TroyHunt
19h
337
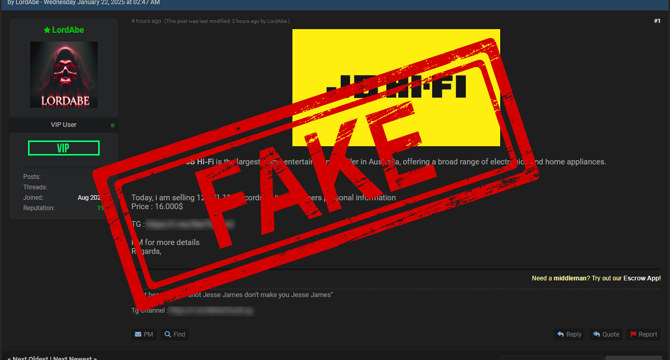
Image Credit: TroyHunt
You Can't Trust Hackers, and Other Data Breach Verification Tales
- A cybersecurity researcher shares his experience of verifying a data breach claim made by a hacker.
- The researcher contacted the hacker to verify a data breach incident related to an electronics retailer.
- Upon investigation, the researcher found that the provided data sample had common breaches with other incidents.
- The hacker's claim was disproved by comparing it to a previous breach, leading to the scammer being exposed.
Read Full Article
20 Likes
For uninterrupted reading, download the app