Cyber Crime News
Securityaffairs
262

Image Credit: Securityaffairs
Security Affairs newsletter Round 523 by Pierluigi Paganini – INTERNATIONAL EDITION
- 437,329 patients' personal data exposed in Ascension cyberattack.
- Operation Moonlander dismantles cybercriminal services Anyproxy and 5socks.
- SonicWall fixes critical flaws in SMA 100.
- NSO Group ordered to pay over $167M to WhatsApp for spyware campaign.
Read Full Article
15 Likes
Minis
510

Image Credit: Minis
BeerBiceps aka Ranveer Allahbadia breaks silence on his channels getting hacked: ‘Is this the end of my YouTube career’
- Popular YouTuber Ranveer Allahbadia, known as BeerBiceps, recently had his YouTube channels hacked.
- Cyber attackers deleted all his podcasts and interviews, replacing them with old streams of Elon Musk and Donald Trump. His channels were renamed “@Elon.trump.tesla_live2024” and “@Tesla.event.trump_2024,” but both have since been removed by YouTube.
- Reacting on Instagram, Ranveer humorously posted about the incident while enjoying vegan burgers and questioned, “Is this the end of my YouTube career?” Ranveer, who started his content journey at 22, manages seven channels with a combined 12 million subscribers.
Read Full Article
24 Likes
Minis
7.7k

Image Credit: Minis
Passwords Leaked: Hackers post file with 1,000 crore passwords online in biggest cyber security breach yet
- A massive cyber security breach has exposed a file containing approximately 10 billion passwords on an online hacking forum.
- The compilation, posted on July 4, includes both old and new password breaches, making it the largest such leak to date. The leak raises significant concerns about credential stuffing attacks, where hackers use a breached password to access multiple accounts.
- An IMF report highlights that malicious cyberattacks have doubled globally since 2020, particularly targeting the financial and healthcare sectors. Despite the leak's magnitude, some experts believe the file's size may render it less effective for attacks.
Read Full Article
41 Likes
Minis
2.6k

