Cyber Security News
VentureBeat
64

Image Credit: VentureBeat
Patronus AI debuts Percival to help enterprises monitor failing AI agents at scale
- Patronus AI has launched Percival, a monitoring platform that automatically identifies failures in complex AI agent systems to address enterprise concerns about reliability.
- Percival is the first solution capable of detecting various failure patterns in AI agent systems, suggesting fixes, and optimizations automatically.
- The software can detect over 20 failure modes across four categories, offering benefits such as reduced debugging time for enterprises.
- The market for AI monitoring tools is expected to grow significantly as companies transition from experimental to mission-critical AI applications, and Patronus AI aims to cater to the enterprise AI safety market.
Read Full Article
3 Likes
Mcafee
299

Image Credit: Mcafee
Keep It Real: How McAfee Is Using AI to Fight AI—and End Scam Stigma
- McAfee launched a digital ad with a rotating head to showcase AI's ability to mimic reality using generative AI, blurring the line between real and surreal.
- The campaign aims to highlight the importance of tools like McAfee's Scam Detector in detecting sophisticated AI-based deceptions.
- Alongside the ad campaign, McAfee introduced Scam Stories to share real experiences of scams, partnering with FightCybercrime.org to help people recognize and recover from scams.
- The campaign is not just about raising awareness but also taking action by donating $50,000 worth of McAfee protection and expanding education efforts through the Online Safety for Kids initiative.
Read Full Article
17 Likes
Mcafee
59

Image Credit: Mcafee
Introducing Scam Stories: A McAfee Campaign to End Scam Stigma
- Actors Chris Carmack and Erin Slaver were scammed while trying to order patio cushions, leading them to share their story as part of the McAfee-led Scam Stories campaign.
- Scam Stories is a movement aimed at ending the stigma around being scammed, encouraging people to share their experiences, and educating the community on staying safe online.
- The campaign features real stories of individuals who've fallen victim to scams, highlighting the importance of scam awareness and sharing experiences to prevent others from being scammed.
- Partnering with FightCybercrime.org, McAfee is donating protection products and funds to support scam survivors and educate the public on cybercrime prevention.
Read Full Article
3 Likes
TechBullion
276

Image Credit: TechBullion
SecurityBridge Partners with Microsoft to Boost SAP Security
- SecurityBridge has partnered with Microsoft to integrate SAP data into Microsoft Sentinel, enhancing SAP security.
- The collaboration aims to provide improved visibility to detect and respond to threats across SAP landscapes effectively.
- Combining SecurityBridge's SAP-native cybersecurity platform with Microsoft Sentinel's capabilities makes complex SAP security events accessible and actionable for all security teams.
- The collaboration benefits SAP customers by leveraging Microsoft Sentinel's machine learning and SecurityBridge's SAP security insights to enhance threat identification and response capabilities.
Read Full Article
16 Likes
Mcafee
47
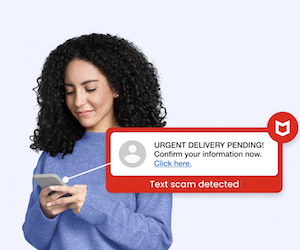
Image Credit: Mcafee
Introducing McAfee’s Scam Detector – Now Included in All Core Plans
- McAfee has introduced Scam Detector, advanced scam detection technology included in all core plans for customers in the U.S., UK, and Australia.
- Scam Detector is designed to detect scams in text messages, emails, and videos using AI-powered detection, educational guidance, and multi-platform coverage.
- Features include smarter text scam detection across messaging apps, AI-based scam analysis for email, deepfake detection for videos, on-demand scam check, custom sensitivity settings, and safe browsing layer.
- Privacy-focused Scam Detector utilizes on-device AI, and is included at no extra cost in McAfee's core plans without the need for additional purchases.
Read Full Article
2 Likes
Tech Radar
409

