Medium
1M
428
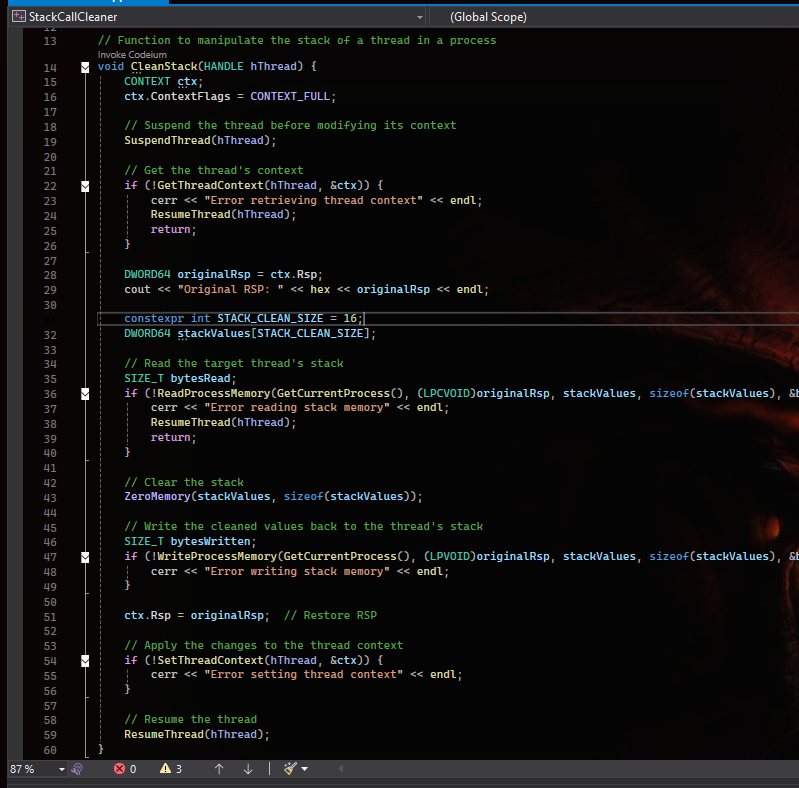
Image Credit: Medium
Thread Call Stack Cleaning
- Stack cleaning is a technique used to remove traces of injected or suspicious execution paths from a thread's call stack.
- By manipulating the return addresses in the call stack, stack cleaning can help malware evade detection by security tools.
- The process involves suspending the thread, retrieving the execution context, reading memory from the stack, zeroing out the stack values, and restoring the original context.
- Stack cleaning combined with other evasion techniques can improve stealth and persistence of malware, but advanced security solutions can still detect suspicious activity.
Read Full Article
25 Likes
For uninterrupted reading, download the app