Image Credit: Minis
Shadowy hacker claims he has data of 375 million Airtel users, Airtel says no breach in its systems
- A hacker claims to possess data of 375 million Airtel users, including sensitive information like phone numbers, Aadhaar numbers, and more.
- Airtel denies any breach, attributing the claim to misinformation aimed at damaging its reputation. The alleged data sale surfaced on forums frequented by cybercriminals, sparking concerns despite Airtel's assurances.
- Security experts debate the validity of the claim, urging vigilance in cyber hygiene practices like password updates, monitoring accounts, enabling 2FA, and avoiding phishing. Airtel emphasizes its systems' security while acknowledging past data breaches in Indian companies.
Read Full Article
24 Likes
Minis
1.3k
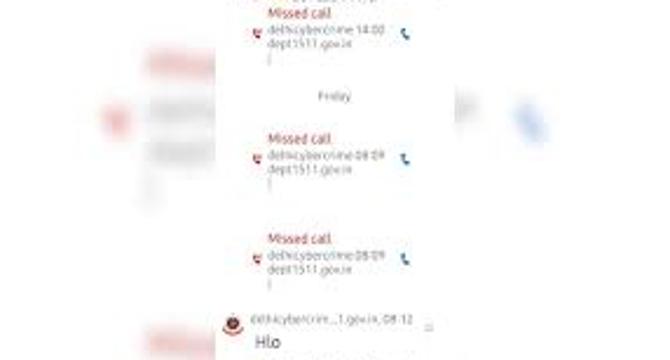
Image Credit: Minis
Fake CBI, police officers threaten woman on Skype, wipe her bank account in Kolkata
- A Kolkata company secretary lost ₹51,000 to scammers posing as Delhi Police and CBI officers. They claimed she had 35 bank accounts involved in money laundering.
- The scammers coerced her into transferring money for "verification" via Skype, threatening arrest. She sent the money to an account in Andhra Pradesh and later realized the fraud, filing complaints with Kolkata police and on a cybercrime portal.
- Similar cases across India have surfaced, with victims losing large sums. Critics argue banks need stricter KYC monitoring, suspecting insider involvement in some cases. Victims have questioned the slow investigative response.
Read Full Article
23 Likes
Minis
816
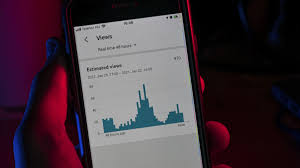
Image Credit: Minis
Chinese man uses 4,600 phones to fake live-stream views, earns over ₹ 3 crore in 4 months
- A Chinese man has been sentenced to one year and three months in prison and fined $7,000 for using 4,600 phones to fake live-stream views, earning over ₹3 crore in just four months.
- Wang's scheme, known as "brushing," involved inflating viewer counts to simulate genuine interactions. He purchased phones controlled by cloud software and network equipment, profiting by selling his service to live-streamers.
- Authorities are investigating Wang and 17 others for breaking regulations and disrupting market order. This case sheds light on the prevalence of online fraud and the measures needed to combat it effectively.
Read Full Article
13 Likes
Minis
759
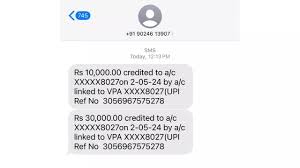
Image Credit: Minis
Bengaluru techie shares new fraud criminals are using to steal your money
- As online fraud cases surge, Bengaluru-based entrepreneur Aditi shared a cautionary tale on X, warning about a new scam tactic exploiting SMS messages.
- During an office call, Aditi received a call from someone claiming to transfer money to her father. After receiving SMS alerts mimicking bank notifications, the caller alleged mistakenly sending Rs 30,000 instead of Rs 3,000 and urged Aditi to return the excess. Alert to discrepancies in the SMS alerts, Aditi avoided the scam.
- This incident underscores the need for vigilance, urging individuals to verify transactions through secure channels, as reliance on SMS notifications alone can be exploited by cybercriminals.
Read Full Article
4 Likes
Minis
1.4k

