Cyber Crime News
Kaspersky
0

Image Credit: Kaspersky
What an SMS blaster is, and how to protect yourself from malicious SMS messages while traveling | Kaspersky official blog
- Scammers use 'SMS blasting' to send fake text messages directly to victims' phones.
- SMS blasters exploit 2G vulnerabilities to mimic carrier signals and send malicious SMS.
- Protect yourself by disabling 2G connectivity or using comprehensive smartphone security systems.
- Avoid clicking on links in fake SMS messages and be vigilant against various scam tactics.
Read Full Article
Like
Digit
400

Image Credit: Digit
McDonald’s AI hiring bot leaks millions of job seeker’s details: Here’s what happened
- McDonald’s experienced a security breach in its AI-powered chatbot hiring system, exposing the personal details of around 64 million job applicants.
- The breach, discovered in the McHire platform developed by Paradox.ai, revealed critical flaws in the system's security, including default login credentials and a vulnerability that allowed unauthorized access to sensitive applicant data.
- Security researchers uncovered the breach by exploiting an insecure direct object reference (IDOR) vulnerability, accessing applicant data like names, emails, phone numbers, and chat logs with the AI chatbot.
- Following the discovery, McDonald’s and Paradox.ai swiftly patched the vulnerabilities, replacing default credentials with secure protocols. The incident underscores the risks of lax security in AI systems and highlights the need for robust cybersecurity measures in the age of automation.
Read Full Article
18 Likes
Medium
32

Image Credit: Medium
Inside a Hacker’s Mind: The Dark Tricks Behind Phishing Emails
- Phishing emails rely on psychology rather than sophistication to trick recipients into giving away sensitive information.
- The phisher meticulously crafts the email to exploit trust and urgency, using familiar sender addresses and urgent subject lines to trigger panic.
- To hook the recipient, the email body is designed to mimic a legitimate website, creating a sense of familiarity and scarcity to persuade the target to click on the malicious link.
- The article provides an insight into the tactics used by hackers to manipulate individuals into falling for phishing emails and highlights the importance of cybersecurity awareness.
Read Full Article
1 Like
TronWeekly
40

Image Credit: TronWeekly
GMX Halts V1 Trading After $42M Crypto Hack Hits Arbitrum Liquidity Pool
- GMX experienced a $42 million crypto hack on its V1 GLP pool on Arbitrum due to a logic flaw.
- The attacker converted stolen funds to ETH, DAI, and other tokens and bridged them to Ethereum.
- To recover funds, GMX offered a 10% bounty and halted V1 trading while investigating the exploit.
- The security breach led to GMX suspending V1 trading, GLP minting, and redemption to prevent further risks.
Read Full Article
2 Likes
Securityaffairs
101
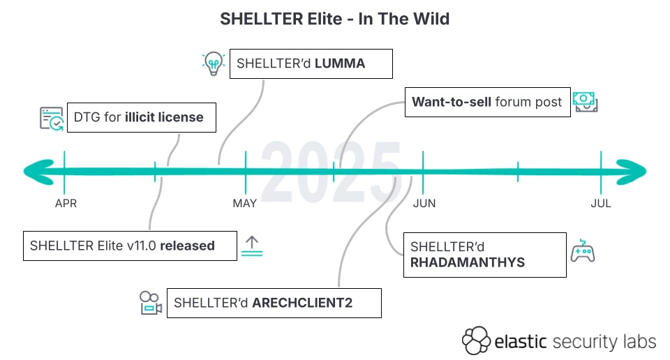
Image Credit: Securityaffairs
Hackers weaponize Shellter red teaming tool to spread infostealers
- Hackers exploit leaked Shellter Elite copy for infostealer attacks, bypassing security measures.
- Elastic Security Labs identifies malware campaigns using Shellter for evasion and malware deployment.
- Dynamic unpacker released by Elastic to detect and analyze SHELLTER-protected malware more effectively.
- Threat actors adopt Shellter for infostealer attacks, prompting efforts to counter abuse.
Read Full Article
6 Likes
Securityaffairs
308

Image Credit: Securityaffairs
Security Affairs newsletter Round 532 by Pierluigi Paganini – INTERNATIONAL EDITION
- McDonald’s job app exposes data of 64 million applicants
- Russian basketball player accused in U.S. ransomware case
- UK NCA arrests four people over M&S, Co-op cyberattacks
- PerfektBlue Bluetooth attack allows hacking infotainment systems of Mercedes, Volkswagen, and Skoda
Read Full Article
17 Likes
Securityaffairs
324

Image Credit: Securityaffairs
Athlete or Hacker? Russian basketball player accused in U.S. ransomware case
- Russian basketball player Daniil Kasatkin, 26, was arrested in France at the request of the U.S. over alleged ties to a ransomware group targeting U.S. companies and federal entities.
- Kasatkin is suspected of aiding a ransomware group that targeted over 900 entities from 2020 to 2022, allegedly helping negotiate ransoms.
- Despite the accusations, Kasatkin denies all charges, with his lawyer claiming he lacks the technical skills for such involvement, having minimal computer knowledge.
- The athlete's lawyer unsuccessfully requested his release, citing health and career concerns, with Kasatkin experiencing weight loss in detention and feeling unsafe amidst the Russia-Ukraine conflict.
Read Full Article
19 Likes
TechCrunch
244

