Securityaffairs
1M
324
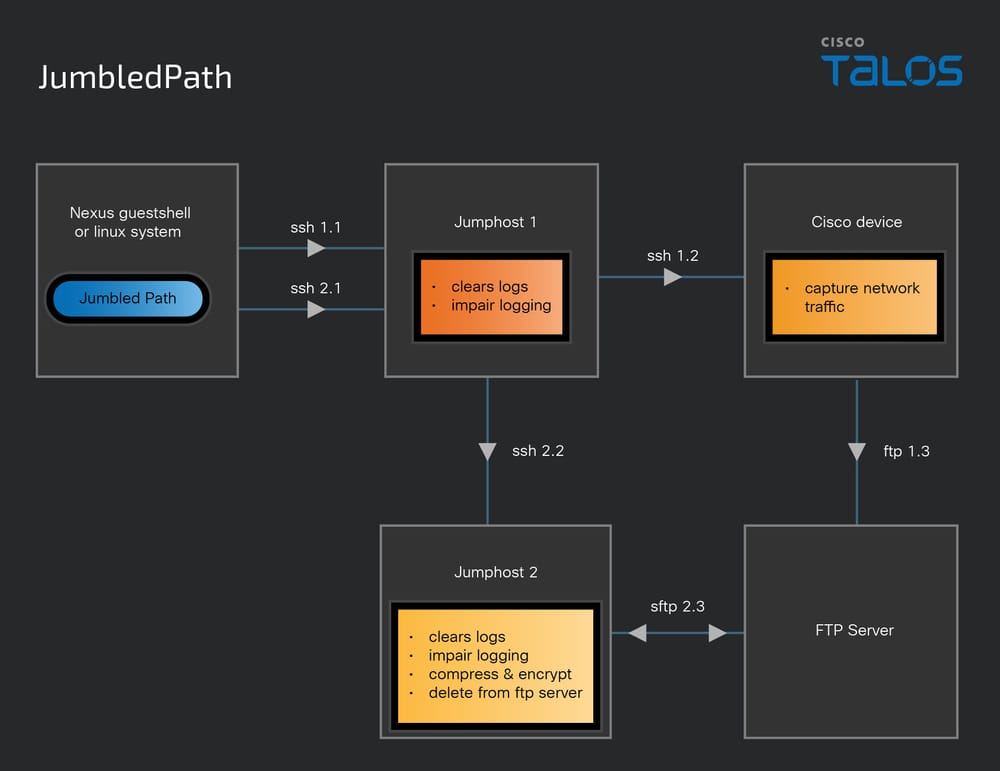
Image Credit: Securityaffairs
Salt Typhoon used custom malware JumbledPath to spy U.S. telecom providers
- China-linked APT group Salt Typhoon utilizes custom malware JumbledPath to spy on U.S. telecom providers, as reported by Cisco Talos researchers.
- The APT group has been active since at least 2019, targeting government entities and telecom companies globally.
- Salt Typhoon exploited Cisco vulnerabilities, breached U.S. telecom networks, and utilized GRE tunnels for data exfiltration.
- Stolen credentials, network config captures, and intercepted traffic were used by Salt Typhoon for further access inside networks.
- The group manipulated network settings, used JumbledPath tool for packet capture, and attempted evasion techniques.
- In December 2024, Salt Typhoon targeted a Myanmar-based telecom provider, with IOCs and mitigation recommendations provided in the report.
- The group also compromised Charter Communications and Windstream, exploiting vulnerabilities in major network device vendors.
- Salt Typhoon breached a ninth U.S. telecom as part of a global cyberespionage campaign aimed at telco firms, confirmed by a White House official.
- President Biden's national security adviser disclosed breaches in telecommunications companies globally by the China-linked APT group.
- Lumen, AT&T, and Verizon reported securing networks post-cyberespionage attempts by Salt Typhoon, active for 1-2 years targeting telcos worldwide.
Read Full Article
19 Likes
For uninterrupted reading, download the app