Image Credit: Minis
What is ‘Digital Arrest’, a new form of cybercrime?
- "Digital Arrest" is a new form of cybercrime where scammers, posing as law enforcement officers, use virtual platforms like Skype to intimidate and manipulate victims.
- In recent cases reported by cyber police across several states in India, scammers falsely accused individuals of involvement in crimes like money laundering, presenting fabricated documents and conducting virtual interrogations.
- To create a convincing illusion, scammers set up virtual police stations during Skype calls. Victims are coerced into transferring funds, taking loans, and even virtually signing fake documents under the guise of aiding investigations. This emerging cybercrime tactic exploits fear and misinformation, leading to significant financial losses.
Read Full Article
10 Likes
Minis
547
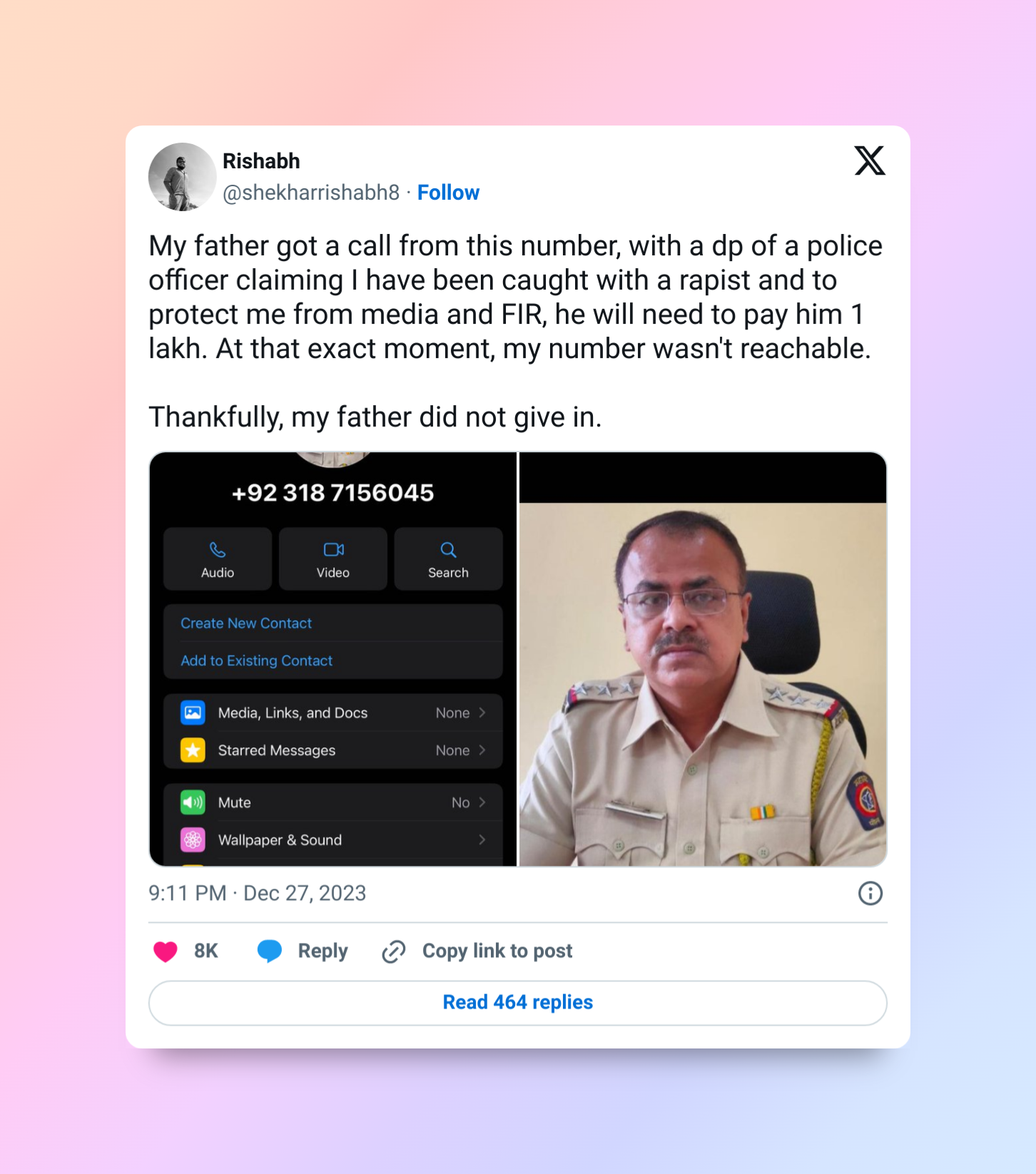
Image Credit: Minis
Pepper Content COO says a 'cop' told his father he was caught with rapist, demanded Rs 1 lakh
- A Pepper Content COO, Rishabh Shekhar, reported an extortion call targeting his father, where an alleged police officer demanded Rs 1 lakh. The caller claimed Shekhar was caught with a rapist, threatening an FIR.
- Shekhar shared a screenshot with the +92 Pakistan country code. The scam used a Pune Police officer's image. Mumbai Police advised reporting to the nearest station. Shekhar emphasized the need to combat such scams, urging awareness.
- Others shared similar experiences, including a doctor who faced a similar issue with no response despite contacting authorities. Such scams pose serious threats, demanding increased vigilance and crackdowns.
Read Full Article
29 Likes
Minis
383