Image Credit: Tech Radar
SAP patches recently exploited zero-day in wake of NetWeaver server attacks
- SAP has patched a critical-severity zero-day vulnerability, CVE-2025-42999, in NetWeaver server.
- This vulnerability was chained with CVE-2025-31324, fixed in April, and poses a risk to Fortune 500 companies.
- The flaw allows a privileged user to upload content that could compromise confidentiality, integrity, and availability.
- Several firms observed attacks exploiting the vulnerability in which web shells were dropped on vulnerable servers.
Read Full Article
24 Likes
Tech Radar
322

Image Credit: Tech Radar
Extensive investment scam that stole €3 million tackled by Europol
- Europol, in collaboration with other agencies, has dismantled an organised crime group involved in an extensive investment scam.
- The group defrauded over 100 victims of a combined amount of €3 million through a fake online investment platform.
- The criminals used cyber trading and promised substantial profits to victims, convincing them to transfer more funds that were directly stolen by the group.
- The scam was reported by a couple in Germany, leading to the seizure of evidence, including documents, electronic devices, and cash, uncovering an extensive criminal network.
Read Full Article
19 Likes
Securityaffairs
377

Image Credit: Securityaffairs
Microsoft Patch Tuesday security updates for May 2025 fixed 5 actively exploited zero-days
- Microsoft Patch Tuesday security updates for May 2025 addressed 75 security flaws, including five zero-day vulnerabilities.
- Of the vulnerabilities fixed, 12 are rated Critical and the rest are rated Important in severity.
- Microsoft confirmed that five zero-day vulnerabilities were actively exploited in the wild, including issues related to Scripting Engine Memory Corruption and Elevation of Privilege in various Windows components.
- Microsoft urged users to apply the security updates to protect their systems from potential cyber attacks.
Read Full Article
22 Likes
Tech Radar
211

Image Credit: Tech Radar
Intel still vulnerable to Spectre data-leak vulnerabilities, researchers say
- Researchers from ETH Zurich found a way around Spectre mitigations on Intel.
- Intel released a microcode patch to address the vulnerabilities discovered.
- ARM and AMD chips are not affected by the newly identified vulnerabilities.
- The new vulnerabilities named Branch Prediction Race Conditions (BPRC) impact Intel products from the 7th to 9th generation CPUs.
Read Full Article
12 Likes
Wired
193

Image Credit: Wired
North Korean IT Workers Are Being Exposed on a Massive Scale
- North Korean IT workers from Laos and Russia, identified by researchers as 'Naoki Murano' and 'Jenson Collins,' raise money for North Korean regime through cyber activities.
- North Korea poses a severe cyber threat by stealing intellectual property, looting crypto, and employing IT workers to infiltrate companies.
- DTEX discloses North Korean cyber activity and publishes over 1,000 email addresses linked to North Korean IT workers.
- North Korean IT workers operate with a goal of funding the regime and developing weaponry, functioning like a crime syndicate.
- IT workers use stolen identities and false personas, primarily targeting multiple companies and tricking them into hiring them remotely.
- DTEX's report highlights the involvement of IT workers like Murano and Collins in crypto projects and revenue generation for Pyongyang.
- US government sanctions North Korean companies employing IT workers, highlighting the billions earned to fund the regime.
- As more North Korean IT workers are identified, they adapt tactics like face-changing software during interviews to evade detection.
- North Korean IT workers face close surveillance by the regime, are set earnings quotas, and operate through various military and intelligence organizations.
- IT workers generate income through various projects for North Korea, with some involved in AI organizations and revenue generation schemes.
Read Full Article
11 Likes
Global Fintech Series
331

