linked APT Seashell Blizzard is behind the long running global access operation BadPilot campaign
- A subgroup of the Russia-linked Seashell Blizzard APT group (aka Sandworm) ran a global multi-year initial access operation called BadPilot.
- Microsoft shared findings on research on a subgroup of the Russia-linked APT group Seashell Blizzard behind the global BadPilot campaign, which compromises infrastructure to support Russian cyber operations.
- The subgroup of Seashell Blizzard APT group compromised multiple Internet-facing infrastructures to enable persistence in the networks of high-value targets and support tailored network operations.
- The subgroup exploited known vulnerabilities on network perimeters of small office/home office (SOHO) and enterprise networks to maintain persistence and gain access to targets.
Read Full Article
18 Likes
For uninterrupted reading, download the app