Image Credit: Minis
How a Ghaziabad gang led by an MBA graduate scammed US citizens
- A gang of 24 individuals, led by an MBA graduate named Ankur Gupta, has been arrested for operating a call centre in Bisrakh and scamming US citizens by offering false policy renewals and technical assistance.
- The gang obtained phone numbers and insurance records from the dark web, made around 1,500 calls per day, and earned approximately Rs 10 lakh through their fraudulent activities.
- The Noida police, with assistance from US investigating agencies, apprehended the gang after receiving a tip-off, seizing cars, laptops, phones, and foreign currencies.
Read Full Article
22 Likes
Minis
1.1k

Image Credit: Minis
IT services companies chase large deals for higher revenue, faster growth
- Indian IT giants like Wipro, Infosys, HCLTech, and TCS are focusing on securing large and mega deals, with an emphasis on contracts above $100 million.
- Wipro's CEO Thierry Delaporte is steering the company away from smaller, less lucrative clients, leading to a surge in both the number and size of deals, including two half-a-billion-dollar contracts.
- Infosys hit its highest-ever Total Contract Value (TCV) of large deals at $7.7 billion in Q2, contributing to a remarkable $10 billion TCV for H1 FY24, driven by deals centered on cost, efficiency, and advanced technologies.
Read Full Article
19 Likes
Minis
411
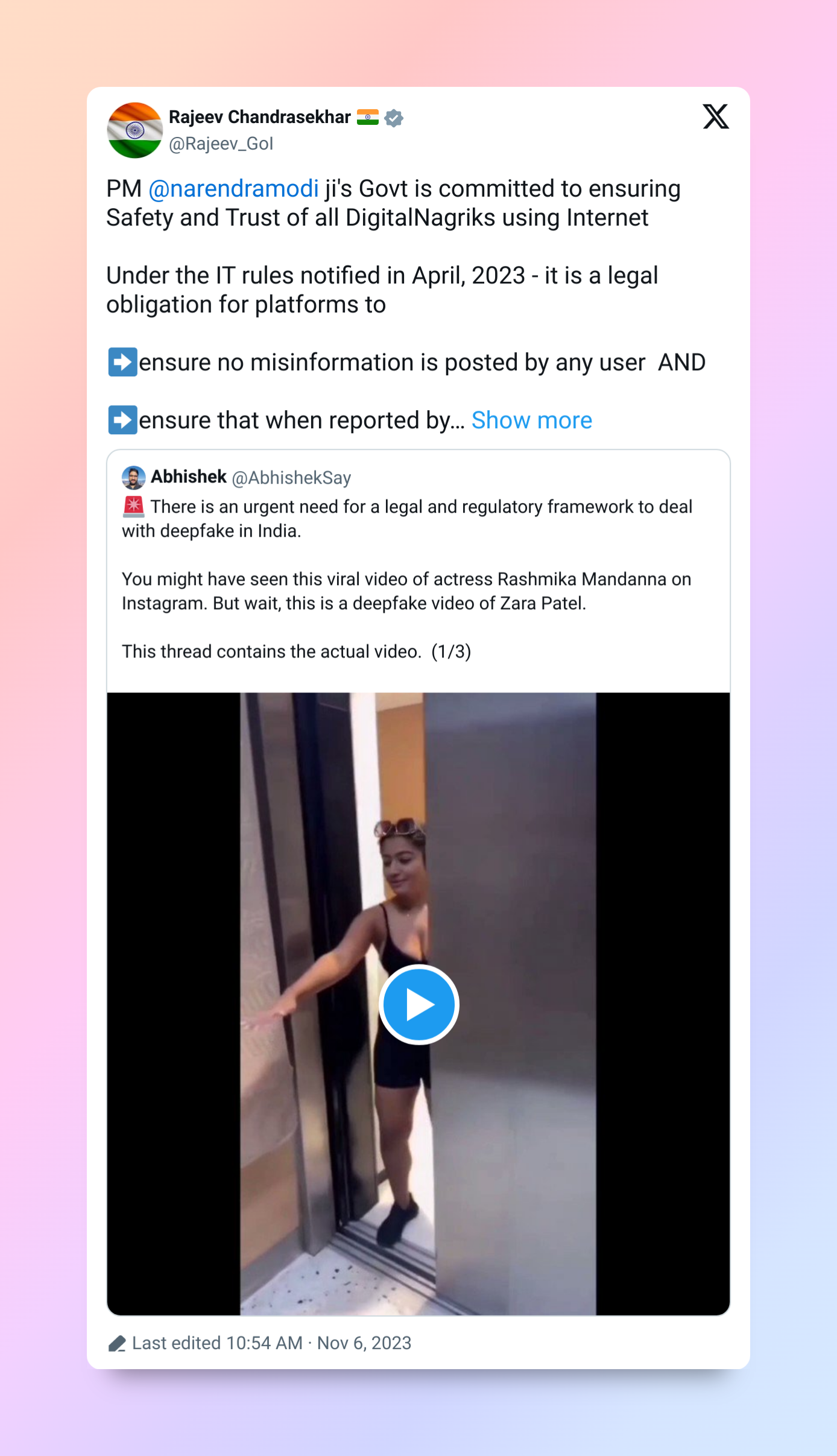
Image Credit: Minis
Union Minister Rajeev Chandrasekhar reacts strongly to 'deepfake' video targeting actress Rashmika Mandanna on social media
- Union Minister Rajeev Chandrasekhar strongly reacts to a "deepfake" video targeting actress Rashmika Mandanna on social media. He emphasizes that platforms are obligated to remove content violating India's IT rules.
- Chandrasekhar highlights that under the IT rules, misinformation must be removed within 36 hours upon reporting. Failure to comply may lead to legal action under rule 7, with platforms taken to court by aggrieved parties.
- The "deepfake" video involves digitally altering Rashmika Mandanna's face to mislead viewers. It falsely portrays her entering an elevator, while the original clip features social media influencer Zara Patel.
Read Full Article
22 Likes
Minis
1.1k