Image Credit: TechCrunch
CISA warns hackers are actively exploiting critical ‘Citrix Bleed 2’ security flaw
- CISA warns that hackers are actively exploiting a critical 'Citrix Bleed 2' security flaw in Citrix NetScaler.
- The bug allows hackers to remotely extract sensitive credentials from an affected NetScaler device, potentially gaining broader access to a company's network.
- CISA has evidence of active exploitation and ordered federal government agencies to patch affected Citrix devices within a day due to the significant risk posed.
- Citrix has not acknowledged the exploitation but advises customers to update affected devices promptly.
Read Full Article
14 Likes
Guardian
102
Image Credit: Guardian
Louis Vuitton says UK customer data stolen in cyber-attack
- Louis Vuitton's UK customer data has been stolen in a cyber-attack, making it the latest victim of hackers.
- An unauthorized party accessed the UK operation's systems and obtained names, contact details, and purchase history, but no financial data was compromised.
- Louis Vuitton notified customers of the breach, warning of potential phishing, fraud, or unauthorized use of information.
- Recent arrests were made in connection with cyber-attacks on Marks & Spencer, the Co-op, and Harrods, highlighting the increasing threat of cybercrime to retailers.
Read Full Article
6 Likes
Securityaffairs
135

Image Credit: Securityaffairs
UK NCA arrested four people over M&S, Co-op cyberattacks
- UK NCA arrests 4, including 3 teens, linked to cyberattacks on M&S, Co-op, and Harrods.
- Arrested individuals seized in London and West Midlands for Computer Misuse Act offenses.
- Suspects face charges of blackmail, money laundering, and organized crime participation.
- Attacks caused major disruptions and financial losses for affected businesses.
- DragonForce group behind attacks, stealing data and demanding ransom from victims.
Read Full Article
8 Likes
Securityaffairs
318

Image Credit: Securityaffairs
Qantas data breach impacted 5.7 million individuals
- Qantas confirmed data breach impacted 5.7 million customers via third-party platform.
- Hackers accessed a call centre platform stealing names, emails, phone numbers, birth dates.
- Qantas assures no financial data or passwords were affected in the incident.
- Approximately 5.7M unique customers impacted; no credit card or passport info accessed.
- Qantas now contacting affected customers to inform them and offer necessary support.
Read Full Article
19 Likes
Medium
56

Image Credit: Medium
Protecting Your Business from Cyber Attacks in Saudi Arabia
- E-commerce, fintech, healthcare, and smart infrastructure growth in Saudi Arabia has led to cyber threats.
- Attacks include APTs with covert backdoors, ransomware, supply chain breaches, and insider risks.
- Key defenses involve network segmentation, EDR, web/email security, IAM, SIEM, and customized implementations.
- Robust cybersecurity measures, aligned with NCA standards, are vital for businesses in Saudi Arabia.
- Promoting cyber resilience requires training, incident response plans, leadership support, and third-party risk management.
Read Full Article
3 Likes
Moneyweb
72

SA earns top spot as target for cyber attacks
- South Africa is identified as a prime target for cyber attacks.
- Interpol's Africa Cyberthreat Assessment Report highlights the country's vulnerability.
- Major financial institutions and businesses are key targets for cyber criminals in SA.
- Emphasis is placed on the need for better cybersecurity measures nationwide.
- Factors like geopolitics and AI advancements play a role in escalating cyber threats.
Read Full Article
4 Likes
Securityaffairs
98

Image Credit: Securityaffairs
Nippon Steel Solutions suffered a data breach following a zero-day attack
- Nippon Steel Solutions, a subsidiary of Japan’s Nippon Steel, reported a data breach caused by hackers exploiting a zero-day vulnerability in their network equipment.
- The breach led to unauthorized access and potential leaks of personal data of customers, partners, and employees, but cloud services remain unaffected.
- Compromised information includes customer names, company details, employee names, and business-related contact information.
- The company has notified affected parties, cooperated with authorities, and implemented security measures to address the breach. There is no evidence of leaked data on social media or the dark web.
Read Full Article
5 Likes
Securityaffairs
247
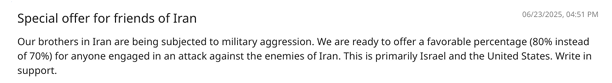
Image Credit: Securityaffairs
Iranian group Pay2Key.I2P ramps Up ransomware attacks against Israel and US with incentives for affiliates
- The Iranian ransomware group Pay2Key.I2P has increased its attacks on U.S. and Israeli targets, offering affiliates higher profits.
- Pay2Key.I2P, linked to the Iran-nexus APT group Fox Kitten, now operates as a ransomware-as-a-service outfit.
- The group has secured over 51 ransom payouts in four months and expanded its reach by launching a Linux version of their ransomware.
- U.S. cybersecurity agencies have warned of rising cyber threats from Iranian state-linked hackers, urging organizations to enhance their defenses.
Read Full Article
14 Likes
For uninterrupted reading, download the app