Medium
2w
81
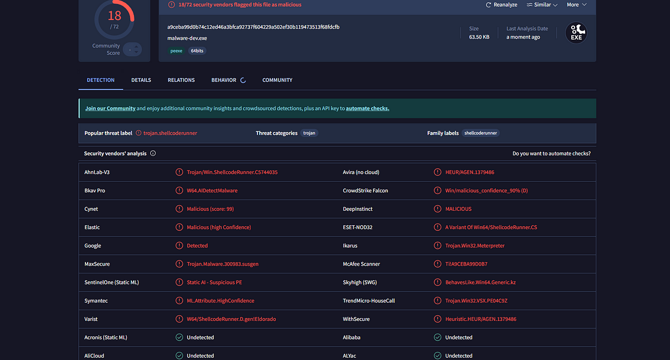
Image Credit: Medium
Thought about Anti-Debugging in Malware Development
- The developer explored anti-debugging techniques in malware development using C/C++ programming language.
- The Windows API function IsDebuggerPresent() was used to detect the presence of a debugger.
- The IsDebuggerPresent() function returns a non-zero value if a debugger is present.
- Sample code demonstrated how this function can be utilized to determine the presence of a debugger.
- The code successfully detected the presence or absence of a debugger.
- The effectiveness of this technique against experienced individuals remains a question.
- A VirusTotal scan easily detected the malicious nature of the program created.
- The project served as a valuable learning experience.
- The developer acknowledged the limitations of relying solely on this strategy in a red team situation.
- The news did not provide detailed information on the specific anti-debugging techniques used.
- The article includes output examples showcasing detection with and without a debugger.
- The final code snippet shared excluded the shellcode intentionally.
- The developer remains cautious about the effectiveness of this technique in high-security environments.
- The project highlighted the need for more advanced evasion strategies in red team scenarios.
- The anti-debugging exploration focused on basics and may not be sufficient for sophisticated threat actors.
- The technique may serve as a starting point for those interested in malware evasion tactics.
Read Full Article
4 Likes
For uninterrupted reading, download the app