Info. Security News News
Sentinelone
335

Image Credit: Sentinelone
The Good, the Bad and the Ugly in Cybersecurity – Week 37
- Singaporean authorities conducted an island-wide raid on various suspects that were being monitored for their links to a global cybercrime syndicate.
- Two individuals have been indicted in the U.S. for their alleged involvement in managing a dark web marketplace known as WWH Club.
- Crypto took a major hit last year with losses exceeding $5.6 billion.
- The report laid out several fraud and scam trends, ranging from fake investment sites, pig butchering schemes linked to dating apps and professional networking platforms, and liquidity mining scams that offer high returns for staking assets.
- Iraqi government entities have been targeted in a sophisticated campaign led by OilRig (aka APT34), an Iranian state-sponsored threat group.
- OilRig introduced two new malware strains, Veaty and Spearal, designed to execute PowerShell commands and extract sensitive files.
- Spearal, a .NET backdoor, uses DNS tunneling for communication, while Veaty relies on compromised email accounts for its command-and-control (C2) operations.
- The campaign targeting Iraqi government infrastructure also involved the discovery of additional backdoors, such as CacheHttp.dll, that targets Microsoft’s Internet Information Services (IIS) servers.
- Advanced persistent threats (APTs) like OilRig continue to develop specialized techniques in maintaining C2 channels to further develop elaborate cyber-espionage campaigns against high-value adversarial targets.
- Latest findings published by the FBI’s Internet Crime Complaint Center (IC3), the product of almost 70,000 reports, marks this 45% rise as a new record high for the industry.
Read Full Article
20 Likes
Securityintelligence
381

Image Credit: Securityintelligence
What can businesses learn from the rise of cyber espionage?
- Rival nation-states and the organizations loyal to them are increasingly turning to cyber espionage to gain a strategic advantage.
- Long gone are the days when standalone criminals are the greatest threat. Now the greater threat comes from nation-states and large enterprises that have capitalized on the opportunities of digital espionage.
- The combination of AI and increasingly massive amounts of data means business strategy can be decided in hours and days rather than months, making AI a necessity even in the world of cyber crime and espionage.
- State-sponsored attackers are already using tools like large language models (LLMs) to scale, inform, and enhance their attacks, making AI a force multiplier in the broader threat landscape.
- Organizations must proactively protect against cyber espionage by layering on a zero trust architecture, conducting regular security audits, and ensuring all sensitive information is encrypted regardless of where it resides.
- Businesses need to continuously monitor, review and update their security systems, and layering on AI has become necessary thanks to its ability to augment real-time threat detection and response capabilities.
- No business will ever be immune to cyberattacks, but the greatest risk comes with a failure to innovate. Businesses need to strike the right balance by incorporating AI strategically as a tool to protect against the next generation of state-sponsored cyber threats.
Read Full Article
22 Likes
Socprime
312

Image Credit: Socprime
RansomHub Ransomware Detection: Attackers Exploits Kaspersky’s TDSSKiller to Disable EDR Systems
- RansomHub Ransomware group is exploiting Kaspersky's TDSSKiller software to disable EDR systems.
- Attackers use TDSSKiller to bypass defenses and then utilize the LaZagne tool to extract login details.
- The FBI, CISA, and partners have warned of increasing RansomHub Ransomware activity.
- To prevent EDR system disablement, experts recommend enabling tamper protection and monitoring for specific parameters.
Read Full Article
18 Likes
Hackingblogs
408
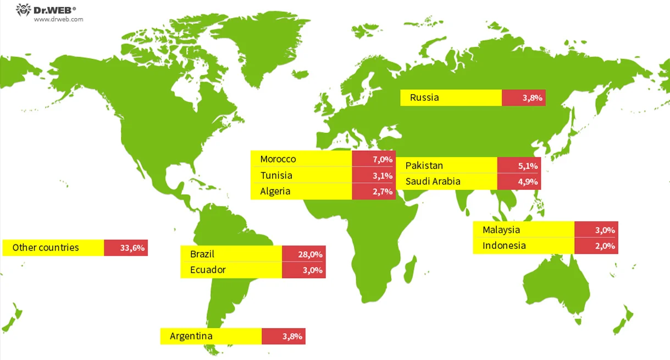
Image Credit: Hackingblogs
Critical Alert: New Vo1d Malware Hits 1.3 Million Android TV Boxes Worldwide
- Cybersecurity specialists at Doctor Web have discovered a new Vo1d backdoor malware campaign targeted at Android-based TV sets.
- Over 1.3 million Android TV streaming boxes have been infected with the Vo1d malware, giving attackers complete access to the compromised devices.
- The majority of infected devices were found in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
- The malware exploits vulnerabilities in older Android versions running on these TV boxes, taking advantage of the lack of security software installed on them.
Read Full Article
24 Likes
Securityaffairs
229
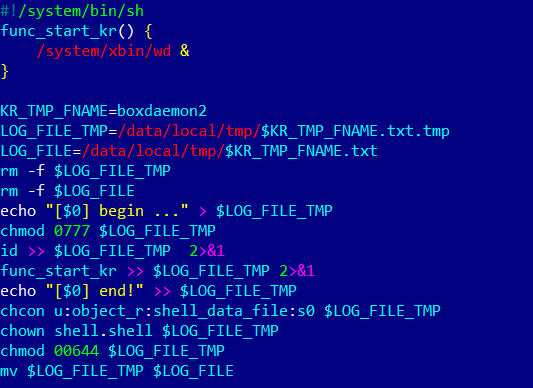
Image Credit: Securityaffairs
Vo1d malware infected 1.3 Million Android-based TV Boxes in 197 countries
- Researchers uncovered an Android malware, dubbed Vo1d, that has already infected nearly 1.3 million Android devices in 197 countries.
- The malware, Vo1d, acts as a backdoor, allowing attackers to download and install third-party software covertly.
- The infections were geographically distributed, with the highest number of infections reported in Brazil, Morocco, Pakistan, Saudi Arabia, and other countries.
- Targeting Android-based TV boxes with outdated software versions and unpatched vulnerabilities, attackers exploit users' belief that these devices are more secure than smartphones.
Read Full Article
13 Likes
Salesforce
64