Image Credit: Minis
27-year-old vegetable vendor turns cyber scammer, earns Rs 21 crore in just 6 months by tricking people
- Rishabh Sharma, once a vegetable seller, turned to fraudulent work-from-home schemes after facing financial losses during the pandemic.
- In just six months, Rishabh managed to trick people out of a massive Rs 21 crore, becoming a central figure in 37 fraud cases across 10 Indian states and assisting in 855 other scams.
- Rishabh created a fake website resembling Marriott Bonvoy hotel's and offered fake job opportunities to write reviews, luring victims into investing more money with false promises.
- It is suspected that Rishabh might have collaborated with criminal groups from countries like China and Singapore to send the stolen money using secret methods.
Read Full Article
11 Likes
Minis
1.9k

Image Credit: Minis
Man posing as HR head of multinational company dupes HSBC bank of ₹2 crore
- An alleged fraudster posing as the HR head of a multi-national company duped HSBC Bank of over ₹2 crore by opening 38 salary accounts, obtaining 28 credit cards, and taking two loans.
- The accused presented fake employees as account holders, and money was credited as salaries into these accounts every month. However, no repayments were made for the credit cards or loans.
- The bank's investigation revealed that the money credited to these accounts was immediately withdrawn through debit cards, and the addresses and account holders' photographs were fake.
Read Full Article
29 Likes
Minis
1.3k

Image Credit: Minis
3 missed calls and your money is gone: Check how the 'SIM Swap' scam works
- SIM Swap scams are on the rise in India, where scammers aim to gain access to duplicate SIM cards to exploit personal data.
- A recent case involved a lawyer who lost money from her bank account after receiving three missed calls and without sharing any personal details or OTPs.
- Scammers use various tactics, including unusual browsing history, phishing links, and UPI registration texts, to obtain personal information.
- SIM Swap scammers aim to obtain personal data to collaborate with insiders at a mobile network and get a duplicate SIM card. This allows them unauthorized access to bank accounts and personal information.
Read Full Article
24 Likes
For uninterrupted reading, download the app