Image Credit: Global Fintech Series
Using Technology to Plug the UK Finance Skills Gap
- The UK finance skills gap poses challenges for businesses striving for efficiency in financial processes and talent retention.
- Technology, such as business process automation, is essential to elevate finance professionals into strategic roles within organizations.
- Automating processes like accounts payable can eliminate late payments, errors, and enhance supplier relationships.
- Implementing powerful technology solutions leads to increased productivity and a more satisfying work environment for finance talent.
- Developing diversity, equality, and inclusion in finance teams can attract a wider talent pool and improve retention rates.
- AI and agentic AI are transforming financial operations, requiring finance professionals to acquire new skills in data analysis and AI understanding.
- Investing in effective technologies enables organizations to retain analytical finance talent and achieve greater profitability.
Read Full Article
19 Likes
Dev
174

Image Credit: Dev
Fine-Tuning SSL Protocols and Ciphers in SafeLine WAF
- SafeLine WAF allows full control over SSL protocols and cipher suites for securing web applications.
- You can configure SSL certificates, select supported protocol versions, and customize cipher suites based on security needs.
- Options include enabling HTTPS access by uploading SSL certificates, choosing SSL/TLS versions like TLSv1.3, and customizing cipher suites.
- SafeLine supports various encryption algorithms and configurations to ensure secure and optimized encryption tailored to specific environments.
Read Full Article
10 Likes
Hackernoon
87

Image Credit: Hackernoon
The 5 Lessons RSAC 2025 Forced Me to Learn About Modern Cybersecurity
- Attending RSA Conference 2025 provided a firsthand look at the transformation in the cybersecurity industry.
- The event showcased the overwhelming scope of cybersecurity, with over 400 exhibitors covering various aspects.
- Despite the industry's growth in response to increasing threats, vendors are shifting towards a deeper purpose of helping customers.
- AI played a prominent role at RSAC 2025, with a focus on practical applications rather than hype.
- The industry is witnessing a split between consolidating platform vendors and emerging specialized startups.
- Identity emerged as a crucial focus at the conference, with discussions on passwordless authentication and continuous profiling.
- The return to community and trust was highlighted, emphasizing the human aspect of cybersecurity alongside technology.
- The shift from 'fear-driven marketing' to 'trust-driven operations' signals a change in industry approach.
- In navigating this evolving landscape, clarity, ethics, and tangible impact are now paramount.
- The industry is called to deliver more transparency, effectiveness, and value to meet the demands of the modern cybersecurity landscape.
Read Full Article
5 Likes
Securityaffairs
4

Image Credit: Securityaffairs
Fortinet fixed actively exploited FortiVoice zero-day
- Fortinet has fixed a critical remote code execution zero-day vulnerability, CVE-2025-32756, actively exploited in attacks targeting FortiVoice enterprise phone systems.
- The vulnerability affects FortiVoice, FortiMail, FortiNDR, FortiRecorder, and FortiCamera, allowing remote unauthenticated attackers to execute arbitrary code via malicious HTTP requests.
- Threat actors exploiting the flaw scanned networks, erased crash logs, and deployed malware on compromised servers. They also added credential-stealing cron jobs and used scripts to scan victim networks.
- Fortinet recommends disabling the HTTP/HTTPS administrative interface as a workaround. The attackers were identified using several IP addresses and enabling the 'fcgi debugging' setting on compromised systems.
Read Full Article
Like
Pymnts
320

Image Credit: Pymnts
From Faked Invoices to Faked Executives, GenAI Has Transformed Fraud
- Generative artificial intelligence, including deepfakes and advanced voice synthesis, has revolutionized fraud in payments and cybersecurity.
- Cyberfraud using generative AI, such as deepfake videos and voice cloning, has become more prevalent and sophisticated, posing challenges for businesses to detect fraudulent activities.
- AI-driven attacks now involve impersonation of executives through deepfake technology, leading to increased instances of fraudulent fund transfers and cyber scams.
- To combat the rising threat of AI-driven fraud, businesses are adopting advanced fraud detection systems and emphasizing employee training and collaboration to enhance cybersecurity measures.
Read Full Article
17 Likes
For uninterrupted reading, download the app