Image Credit: Salesforce
Data Privacy Pitfalls? Not With These 5 Steps to Compliance Success
- As organizations dive into deeper customer relationships and personalized experiences, organizations face growing pressure to protect individual privacy rights while navigating an increasingly complex regulatory landscape.
- Proper data classification is crucial for effective data management and protection.
- Audit your access controls and update access permissions based on employee roles, data sensitivity, and regulatory requirements.
- By anonymizing or pseudonymizing sensitive information, organizations can simulate real-world scenarios without compromising individuals’ privacy rights.
- Tracking and logging user activities can spot anomalies and respond quickly to potential security issues.
- Implementing data minimization ensures you collect and retain only the essential data, reducing the impact of potential breaches.
- For instance, Privacy Center is a suite of data management tools built to help you manage components of data privacy laws.
- With the right tools and practices in place, you’ll maintain a classified, permission-minimized, and secure data environment, ready to tackle data privacy compliance with confidence.
- By strengthening privacy and compliance frameworks, businesses can build trust with consumers and reduce legal risks and potential fines.
- Good AI needs good data and data privacy compliance becomes a critical part of that strategy.
Read Full Article
3 Likes
Securityaffairs
18

Image Credit: Securityaffairs
Cybersecurity giant Fortinet discloses a data breach
- Cybersecurity giant Fortinet disclosed a data breach after a threat actor claimed the theft of 440GB of files from the company’s Microsoft Sharepoint server.
- A threat actor gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive.
- Fortinet confirmed that the incident did not result in malicious activity affecting any customers or their operations.
- The number of impacted customers and the potential impact on the Australian federal government or critical infrastructure remain undisclosed.
Read Full Article
1 Like
Securityaffairs
317

Image Credit: Securityaffairs
UK NCA arrested a teenager linked to the attack on Transport for London
- U.K. police arrested a 17-year-old teenager allegedly linked to the cyberattack on London’s public transportation agency, Transport for London.
- The arrest was made by the U.K. National Crime Agency (NCA) on suspicion of Computer Misuse Act offences.
- Transport for London (TfL) is investigating the cyberattack that occurred on September 1.
- The agency confirmed that customer data, including names, contact details, and addresses, may have been accessed in the breach.
Read Full Article
19 Likes
Dataprivacyandsecurityinsider
423

Russian Military Cyber Actors Targeting Critical Infrastructure Sector
- Russian military cyber actors are targeting critical infrastructure sectors, government services, financial services, transportation systems, energy, and healthcare sectors of NATO members.
- Unit 29155, a cyber group affiliated with the Russian military, is responsible for data collection, espionage, reputational harm, and systematic sabotage.
- The FBI has detected over 14,000 instances of domain scanning and website defacements by Russian cyber actors.
- To mitigate the threat, organizations are advised to prioritize system updates, segment networks, and enable phishing-resistant multifactor authentication.
Read Full Article
25 Likes
Dataprivacyandsecurityinsider
257

The Push for Warning Labels on Social Media Platforms, States Attorneys General Urge Lawmakers to Take Action
- Lawmakers and Attorneys General are pushing for warning labels on social media platforms to alert users of potential risks to children.
- There are concerns about cyberbullying, harassment, eating disorders, and suicidal thoughts among children using social media platforms.
- U.S. Surgeon General Vivek Murthy advocates for tobacco-style warning labels on social media to address the harm they can cause to children's mental health.
- The push for warning labels is challenged by tech industry groups and free-speech advocates.
Read Full Article
15 Likes
Dataprivacyandsecurityinsider
174

Lehigh Valley Health Network Settle Class Action Case for $65M
- Lehigh Valley Health Network (LVHN) has agreed to settle a class action case for $65 million.
- The settlement relates to a ransomware attack in February 2023 that compromised personal information of patients.
- The stolen information included medical and treatment records, health insurance details, and potentially sensitive data like social security numbers and banking information.
- The settlement, if approved by the court, will provide compensation ranging from $50 to $70,000 to each class member.
Read Full Article
10 Likes
Dataprivacyandsecurityinsider
55

Members of International Sextortion Ring Charged for Stealing $2M From Victims
- Four Delaware men have been charged with an international sextortion and money laundering scheme.
- They targeted thousands of victims across the United States, Canada, and the United Kingdom.
- The men posed as young females online and extorted approximately $1.9 million from victims through CashApp and Apple Pay.
- They threatened to distribute explicit images unless victims paid them.
Read Full Article
3 Likes
Dataprivacyandsecurityinsider
450

Privacy Tip #413 – NIST Releases Recommendation for Consumer Routers
- The National Institute of Standards and Technology (NIST) has issued recommendations for securing home routers.
- The publication emphasizes the importance of router security in the context of smart homes, IoT devices, and remote work.
- A compromised router can lead to unauthorized access, information dissemination, and malicious attacks on connected devices.
- The NIST recommends setting strong, unique passphrases for home routers instead of using default passwords.
Read Full Article
27 Likes
Sentinelone
413

Image Credit: Sentinelone
From Amos to Poseidon | A SOC Team’s Guide to Detecting macOS Atomic Stealers 2024
- Amos Atomic is one of the most successful malware-as-a-service (MaaS) offerings that primarily targets Mac users, and it has evolved and expanded into several other malware options.
- What distinguishes the current family of these Malware-as-a-service providers from those which have targeted Apple's desktop operating system in the past is their highly sophisticated distribution methods, which target a broad range of enterprise applications instead of being restricted to cracked games and user productivity apps.
- These Atom InfoStealer variants come with different file characteristics, with some being written in Go, Objective-C, and C++, among others.
- Among the most prevalent variants of these stealer families found throughout 2024 are Banshee, Cthulu, Poseidon, and RodrigoStealer.
- Many of these variants have taken various approaches to obscuring the code, such as base32 encoding, hex-encoded strings, pulling 2nd-stage AppleScript files from remote servers, and chunk-splitting strings.
- Some of the characteristics of different types of these atomic stealer variants have been documented in the post, with evidence of capsule strings and RC4-encoded hex strings to obfuscate AppleScript commands and C2 URLs for fetching payloads.
- Users are tricked into allowing permissions and giving away their admin passwords for the system via the use of various AppleScript dialogs.
- Organizations without enterprise security systems are urged to review the indicators of compromise offered through the post to keep their systems protected.
- SentinelOne detects all variants of the atomic stealer through a multi-engine platform that combines static and dynamic Artificial Intelligence; both are aimed at stopping the threats pre-execution and on-execution.
- The post cautions that despite how unprecedented the number of variants of the atomic stealer is on the macOS malware scene, it is not the only infostealer currently visiting unsuspecting users in the wild.
Read Full Article
24 Likes
Amazon
363

Image Credit: Amazon
New whitepaper available: Building security from the ground up with Secure by Design
- Developing secure products and services is imperative for organizations looking to strengthen operational resilience and build customer trust.
- A whitepaper titled 'Building Security from the Ground up with Secure by Design' explores the concept of Secure by Design (SbD) and its importance in mitigating vulnerabilities early.
- Key considerations in implementing SbD include integrating it into the software development lifecycle, supporting it with automation, and applying it to artificial intelligence.
- The whitepaper details five key action items that can help organizations adopt a Secure by Design approach and build secure products.
Read Full Article
21 Likes
For uninterrupted reading, download the app